Using WPS on your Wi-Fi router may be even more dangerous than you think
 A Swiss security researcher has found yet more problems with Wi-Fi Protected Setup (WPS), a system built into many wireless routers to make it easier for you help guests and visitors to get online.
A Swiss security researcher has found yet more problems with Wi-Fi Protected Setup (WPS), a system built into many wireless routers to make it easier for you help guests and visitors to get online.
The idea of WPS is to provide a controlled way for someone whom you trust to connect to your Wi-Fi network by typing in just an 8-digit PIN instead of your full wireless password.
That sounds counter-intuitive, because we have regularly advised that your minimum Wi-Fi security level should be Wi-Fi Protected Access (WPA) with a well-chosen password, known as the Pre-shared Key (PSK).
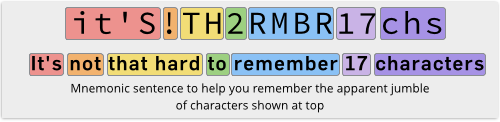
Indeed, we recommend aiming for a PSK length of least 14, using a mixture of letters, numbers and “wackies” (punctuation), and we suggest that you create an aide memoire, such as “it’s not that hard to remember 17 characters” to represent a password like it’S!TH2RMBR17chs.
However, even if you let your laptop, phone or tablet store the PSK for later, you still have to type in it once.
And trying to spell it out phonetically to visitors so they can type it in by hunting-and-pecking on a mobile phone can be frustrating.
WPS to the rescue
 That’s where WPS comes in, so your visitors can type in an 8-digit PIN instead.
That’s where WPS comes in, so your visitors can type in an 8-digit PIN instead.
The idea is that the PIN is generally kept private because it’s printed on a sticker under the router, thus preventing remote attackers from getting hold of it.
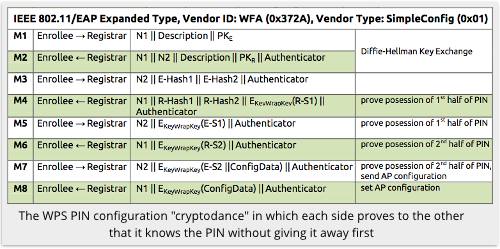
Additionally, there’s an eight-step cryptographic dance that your computer has to undertake with your wireless router before the router will cough up an encrypted copy of the PSK so your computer can then connect to the network permanently.
That cryptographic dance is supposed to make the PIN-based WPS connection time-consuming – sufficiently time-consuming that trying just 100 million 8-digit numbers instead of 100 million million million 14-character passwords is still secure enough.
The problem with WPS
Back in 2011, however, a researcher studying the WPS PIN protocol realised that you didn’t need to try all 100 million possible 8-digit PINs.
Firstly, the last digit of the eight is just a check digit that is calculated from the previous seven, as a way of quickly spotting typing errors.
That means that WPS PINs are effectively only seven digits long.
Secondly, the eight-step protocol doesn’t actually validate the your PIN in the form of a seven-digit number.
It checks the first four digits, and only if those are right does it check the last three digits.
That means that if you are guessing at the PIN, you don’t need to try all seven-digit codes from 0000000-9999999; instead, at worst, you need to try the codes from 0000-9999, followed by the codes for 000-999.
Instead of 107 choices (10,000,000), you are down to 104 (10,000) plus 103 (1000), for a total of just 11,000.
→ When you split a password in half, you don’t end up with two passwords each of half the strength. You end up with two passwords each with the square root of the strength you had before. A 32-bit number, for example, can count up to 4 billion, but a 16-bit number can only count up to about 65 thousand (232 versus 216).
What happened next
We advised in late 2011 that you should simply turn off WPS.
What sounded at best like a risky idea (replace a 14-character strong password with an 8-digit weak one) turned out to be much worse, more like replacing a 14-character password with a 4-digit one.
Turning off WPS was easier said than done, however, with some routers apparently unable to disable WPS at all, even if they had a button in their web interface that claimed to do so.
Fast forward nearly three years, and at least some router vendors have introduced workarounds into their firmware, for example by locking you out of WPS for a while after a few failed attempts to connect, thus disrupting a brute-force attack where you simply try every possible PIN.
More problems with WPS
In the recent Swiss attack mentioned above, researcher Dominque Bongard recently found a new problem with WPS that puts PIN guessing back on the table.
