A tip-off from a source has turned up an interesting quirk in Facebook’s security measures. He claims the social networking site appears to discriminate against log-ins from Africa.
Our tipster, Raj from Vancouver, Canada, has an interesting if unusual set of circumstances.
Raj runs a tech business and uses Facebook to connect with customers. But because he appreciates getting round-the-clock coverage and because he doesn’t want to spend all his time updating Facebook, he has employed freelancers in Singapore, India and most recently Kenya to sign in and update his profile for him.
He could use a Page or a Group. But Raj is using a personal profile for this venture and in order to let his freelancers access his account, he shares his password with them.
And the problem? Raj’s employees in Singapore and India were both able to log in and work for him, but Sam – Raj’s Kenyan employee logging in from Nairobi – was blocked so many times by Facebook security checks he was unable to do his work. This became a problem to the extent where Raj was considering employing someone else in a different country who woulddn’t have the same problems logging in.
Raj is in a funny situation here: not many Westerners hire Kenyans to update their personal pages for them… But it’s exactly the unusual circumstances of Raj’s case that has brought this particular Facebook quirk to light.
To go into a little more detail: the log-ins from India and Singapore were challenged – once – and accepted by Raj on a particular computer back in Vancouver that Facebook recognised. The challenge screens look like the one below. However, the Nairobi log-in was challenged and accepted four times in a row before Raj gave up on trying to get the Kenyan log-ins accepted permanently and engineered a workaround by setting up a VPN so that Sam’s IP address matched his in Vancouver and lost the Kenyan connotations that seemed to be causing Facebook so many problems.
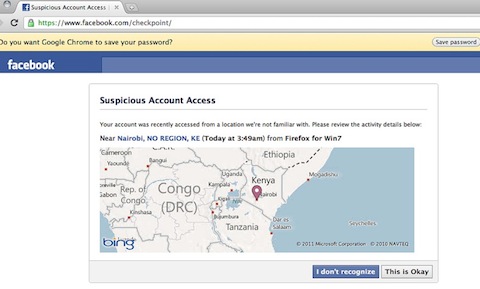
Raj wrote about the annoyance that the hyper security checks caused:
On four (4) separate occasions this week, Facebook temporarily locked us both out of my account. This has not only repeatedly disrupted my authorisations from other applications and social media work, klout, Facebook messenger (now a vital communication piece), and Microsoft Outlook integration, but it’s sucked a bunch of my time up, too! It seems only I can unlock my account from my office computer, so poor [Kenyan employee Sam] sits idle at night and then has to wait for me to come to the office in the morning to unlock the accounts. Can you say annoying? After jumping through Facebook’s little hoop four times, all I can say is can you get the hint, Facebook?
It’s good that Facebook challenge log-ins from unfamiliar places. Goodness knows we give it enough stick for not protecting our security. But why did it accept Raj’s confirmation of log-ins in Singapore and not the ones in Nairobi?
In a statement to The Register, Facebook admitted that it is more likely to block or question log-ins from geographical areas it considers suspicious.
A Facebook spokesperson told us:
We verify log-ins security based on the likelihood of a log-in from that geographic area being erroneous. If we spot a lot of suspicious activity from a particular IP address or area, we’ll take steps to make doubly sure that log-ins from that location are valid. If you log on from a new location, device, or we are wary of the browser you use, we’ll use additional security checks.
As Raj put it, before he figured out the VPN workaround: “I’d hate to turn him [Sam] to the door because of a social network that won’t let me inherently trust a whole country or ISP.”
In an informal briefing with Facebook the company hammered home the point that you should never, ever, according to article 4.8 of the Facebook TCs share your password with another person.
But people share passwords: couples do it, friends do it, people who run events or businesses do it too.
Officially, a Facebook spokesperson told us:
If you log on from a new location, device, or we are wary of the browser you use, we’ll use additional security checks. Doing so is a responsible way of keeping our users’ information safe and secure; it isn’t discrimination. Furthermore, this issue could be resolved by the user having multiple admins using their own profiles to manage a Facebook page rather than a profile. It is against our terms to allow more than one person access to an individual profile.
So this is profiling: the same as airport security guards choosing to search an Arab man rather than a white woman, or cops in Brixton searching a disproportionate number of black male teenagers – but in this case it was on the verge of costing a man his job.
Of course Raj could set up a Page. However there are several advantages to having a Profile on Facebook. It’s possible to convert a Profile into a Page and to save your contacts – people who were “friends” with you will automatically switch to becoming “fans” of your page. But photos and contacts are the only two things transferred over, so other content such as past updates, wall-to-wall conversations and messages will be lost.
Raj mentions that he uses Facebook instant chat to talk to clients and chat is not available to Page-owners. Generally, as a personal profile you can access a lot more information about the people you are connected to, and as a Page you can only see their public information and can’t for example write on their walls.
Facebook is very clear that there should be a distinction between businesses and people, but as Raj is aware there are some uses to being a person with friends rather than a Page with fans. The disadvantage is that Facebook might terminate you and your Facebook activity. That’s in their terms and conditions too. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2011/09/14/facebook_africa_log_ins/
