Unholy trinity of AKBuilder, Dyzap and Betabot used in new malware campaigns
In recent weeks, SophosLabs has published papers outlining threats from AKBuilder and Betabot. Now, it appears the bad guys are combining the two in new attack campaigns.
SophosLabs principal researcher Gábor Szappanos said the lab has received and analyzed a handful of AKBuilder-generated documents in the past week. The documents initially drop a file that contains two payloads: one, the popular Dyzap credential stealer; the other, something that appears to be a version of Betabot. “We thought that Betabot was pretty much dead, with no activity in the past months – up until last week,” Szappanos said.
The malware and tools in question
Before looking at the new developments, a review of the malware is in order.
- AKBuilder is an exploit kit that generates malicious Word documents, all in Rich Text. Once purchased, malicious actors use it to package malware samples into booby-trapped documents they can then spam out. SophosLabs has analyzed and defended customers against two versions – AK-1, which uses two exploits in the same document: CVE-2012-0158 and CVE-2014-1761, and AK-2, which uses a single exploit: CVE-2015-1641.
- Dyzap is a banking Trojan commonly found along with malware called Upatre. The Upatre component is typically delivered in bulk, via spam, and then used to install the banking Trojan on infected computers.
- Betabot is a malware family used to hijack computers and force them to join botnets. It has been used to steal passwords and banking information, and has most recently been used in ransomware campaigns. Betabot has been around for a long time. Its code is easy to duplicate and attackers have turned to a cracked builder to produce it on the cheap.
The three converge
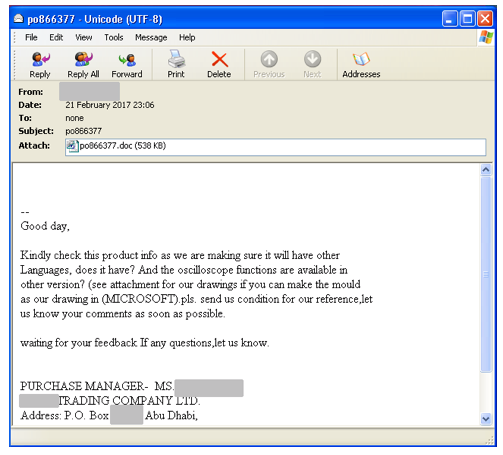
Szappanos shared his findings with Naked Security Wednesday morning. He said the malware is delivered in email messages like this:
And this:
The attachment of the messages are Rich Text Format documents generated by AKBuilder. These documents drop the additional malware components. Here’s some basic information about the documents:
The exploited documents drop two files, which are two different Trojans:
%USERHOME%AppDataRoamingwin32.exe : Dyzap credential stealer
%USERHOME%AppDataLocalTempnbot.exe :Betabot/Neurevt Trojan
Dyzap is executed automatically on startup by %STARTUP%win32.vbs
The CC addresses were used by Dyzap to send credentials to:
monetizechart.me
dfoxinternashipoop.top
conticontrations.com
mdelatropsopc.info
scopeclothingsltd.pro
The malware submits stolen info to a php script on the server, the name of which is fre.php by default
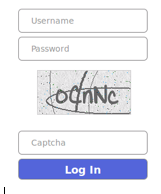
The login of the CC panel looks like this:
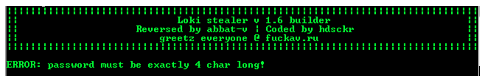
The builder of Dyzap (at least a cracked version) looks like this:
It calls itself Loki stealer, but to avoid confusion with the Locky ransomware, it is simply called Dyzap.
Defensive measures
Since Betabot has most recently been used to serve up ransomware, a reminder of our tips on that front should be useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To protect against VBA malware, tell Office not to allow macros in documents from the internet.
- To learn more about ransomware, listen to our Techknow podcast.
To protect against AKBuilder activities, simply applying recent patches for Microsoft Office should be enough to disarm the attack.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/oJMBsyZbHIw/