Apple’s iCloud iConundrum
 Information security has become such a booming business that it seems there is a conference somewhere in the world every single week.
Information security has become such a booming business that it seems there is a conference somewhere in the world every single week.
Back in the day we saw big hackerish announcements twice a year, during Black Hat and the Chaos Communication Congress. Now it is happening everywhere, all the time.
Last week at the Hack in The Box conference in Malaysia, researcher Vladimir Katalov made some rather bold claims about the security of Apple’s iCloud backups and iCloud document storage.
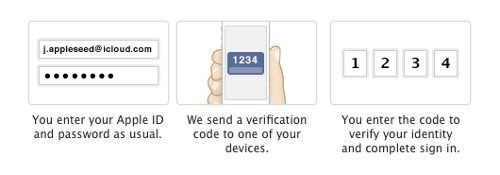
It must first be noted that more than six months after launch, Apple has still only introduced two-factor authentication in a handful of countries. I was not able to test all of these claims as it is not yet available in Canada.
In his talk, “Cracking and Analyzing Apple’s iCloud Protocols”, Katalov showed how Apple’s optional two-factor authentication is selective in its application, even where it is available.
First, two-factor is optional. This is true for most services, but I would like to see someone begin making it mandatory.
Passwords are just too vulnerable and unfortunately two-factor has become the bare minimum for cloud services if you don’t want others accessing your information.
Second, but more importantly, Apple’s two-factor authentication only applies to three specific applications of your Apple ID:
- Making a purchase in iTunes/App Store.
- Managing or changing your Apple ID.
- Working with Apple’s technical support team.
Notice how it is inclusive, rather than exclusive. These are the only things protected and nothing else is guaranteed or indeed, included.
What Katalov discovered is that iCloud backups and iCloud documents are not protected by the two-factor system and that they are stored on Microsoft Azure and Amazon AWS cloud services.
Additionally, while the files are stored encrypted, the encryption keys are stored with the files. . . rendering the encryption largely worthless. It also means that Apple can disclose the contents of iCloud stored files on request of law enforcement and governments if they are required to.
 Katalov demonstrated that by simply acquiring the Apple ID and password of another user, whether they have enabled two-factor authentication or not, he can download their iPhone/iPad/iPod backups and documents from iCloud and see their pictures, music, emails, contacts, documents, presentations, spreadsheets or anything else without the victim being alerted.
Katalov demonstrated that by simply acquiring the Apple ID and password of another user, whether they have enabled two-factor authentication or not, he can download their iPhone/iPad/iPod backups and documents from iCloud and see their pictures, music, emails, contacts, documents, presentations, spreadsheets or anything else without the victim being alerted.
Most users likely assume that by enabling two-factor authentication they are protecting their iCloud data from being stolen if their password is guessed, get infected with a keylogger or are phished. That is true for making an App Store purchase, but all bets are off for iCloud.
Furthermore, iPhone backups can be restored to any device with just the password. If I am able to acquire your Apple ID, I can download everything on your phone to mine. You will get a warning email after the fact, but arguably that is too little too late.
Katalov’s research shows that Apple has only half implemented their two-factor technology and has chosen convenience over actual security. Hopefully his shining a light on the problem will prompt some action from Apple to close these holes.
Image of a apple with an arrow through it courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/CHpSapkBuyI/