The good news is that Bongard’s problem is not a flaw in the WPS design, but rather a weakness in a few (unspecified) implementations.
That means his problem can be completely fixed, not merely worked around, and that many routers, if not most, will not be at risk.
Nevertheless, Bongard’s discoveries make WPS totally useless (downright dangerously useless, in fact) on affected hardware.
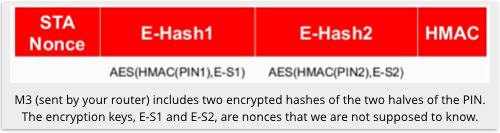
Very briefly explained, Bongard focused on the fact that the third message in the eight-step cryptographic dance mentioned above consists of a cryptographic hash of the WPS PIN, encrypted with a pair of nonces, or one-time random numbers, generated by the router.
The router only reveals the nonces later on in the protocol, after you have proved you know the PIN, allowing you to decrypt the message later and thus to confirm that the router knows the PIN as well.
This reassures you that you are connecting to the right router, not to an imposter that is simply pretending to have validated the PIN you submitted.
What if you could guess the nonces?
But what if you could guess the nonces used as encryption keys in the third message?
In that case, you could use the contents of the message to perform an offline attack to guess the PIN; then you could start your WPS connection all over again, and this time you would get in immediately.
Here’s why.
The router has sent you the data you’ll get if you hash the PIN (in two halves) using a known cryptographic hashing algorithm, and then encrypt those halves using AES with the encryption keys set to the random numbers you aren’t supposed to know yet.
So if you do know the encryption keys, you can try the same calculations for every possible PIN (of which there are only 10 million) and stop when you hit the same data that the router just sent you.
When you get a match, you know you have supplied exactly the same inputs, including the PIN, that the router used.
Bingo.
Guessing the nonces
Bongard claims to have identified at least two (unspecified) router firmwares with different implementation problems.
The first firmware used a non-cryptographic random number generator that produced a repeating cycle of just 232 possible outputs, making it possible to work out where in the cycle you’ll be if you can force the router to reboot and then attempt your WPS connection.
Worse still, the first message in the WPS protocol (M1 in the diagram above) involves the router sending you a random number as a sort of session ID.
Bongard claims that the buggy WPA code generates the two encryption key nonces immediately after generating the random number for M1, allowing you to use the first nonce to determine exactly where you are in the random number generator cycle and thus to recover the keys easily.
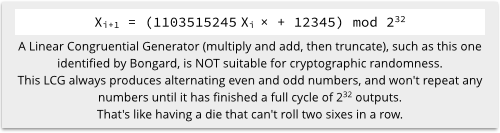
(With just 232 outputs in the random sequence, you can quickly generate and store it as a lookup table for later.)
The second firmware apparently used a slightly stronger, though still non-cryptographic, random generator, which would probably have been enough of a weakness on its own to attack the PIN, but this firmware messed up the random key generation anyway, so the same “random” keys were used every time!
On these firmwares, at least in theory, you can kick off a WPS connection, proceed up to the third message in the cryptographic dance, and then bail out.
That effectively gives you an encrypted hash of the PIN where you know the encryption key, which is, as we pointed out above, equivalent to giving you a straight hash of the PIN.
There are just 10,000,000 PINs and no “key stretching” (repeated hashing or encryption operations) to slow down a brute force attack by extending the effort needed for each split-hash-encrypt operation.
So you can probably crack the PIN in a few seconds on a modest laptop.
What to do?
• Don’t try to invent your own random number generator.
If you knit your own random generator, history suggests you are likely to end up with imperfections.
These can be very expensive in security terms.
• Turn off WPS.
Really: turn it off and leave it off.
It’s not a good idea to rely on a hard-wired 8-digit PIN as a short-cut to let guests onto your network, even if you ignore the errors in the design (and possibly in your implementation) of the WPS system.
• Watch our Busting Wireless Myths video.
Make sure that you aren’t using other Wi-Fi security “features” that don’t actually provide security at all.
• Use the Sophos UTM at home for free
Looking for a full-strength product to replace or augment your regular home router?
Try our enterprise grade protection at home for absolutely no cost.
NB. The Sophos UTM does not support WPS, because WPS is neither necessary nor desirable. So the risks outlined in this article do not apply if you are using Sophos Access Points plus a Sophos UTM to manage your wireless connectivity.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/DbB5EnJ8UaM/