Osram’s smart bulbs blow a security fuse
Nine security holes, four of them currently unpatched, have been found in the Osram smart light bulb system, potentially giving attackers access to a home or corporate network.
The issues in the Lightify Home and Pro systems range from cross-site scripting (XSS) to problems with the ZigBee and SSL protocols to insecure encryption key handling. They were discovered by security company Rapid7.
Some of them are pretty amateurish, raising the larger question of what kind of security review the products go through before being put on the market.
As a result of the holes, attackers can do everything from turning off the lights and taking control of the management interface – an annoyance but not dangerous – to gaining access to the network by pulling the network password, the first step in what could be a significant compromise.
In perhaps the worst hole (CVE-2016-5051), it was discovered that the Lightify iPad app stored the network Wi-Fi password in plain text, right next to its SSID, providing an open invitation to your network.
The company has put out a patch for it that seemingly prevents the information from being stored in the app itself, but you have to wonder why they weren’t able to simply encrypt the information.
Then there are two still-unpatched holes (CVE-2016-5052 and 5057), due to the fact that the company does not use SSL Pinning and so it is possible for someone to launch a man-in-the-middle attack to access SSL-encrypted traffic. SSL is of course hopelessly broken and has been for some time.
Osram says it is working on a patch to introduce SSL pinning – which basically consists of putting your server’s SSL certificate inside your app and making sure it is an exact match when it first connects. It’s become a pretty common approach, which also raises questions over Osram’s security standards.
And more…
The other holes are equally concerning.
One lets an attacker inject JavaScript and HTML into the username data entry field of the Pro system’s web management tool (CVE-2016-5055) – a pretty basic entry point that should never have been allowed. In turn, that provides access to the system’s setup and data and would enable them to take control of the system. The company has since patched the hole.
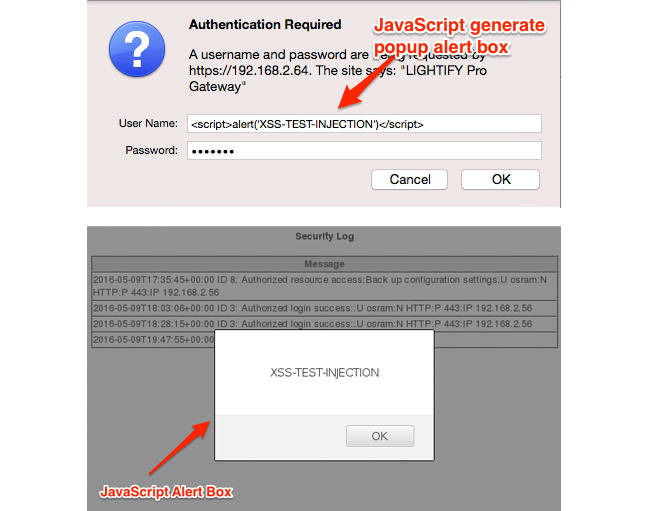
What bad security looks like (Rapid7’s graphics)
The other big, unpatched hole (in both the Home and Pro systems – 5054 and 5058) stems from the fact that the system does not refresh the keys it uses to pair devices to the system through the ZigBee protocol. As such, all past commands can be grabbed and replayed without the need for authentication. Osram says it is working on an update that will introduce routine rekeying.
And if all that weren’t bad enough, the system uses weak default pre-shared keys (PSKs), one being “0123456789abcdef”, which means that it would only take a decent hacker a few hours to break into the system. A patch will use longer and more complex PSKs.
In short, the whole exercise highlights what many people have been warning and worrying about for some time: that smart-home and IoT manufacturers are not doing a sufficient job on security and so opening up consumers and businesses to serious security risks.
As we have seen with baby monitors, smart watches, cameras, bathroom scales, and now light bulbs, this new consumer-friendly technology represents a significant risk and companies need to up their game and take security much more seriously than they currently do. ®
Sponsored:
2016 Cyberthreat defense report
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2016/07/27/osram_smart_lightbulbs/