After WannaCry, EternalRocks digs deeper into the NSA’s exploit toolbox
Shortly after the WannaCry outbreak began to ebb last weekend, security experts warned that this wasn’t over. Copycats would surely cook up new malware using NSA tools leaked by Shadow Brokers. In recent days, we’re seeing some evidence of that.
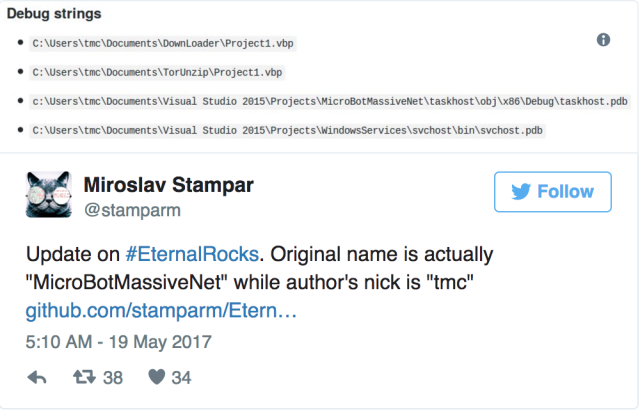
Miroslav Stampar – a member of the Croatian Government CERT and author of the sqlmap tool used to detect and exploit SQL injection vulnerabilities – detected a new worm that exploits Windows Server Message Block (SMB) vulnerabilities. He named it EternalRocks and said it uses six SMB-specific NSA tools to spread, whereas WannaCry used only two to infect hundreds of thousands of computers across the globe.
WannaCry spread with the help of the NSA’s EternalBlue and DoublePulsar exploits. Stampar said EternalRocks exploits EternalBlue, EternalChampion, EternalRomance and EternalSynergy – all SMB exploits – as well as SMBTouch and ArchiTouch, NSA tools used for SMB spying operations. His full analysis is posted on GitHub.
At this point, the malware doesn’t appear to be dropping ransomware or any other payload. But it could be paving the way for a future attack.
Defensive measures
With the return of old-school worm outbreaks, it’s worth reviewing steps users can take to avoid infection. Unfortunately, some of those steps have proven unpopular, as Naked Security’s John Dunn wrote. Admins can block services or ports at firewall level but not often indefinitely. Suspending email is another tactic that works until everyone complains.
The best advice remains the same as it did when the outbreak began:
To guard against malware exploiting Microsoft vulnerabilities:
- Stay on top of all patch releases and apply them quickly.
- If at all possible, replace older Windows systems with the latest versions.
Follow @NakedSecurity
Follow @BillBrenner70
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/9BK1vTtoiXg/