Palo Alto IDs another C&C-over-DNS attack
Palo Alto Networks researchers say the Webky group is using DNS (domain name system) requests as their command and control channel.
The reason that’s important is that DNS is one of those ports that’s less heavily policed than (for example) Port 80.
The Palo Alto post (by Josh Grunzweig, Mike Scott and Bryan Lee) says the activity was spotted during an attack on an unnamed US organisation.
The attack was based on the HTTPBrowser malware family, which was seen in attacks such as this from 2015 in China.
The researchers dubbed this attack ‘pisloader’. It pointed victims at http://globalprint-us[.]com/proxy_plugin.exe to download malware, which loads the well-known Poison Ivy RAT.
The other domains used in the attack, all newly-registered, were logitech-us[.]com (not the real Logitech), and intranetwebcam[.]com.
It’s mostly the DNS CC that makes this different, Palo Alto Networks writes. Here’s an example of the request:
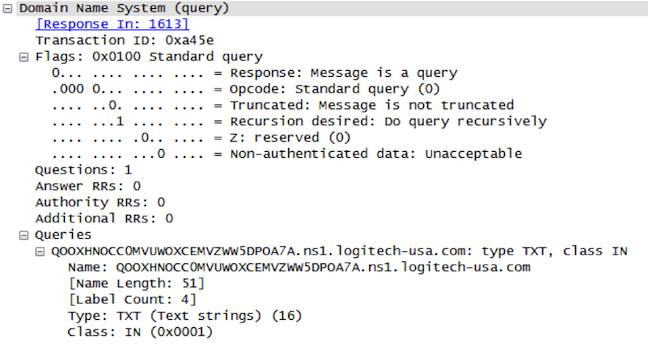
Like FrameworkPOS, putting CC instructions in the protocol is designed to skip past security products.
Hence a response from the CC will be in the form of a DNS response, with instructions to the malware in the text of the response:
As the post notes, the code to generate the commands is at GitHub. ®
Sponsored:
HPC in the cloud: A solution for varied computing needs
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2016/05/26/palo_alto_ids_another_ccoverdns_attack/