Microsoft’s Patch Tuesday is out
 Microsoft’s Tenth Anniversary Patch Tuesday is out, and, yes, Redmond’s security gurus did patch against the recent Internet Explorer zero-day that is being exploited in the wild.
Microsoft’s Tenth Anniversary Patch Tuesday is out, and, yes, Redmond’s security gurus did patch against the recent Internet Explorer zero-day that is being exploited in the wild.
More precisely, the vulnerability CVE-2013-3893 has been fixed, so even if you aren’t using (or couldn’t use) Microsoft’s temporary Fix it, you can now close off that avenue of attack altogether.
Notably the Fix it was for 32-bit platforms only, so servers and recent laptop installs running 64-bit Windows versions were out of luck.
That’s a creditably quick response from Microsoft, and a great Tenth Birthday result.
By the way, there’s a reliable and easy-to-modify proof of concept exploit floating around on the web, as well as an exploit module for the DIY break-and-enter toolkit Metasploit, so CVE-2013-3893 must be considered a clear and present danger.
The proof of concept I’ve seen is packaged as a single chunk of JavaScript inside a single HTML file, and targets IE 8 and IE 9 on Windows XP, Vista and Seven.
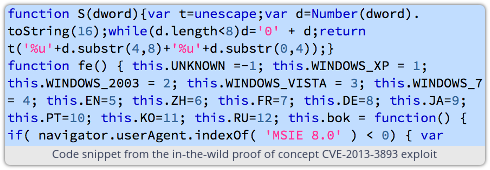
If you view a web page that contains the JavaScript from the proof of concept, then your browser will connect to an external site, download an executable file in the background, and run it.
If you don’t have a decent anti-virus installed (or you have one that hasn’t been updated since the free trial ran out a year ago) then you won’t see anything – not a warning, a dialog box, a progress bar or even a logfile entry – to tell you what happened.
Your browser will eventually crash, but after the download has finished and the secretly installed malware has launched.
→ A decent anti-virus is ilkely to control this exploit. Sophos Anti-Virus, for example, blocks boody-trapped web pages as Exp/20133892-B. But immunising your browser alogether, by neutralising the vulnerability that makes the exploits possible in the first place, is by far the best solution.
But don’t concentrate only on the Internet Explorer “biggie.”
There are six other remote code execution holes fixed this month, and even though four of them are rated only at Important by Microsoft, rather than Critical, I’d still treat “important” as meaning “important enough to patch right away.”
All the Important vulnerabilities are in various components of the Office suite, and can be triggered via shellcode – that’s executable code buried invisibly in amongst data – in files you are entitled to assume that Office should open without risk.
In theory, if you put executable code in a data file, it ought to be harmless: whether you give your name as text that spells out Paul Ducklin or machine code that corresponds to PUSH-PUSH-CALL-POP should make no difference.
The machine code version of your name should be treated as data, and never get a chance to run.
Programming mistakes do happen, however, sometimes allowing deliberately mangled files to confuse Word or Excel (or other software of that sort) into executing data as if it were code.
The eighth patch this month is for an information disclosure bug in Silverlight.
Microsoft isn’t saying what might be disclosed if this bug is triggered.
But since “information disclosure” is another way of saying “potential data breach,” you probably want to patch the eighth one, too.
For the opinion of SophosLabs on the likelihood of each of the eight vulnerabilities being exploited, and for advice on alternative mitigiations (if you are unwilling to patch) or additional mitigations (if you are patching anyway), please visit our Vulnerabilties page.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/AFl18CXunU0/