Microsoft issues alert for Word zero-day – booby
 Microsoft has issued an emergency security alert about an in-the-wild exploitable vulnerability in Word.
Microsoft has issued an emergency security alert about an in-the-wild exploitable vulnerability in Word.
To clarify the jargon in that first sentence:
- A vulnerability is the flaw that caused the bug that could let crooks get in.
- An exploit is a way for the crooks to use a vulnerability in practice, and actually get in.
- In the wild means the crooks not only can get in, but are actively doing so already.
If that sounds rather bad, it is.
Usually, Microsoft’s updates appear in a regular, frequent and predictable way, published on Patch Tuesday, the second Tuesday of every month.
This is a good approach for patching vulnerabilities for which no known exploit yet exists, or exploits that were discovered by Microsoft’s own researchers, or holes that were found privately and responsibly disclosed to Microsoft so it could fix them before they became publicly known.
It gives Microsoft time to test, and test again, that the patches don’t cause problems that outweigh the security risk or, worse, open up yet more security holes.
And it lets IT teams plan their routine patching to minimise disruption.
But when the crooks start using an exploit before a patch is available, the hole is rather quaintly called a zero-day, or 0-day (pronounced “oh day”), because the maximum number of days you could have been patched ahead of the exploit was zero.
Many, if not most, software vulnerabilities are hard to exploit, meaning that even if you patch some time after the fix was available, you might get lucky.
The crooks might never actually manage to work out how to turn the vulnerability into a practicable exploit. (This is rather dramatically called weaponising a vulnerability.)
But in the case of a zero-day, the weaponisation has already happened.
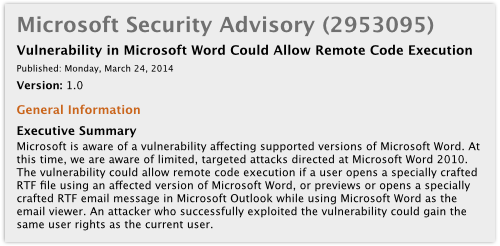
That’s the case with this latest alert about what is known as CVE-2014-1761, as Microsoft explains:
Microsoft is aware of a vulnerability affecting supported versions of Microsoft Word. At this time, we are aware of limited, targeted attacks directed at Microsoft Word 2010. The vulnerability could allow remote code execution if a user opens a specially crafted RTF file using an affected version of Microsoft Word, or previews or opens a specially crafted RTF email message in Microsoft Outlook while using Microsoft Word as the email viewer. An attacker who successfully exploited the vulnerability could gain the same user rights as the current user.
Sophos products detect booby-trapped files exploiting this vulnerability as Exp/20141761-A.
This sounds surprisingly like two existing, well-known Word exploits that have been widely used over the past few years.
These previous exploits are two and four years old respectively, and go by the tags CVE-2010-3333 and CVE-2012-0158.
 SophosLabs researcher Gabor Szappanos (Szappi) recently published a paper analysing the historical record of these two vulnerabilities – both are generally exploited by what Microsoft above calls “specially crafted RTF files” – and discovered an interesting phenomenon.
SophosLabs researcher Gabor Szappanos (Szappi) recently published a paper analysing the historical record of these two vulnerabilities – both are generally exploited by what Microsoft above calls “specially crafted RTF files” – and discovered an interesting phenomenon.
Szappi noticed the 2010 and 2012 exploits were intially seen almost exclusively in attacks that were probably initiated for intelligence gathering purposes, presumably by hackers paid to conduct national or industrial espionage.
But over the past year, that has changed so that these exploits now appear frequently in broader attacks mounted by cybercriminals focused on making money through bots and zombies.
Don’t wait for that to happen here – mitigate the CVE-2014-1761 problem right away!
You can reduce your exposure to attacks delivered in RTF files with these steps:
1. Block RTFs at the gateway.
Consider blocking or quarantining these files by type or extension at your email gateway.
Sophos’s Email Appliance and UTM products can do this for you.
2. Stop RTFs opening in Word.
Consider using Microsoft’s Fix it solution to turn off Word’s ability to open and view RTF content altogether.
3. Use Microsoft’s EMET.
Consider using Microsoft’s Enhanced Mitigation Experience Toolkit (EMET) as a way to sandbox Microsoft Office to make it harder to exploit.
EMET can prevent unpatched vulnerabilities from being successfully weaponised.
4. Switch to plain text in email.
If you use Outlook, consider switching your email to plain text.
This makes some emails, such as marketing mails and newsletters, harder to read.
But it limits your risk when reading emails containing booby-trapped content.
By the way, when a permanent fix for CVE-2014-1761 comes out, take the opportunity to make sure that you aren’t missing the patches for CVE-2010-3333 and CVE-2012-0158.
The fact that cybercrooks are still making extensive use of these holes, years on, suggests that many people still aren’t patched.
That might be because they aren’t patching at all, but seems equally likely that even users and IT administrators who try to be faithful about Microsoft updates may be lacking one or two fixes, exposing them to the very holes that cybercriminals are adept at jumping through.
NB. Article updated at 2014-03-25T14:30Z to clarify that only a workaround is currently available from Microsoft, not a permanent patch.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/P-HiAsIUMoc/