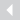WhatsApp image showing drug dealer’s fingerprints leads to arrest
A dealer had some Class A drugs to sell.
So he sent out an advertisement for ecstasy on WhatsApp. White, blue, yellow, red: they looked like candy in the photo, sealed in plastic, held out for display on his palm.
Smart drug dealer, right? Much to the chagrin of law enforcement, WhatsApp encrypts messages end-to-end. That means all messages: calls, photos, videos, file transfers and voice messages.
But the pill pusher didn’t consider that his message might end up on a seized phone in the hands of the police. Not did he likely consider a certain piece of evidence captured in that photo: his fingers.
In what the BBC calls a first for police in Wales, the image of a fingerprint helped to identify the man and to bring down an extensive drug-selling ring that could turn out to be larger still as the investigation continues.
Dave Thomas, of South Wales Police’s scientific support unit, called the work “groundbreaking.” He said that the WhatsApp photo helped to secure 11 convictions and to bring down the drug ring’s supply chain.
The middle and bottom part of a couple of fingers were just about visible under the bag of tablets in the image. In a video interview filmed by the BBC, Thomas pointed to the photo to describe how the imaging work was done:
Through some work done by our imaging unit, we enhanced what we could see on here. We did some inverting of the marks, [and] we then looked at the scale, which was another problem for us. We didn’t have a scale. Eventually we came from that with a suspect – main file fingerprints – and we compared them directly against this part of the mark which we could then search and identify the individual, which resulted in a number of arrests and a number of jail terms.
Thomas told the BBC that police are now looking more closely at the photos found on seized phones, in case they too might lead to evidence.
Of course, there’s nothing new about using fingerprints to identify criminals, Thomas said. The only new wrinkle is doing it through social media-shared photos:
[Fingerprinting] is an old-fashioned technique, not new. Ultimately, beyond everything else, we took a phone and looked at everything on it – we knew it had a hand with drugs on it. [Drug dealers] are using the technology not to get caught, and we need to keep up with advancements.
As it is, he said, 80% of people now own mobile phones. Besides telltale social media postings, many of those phones are used to purposefully record incidents the police may wind up investigating, be they fights or accidents. Then too, phones offer police evidence regarding their owners’ whereabouts via location data: evidence coming from cell towers that crooks often overlook.
Thomas:
We want to be in a position where there is a burglary at 20:30, we can scan evidence and by 20:45 be waiting at the offender’s front door and arrest them arriving home with the swag.
That will work through remote transmission – scanning evidence at the scene and sending it back quickly for a match.
It’s the future. We are not there yet but it could significantly enhance the ability of the local bobbies to arrest people very quickly.
The WhatsApp drug dealer turned out to be one member of a family business. The prints led to Elliott Morris, 28, of Redditch, Worcestershire, who’s been sentenced to 8.5 years for conspiracy to supply cannabis. His father, Darren, was sentenced to 27 months, and his mother, Dominique, received 12 months.
Police were initially tipped off when neighbors complained about a large number of visitors going to a separate address from that of the Morrises. In August 2017, police raided the address and found a large amount of cannabis, cash, and a “debt” list of people.
Five men were arrested, including one whose phone held WhatsApp and other social media messages about drug sales being sent out from the area. That led officers to Elliott Morris’s parents – Darren, 51 and Dominique, 44. They found that the family was running a “cannabis factory” at their home.
Also on the seized phone, they found the photo with the fingers.
Detective Inspector Dean Taylor told the BBC that even after staff at the scientific support unit increased the size and improved the clarity of the image, they still couldn’t find a match in a national fingerprint database. However, the BBC notes, when police fingerprint offenders, they take prints of the top part of their fingers, only occasionally getting the middle and bottom parts.
The elder Morrises’ prints didn’t match what officers found in the ecstasy photo. But they did match those of their son, Elliott, whom officers found in what Taylor described as a “rural log cabin hide-out.” That’s where they also found a second cannabis factory, as well as some very familiar looking ecstasy tablets.
Elliott was the main operator of the operation, so he got a stiffer sentence. Police are continuing the investigation, which has also identified £20,000 ($28,673) worth of Bitcoin as being drug-related profits.
Six other men who admitted taking part in the conspiracy, one of which was the owner of the phone that held the Whatsapp message, received between 8 and 30 months each.
Elliott Morris’ girlfriend, Rosaleen Abdel-Saleem, was found not guilty of taking part in the conspiracy but was fined £350 ($501) for possessing ecstasy. A Birmingham man, Chazino Suban, was also found not guilty of the conspiracy but was fined £700 ($1003) for possessing cannabis and cocaine.
Follow @LisaVaas
Follow @NakedSecurity
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/jq2lBFjGfVw/