Data exfiltrators send info over PCs’ power supply cables
If you want your computer to be really secure, disconnect its power cable.
So says Mordechai Guri and his team of side-channel sleuths at the Ben-Gurion University of the Negev.
The crew have penned a paper titled PowerHammer: Exfiltrating Data from Air-Gapped Computers through Power Lines that explains how attackers could install malware that regulates CPU utilisation and creates fluctuations in the current flow that could modulate and encode data. The variations would be “propagated through the power lines” to the outside world.
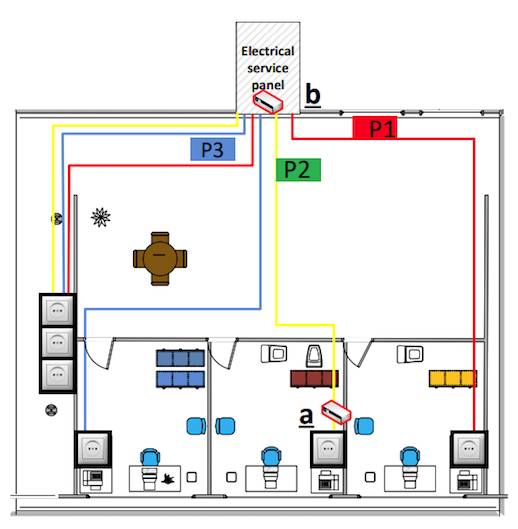
Put the receiver near the user for highest speed, behind the panel for greatest secrecy
Depending on the attacker’s approach, data could be exfiltrated at between 10 and 1,000 bits-per-second. The higher speed would work if attackers can get at the cable connected to the computer’s power supply. The slower speed works if attackers can only access a building’s electrical services panel.
The PowerHammer malware spikes the CPU utilisation by choosing cores that aren’t currently in use by user operations (to make it less noticeable).
Guri and his pals use frequency shift keying to encode data onto the line.
After that, it’s pretty simple, because all the attacker needs is to decide where to put the receiver current clamp: near the target machine if you can get away with it, behind the switchboard if you have to.
With power supplies now representing a data exfiltration vector, defending yourself has requires hermit-like separation from the world: you have to do without wireless connections, use a fanless computer, block the USB ports, install machines in a windowless room with any LEDs covered by black tape, make sure nobody can sense a PC’s magnetic fields, and disconnect the speakers.
If you see a developer in cave with a big stack of pre-charged batteries, this is why. ®
Sponsored:
Minds Mastering Machines – Call for papers now open
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2018/04/12/malware_exfiltrates_data_over_power_supply_cables/