How anyone can hack your Instagram account
Stevie Graham, a security researcher who reported an authentication flaw in Instagram’s iOS software a few days ago, was denied a bug bounty by Facebook.
Presumably, that’s because the flaw isn’t new, rather than because it isn’t serious. (Indeed, we first wrote about this problem in 2012.)
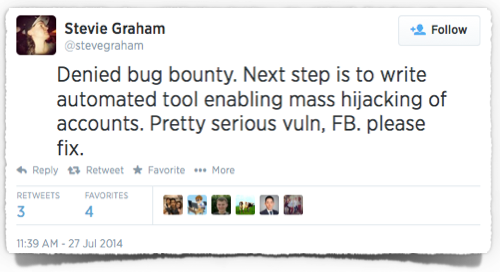
So Graham has gone public with instructions on how to hack other people’s Instagram accounts.
All you need is shared Wi-Fi, a packet sniffer, and the willingness to break the law to violate someone’s privacy.
Simply put, the attack is just Firesheep all over again.
Remember Firesheep?
Social networking security, 2010-style
Back in 2010, social networks like Twitter and Facebook handled session authentication like this:
- Accept a connection using HTTPS (secure HTTP), and let the user enter his username and password over an encrypted connection, to stop criminals from sniffing the credentials.
- Send back a unique “session cookie”, valid until logout, with a one-time cryptographic code that proves the user has already logged in correctly.
- Subsequently accept that cookie over insecure (HTTP) connections.
So you couldn’t sniff the user’s password for next time, but you could sniff his session cookie and hijack his current Twitter or Facebook session in real time.
Enter Firesheep
 Firesheep was a Firefox plugin that automated the process of waiting for users to login and then stealing their session cookies.
Firesheep was a Firefox plugin that automated the process of waiting for users to login and then stealing their session cookies.
That made it a point-and-click exercise to take over their accounts, at least until they realised what was going on and logged out.
The ostensible motivation for Firesheep, even though it was ripe for abuse, was to create a public kerfuffle big enough to push services like Twitter and Facebook to use HTTPS all the time.
And that is exactly what Facebook, Twitter and and others did, because it solved the problem: no unencrypted session cookie to sniff meant no session to hijack.
2010 revisited
Fast forward nearly four years, and it looks as though the Instagram iOS app works in almost exactly the same way as explained in the 1-2-3 list above.
In short, it allows HTTP connections after the initial login.
So Instagram users with iPhones and iPads can be hijacked with ease, or so Stevie Graham claims.
So easily, in fact, that he gives five simple steps to do it:

Ouch.
What next?
We have just three words of advice: don’t do this.
(At least, don’t do it to someone else’s account, unless they explicitly give you permission.)
It’s definitely not nice, and it’s almost certainly not legal, wherever you may live.
But if it really is as easy as Graham says, let’s hope Facebook gets onto it pretty quickly.
In the meantime, you probably want to give up logging into Instagram from your iPhone or iPad.
And then we can worry about how to create a public kerfuffle big enough to raise the bar for the security of mobile apps in general, because we seem to keep writing about how they are lagging behind…
TAKE OUR POLL
(If you would like to explain your reasoning, please leave a comment below. You may remain anonymous.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/BYWpXU0-NTs/