Target issues apology letter
 A Naked Security reader just emailed us to say, “I received a message from Target about the breach. It talks about customers, and people who shopped at the company’s stores, and names me in the breach. But I’ve never acutally shopped at Target.”
A Naked Security reader just emailed us to say, “I received a message from Target about the breach. It talks about customers, and people who shopped at the company’s stores, and names me in the breach. But I’ve never acutally shopped at Target.”
The concerned reader also pointed out that the statement was published on Target’s website back on 13 January 2014, but the email she received only arrived on 16 January 2014.
She admitted that the email didn’t look dangerous: it had no links to login pages and no suspicious attachments, so it didn’t seem to be anything to worry about.
Except for the fact that she received it at all – and apparently three days’ late at that.
Giving bad news in a good way
That’s always a problem for a company faced with delivering tough security news by email: it’s hard to make the message look obviously different from an email sent by crooks trying to capitalise on the disaster.
Let’s see how well Target did, and if there is anything they might have done differently.
Here is the web version in full:

The message is short, it doesn’t try to pretend the breach didn’t happen, and it offers a sincere apology.
All those things are good.
But there are two things I’d definitely have done differently.
Make it abolutely clear who had what stolen
Firstly, I’d have avoided mixing the words “guests”, “customers” and those “who shopped,” since it’s not clear whether they are intended as synonyms, or merely as different, possibly overlapping, groups of victims.
That, in turn, means it isn’t clear which group Target thinks each victim was in.
It certainly seems, from our reader’s confusion, that “guests” (who lost details like name, address and phone number) include people who have had something to do with Target, somewhere, somehow, but who have never actually have bought any products there recently, or even at all.
So here’s what I think Target is trying to say:
- We have a large database of people who have interacted with us, called “guests”, including customers (who have bought something from us at some stage), and others (who have shared personal information with us, but never actually purchased anything). If you are in this group, your name, address, phone number and email address were stolen by the crooks.
- We have a subset of the above database, consisting of customers who actually bought something from one of our stores (not online), using a payment card, between 2013-11-27 and 2013-12-15 inclusive. If you are in this group, your payment card details, such as number and expiry date, were stolen as well.
If you are in group 2, you can have a year of credit monitoring for free, but if you’re only in group 1, you can’t.
Target really needs to clarify who was in which group (or both), and which recipients of the email quality for the free monitoring.
It’s obvious that there are people whose names and addresses were stolen but who didn’t buy anything recently, who didn’t lose any payment card details in this breach and who therefore don’t qualify for the free credit monitoring.
Target has mixed together the warning sent to people who lost non-payment information only and the warning to those who lost payment card data as well.
That, in my opinion, is a recipe for confusion.
Don’t trust the caller
Secondly, if I were Target, I would not have said this:
Never share information with anyone over the phone, email or text, even if they claim to be someone you know or do business with. Instead, ask for a call-back number.
If you don’t know and trust someone who calls you, why would you trust any phone number or web URL they might give you?
Just bear in mind how successful the so-called fake support call scammers have been in recent years.
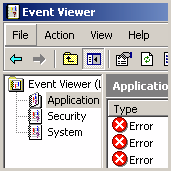 Those are the guys who phone you out of the blue, falsely claim that there is a virus on your computer, dishonestly use the Event Viewer to show you errors that “prove” their claim, and then fraudulently charge you $300 for cleanup.
Those are the guys who phone you out of the blue, falsely claim that there is a virus on your computer, dishonestly use the Event Viewer to show you errors that “prove” their claim, and then fraudulently charge you $300 for cleanup.
If you ask for a number to call those guys back, or simply use the number that came up on your CallerID/CLI display, which amounts to the same thing, you will almost certainly be given a legitimate-sounding local landline number.
If you’re in Sydney, Australia, for example, the number will probably be something like +61.2.8xxx.xxx; if in Oxford, England, +44.1865.7xx.xxx; and so on.
And if you call that number back, guess what?
You will get through to the company that just called you.
Having an honest-looking local phone number doesn’t mean the caller is an honest, local person; the same applies to website domain names.
Domain names can, and frequently do, redirect anywhere; the same is true of phone numbers these days.
Don’t rely on information that could have come from a scammer to help you determine if that person is a scammer.
Use some objective, independent means of finding out the contact details of anyone who claims to represent a company you do business with and who asks you to disclose any personal information.
In the case of your bank, for example, you can probably find the number to call to dispute a payment card transaction on the card itself, or on a recent statement, or (as I notice many banks are doing now) on-screen at any ATM, without needing to insert a card.
And if you are an organisation that finds itself needing to call customers to look into suspicious activity on their account, try to do the right thing from your side.
Please avoid opening the call, as many companies still seem to do, by saying:
Hello, I am X from Y, investigating a possible problem with your account Z. Before we start, for security purposes, I need you to give me your date of birth and your security codeword.
Try a refreshingly different approach, such as this:
Hello, I am X from Y, investigating a possible problem with your account Z. But because you don’t know me, don’t tell me anything yet. I’m going to hang up; I’d like you to take out your {payment card, last statement, contract} and look in the top right corner where it gives an emergency contact number. Then call us back!
As for Target, let’s hope the company distinguishes the various parts of the breach a bit more clearly.
If the crooks got at your payment card data, did they get your home address and phone number, too?
If they got your address and phone number, should you cancel your cards even if you didn’t shop at Target recently?
Clarification along those lines would be very handy.
In the meantime, here’s a short podcast in which we offer some advice on dealing with suspicious callers who try to scam you or your friends and family over the phone:
![]()
(Audio player not working? Download to listen offline, or listen on Soundcloud.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/HUCMHxo8Zv4/