Telegram Messenger delivers candygrams to stalkers
Mere days after opsec expert The Grugq warned that popular messaging app Telegram Messenger couldn’t be regarded as secure, another researcher has demonstrated how its metadata leaks expose users to stalking.
Over at Github, Ola Flisbäck offers up a depressing demonstration of just how easy it is to zero in on an individual by watching the stream of presence and status notifications.
Invisible to ordinary Telegram users, the metadata is accessible to command-line clients, Flisbäck says.
Here’s the problem: in trying to make sure Telegram is usable, it’s been made way too chatty. For example, Flisbäck writes, “The Telegram Android app sends a notification to all contacts when it becomes or stops being the “foreground” app on the device.
“Using that information alone it’s at times easy to make guesses about who’s talking to who if you have several contacts in common with a ‘victim’. An ‘attacker’ will sometimes see the victim and another contact taking turns going active/inactive as they pass messages back and forth.”
It gets better, Flisbäck notes, since if you know the target’s phone number, you can add their phone number to your contacts. That alone is enough to subscribe your phone to their metadata.
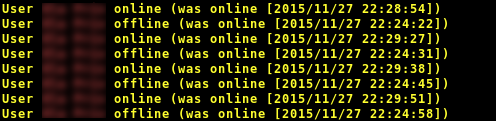
Telegram’s background chat a security risk. Image – Ola Flisbäck
Anyone capturing enough Telegram user metadata would have no trouble working out who is talking to whom, because (for example) a pair of users exchanging text messages will take turn going active and inactive.
If The Grugq and Matthew Green are right and Telegram’s encryption is also problematic, the app is probably more like the spook’s friend than the enemy of civilisation. ®
Sponsored:
Go beyond APM with real-time IT operations analytics
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2015/11/29/telegram_delivers_candygrams_to_stalkers/