Microsoft has designed a family of Arm-based system-on-chips for Internet-of-Things devices that runs its own flavor of Linux – and securely connects to an Azure-hosted backend.
Dubbed Azure Sphere, the platform is Microsoft’s foray into the trendy edge-computing space, while craftily locking gadget makers into cloud subscriptions.
The way it works is like this: Microsoft makes its system-on-chip (SoC) blueprints available to chip designers, which fabricate the chipset and flog it to IoT device makers. These manufacturers slap the silicon in their products, and run Microsoft’s Linux-based Sphere OS along with their own software on the chip, which connects to Microsoft’s Azure Sphere running on Redmond’s cloud.
Sphere does things like make sure gizmos only run official firmware, and automatically pushes out and installs bug fixes on remote devices, and so on. In the process, the chipmaker moves more silicon, the device vendor gets a turnkey security service to show to customers, and Microsoft gets a cloud customer for the lifespan of the device.
It’s basically a rip-off of Arm’s Mbed Cloud, if you don’t want to be generous to Microsoft. The Windows giant calls its chip an MCU – a micro-controller unit – even though pretty much everyone else would call it a system-on-chip. Let’s see what’s in it…
So what’s on the chip?
The Azure Sphere MCU itself is a combination of Arm processor cores, wireless connectivity, memory, some IO, and Microsoft’s custom security controller and core sandboxing.
The heavy lifting will be done by an Arm Cortex-A CPU that will run the device’s application code and Redmond’s custom Linux OS. A pair of Cortex-M cores handle the I/O, and can be accessed by the gadget’s engineers: you can run whatever code you need on them.
A third Cortex-M core forms the basis of Microsoft’s homegrown “Pluton” security coprocessor, which polices the system: it is off-limits to application software on the Cortex-A CPU, and the code running on the other Cortex-Ms. Pluton is kept separate by what Microsoft calls hardware IO firewalls within the SoC.
Whatever firmware is loaded, and regardless of whether or not it has been hacked while running, the Pluton part should remain unaffected and unmolested.
Pluton provides a secure boot mechanism so only officially sanctioned firmware runs, and it uses cryptographic certificates to encrypt and protect its communications with the Azure backend, and to authenticate the gizmo so that the servers can be sure they are talking to legit non-tampered-with hardware. The goal is to stop people or miscreants modifying the firmware, to prevent counterfeit products from connecting, to encrypt data traffic, to receive and install trusted software updates, and so on.
In order to guarantee this, the Pluton section exclusively oversees the Wi-Fi hardware: if application-side code needs to talk to the outside world, it has to ask nicely via APIs with the security coprocessor. The app can’t tell the wireless electronics what to do directly. This stops rogue application code hijacking the wireless connectivity for malicious purposes.
All in theory, of course. Computer security mechanisms and defenses are known to have exploitable bugs – the original Microsoft Xbox, anyone?
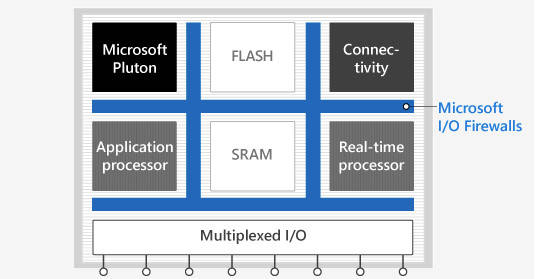
A diagram of the MCU’s layout
The only hardware partner seemingly with hardware at launch is MediaTek: its spin of the chip family is the MT3620. It uses a Cortex-A7 and Cortex-M4F cores along with the Pluton coprocessor and walled-off Wi-Fi transceiver. It features serial interfaces, analog-to-digital converters, pulse-width-modulation outputs, and general input-output pins, all for reading from sensors and buttons, controlling motors, and activating stuff like LEDs.
Microsoft said its reference blueprints for Pluton SoCs are flexible, so chip slingers will have some choice in which Arm cores and IO peripherals they use.
Arm, meanwhile, is pitching its part in this – minus the Pluton and Sphere OS components – as the Platform Security Architecture. Basically, if you want to do your own IoT security chips, you can use the Cortex-A and Cortex-M cores along with Arm’s design kit to produce something similar.
Microsoft’s Arm Linux
In the middle sits Azure Sphere OS. This is Microsoft’s custom Linux kernel that runs on the SoC’s application core, executes your device’s main software, and is designed to talk to the Pluton portion of the chip so that it can send and receive network traffic via the walled-off Wi-Fi controller.
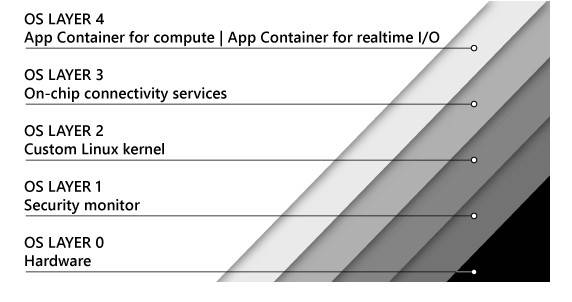
Azure Sphere OS’s security levels
Microsoft has produced a Visual Studio extension for writing code that runs on the application CPU core. Microsoft said it will deliver dev kits by the middle of the year, with the first devices using this technology shipping by the end of 2018.
From there, the MCU-equipped internet-of-things will connect to the Azure Sphere Security Service backend, the actual cloud service where Microsoft will handle things like incident reports, software updates, and failure reporting.
The cloud service is where Microsoft makes its money on the whole deal – the chip blueprints are offered royalty free. Azure Sphere will be sold as a “turnkey” service for companies that are embedding connectivity into their primary products and don’t want to worry too much about security. From there, other Azure services (cloud compute, SQL server, etc) are natural fits, meaning even more subscription cash.
Microsoft also gets the benefit of an even wider net to catch various bad actors. Now, Redmond can tell its enterprise customers it monitors IoT devices and can catch those high profile botnets and big news threats. Getting potentially billions of new info sources under the umbrella will only help Microsoft sell its other big-money security products. ®
Sponsored:
Minds Mastering Machines – Call for papers now open
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2018/04/17/microsoft_azure_sphere_iot_chip/







