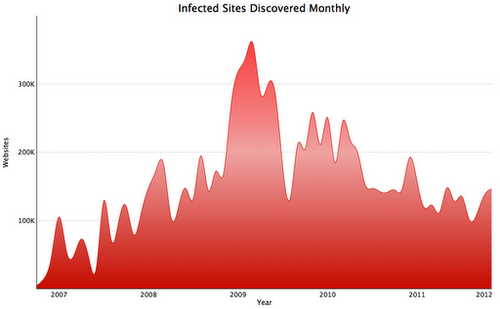
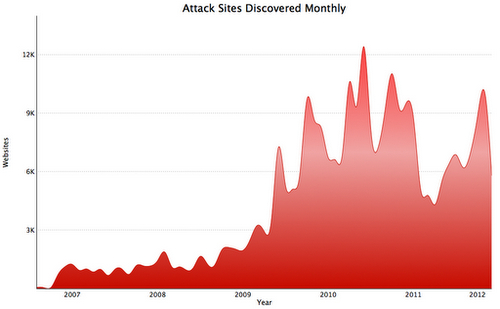
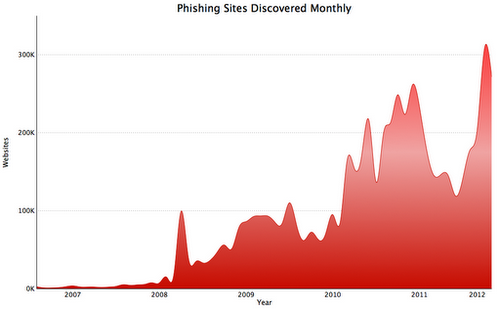
Comment The British government is keen for more public data and private transactions with taxpayers to be pushed online at precisely the same time as the Home Secretary demands more powers for security services to effectively snoop on communications traffic with the help of telcos and social networks.
Add to that the fact that spooks are constantly trying to interrupt encrypted sites that – they argue – are used by organised criminals and terrorists.
Then factor in the European Commission’s vice president Viviane Reding’s efforts to convince the EU parliament to pass a new data protection law because she and many others believe that the one written in 1995 is out of date.
Reding has repeatedly reminded audiences of computer academics and internet players, whom she has lobbied hard with her draft DP bill, that Facebook founder Mark Zuckerberg was only 11 when the previous legislation came into being.

Viviane Reding continues to lobby for rewrite of Euro data protection law
Indeed, that justification for overhauling the law was bandied around again by the Brussels’ justice commissioner earlier this week when she was speaking at the inaugural Digital Enlightenment Forum in Luxembourg.
Google, she added, was in 1995 still three years away from being incorporated and its young execs were still working in a garage office in California.
Reding’s views were met, in the main, with a positive response from the gathered crowd, many of whom expressed a sense of the digital world moving too fast.
This shifting sands attitude was pervasive at the event in which many experts on the topic of data protection and online identity were in agreement that legislation needs to happen, and that it needs to happen quickly.
The word “enlightenment” was somewhat cringingly used to help explain that sense of urgency. Some considered that we are in fact living through a kind of Enlightenment 2.0 – with the engine behind that apparent radical change in thinking being the internet and how society operates on it.
Facebook’s dominant social data farm has seemingly proved to be the trigger for many of these thinkers.
Google – a startup born in the late 90s that became the world’s biggest ad broker with billions of dollars of revenue – never got the sort of attention in Luxembourg this week that was lavished on data hoarder-extraordinaire, Facebook, with its modest sales garnered from an ad business model that still looks amateurish compared with that of Google’s.
And many experts in the field of identity couldn’t help but look on in awe at Zuck’s vast 900-million-people-strong siloed estate.
Some contended that a new “social contract” was required that would put the user in charge of accountability when it comes to what data is stored online.
It’s precisely the kind of contract that the UK’s Cabinet Office is mulling over as part of its proposals to farm out the handling of taxpayers’ online identities to the private sector.
A move which, as the Reg has previously reported, would eventually require primary legislation and regulations implemented in the same way that banks are scrutinised.
Some of the proposals the Cabinet Office has put forward were aired at the forum – that included holding up the principles of user control, transparency, governance, certification and, among other things, portability.
Portability is of course a concept that Facebook does not approve of. It has long held on to its users’ data and declined to let the likes of Google tap into that information. The recently floated company does allow its users to take chunks of their data with them if they choose to leave the social network, but that data does not easily flow into competing websites.
What was fascinating at this conference was the fixation, not with Google or even Microsoft – a company behind, for example, the previous UK government’s online “gateway” system for taxpayers to access services online – but with that of upstart Facebook.

Zuck continues to dig deep for ad revs
Perhaps that’s not unreasonable given how many people are sharing their lives on Facebook. Zuckerberg has previously floated the smug notion that his userbase could be considered the world’s third largest country.
Indeed, it has done what others including Google have failed to do – amass fine-grained, near real-time data that ought to be an advertiser’s dream come true.
One speaker at the event naively likened today’s social networks to US analogue television broadcasters of the 1950s and 1960s because TV audiences back then understood the commercial contract involved. Of course, that relationship was arguably much more benign than the interplay of Facebook with our lives today.
But making Facebook a major catalyst for an overhaul of European data protection law that many might hope will be expected to stand up to the tests of time better than the one written in 1995 could yet prove to be a huge, short-sighted error. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2012/06/20/data_protection_the_facebook_effect/