Phishing campaign spoofs online auto brand, exposes stolen passwords
Falling for a phishing scam is bad enough. When the bad guys keep your stolen account on a site so riddled with security holes that anyone can peek through, it’s like rubbing salt into the wound.
Researchers from SophosLabs found just such a site when investigating a phishing campaign that spoofed the site of mobile.de – the largest online vehicle marketplace in Germany.
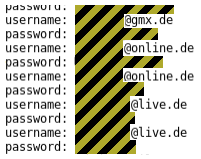
Those managing the phishing site in question left its directory open for browsing, allowing anyone who gets there to see the usernames and passwords of phished accounts. The result is that the passwords stolen by the first group of thieves could have already been stolen again by someone else.
RELATED PODCAST: Phishing – How this troublesome crime is evolving
What happened
The campaign SophosLabs investigated was a classic case of phishing by SMS, the text messaging service component of most mobile phones. Though people have gotten better at not falling for traditional phishing scams that come by way of email on laptops and desktops, they remain susceptible to SMS phishing. Phones come with little or no security for anti-phishing except for what is provided by the vendor, like Safe Browsing in Chrome. And messages arrive on smaller screens, which makes it harder to spot forgeries.
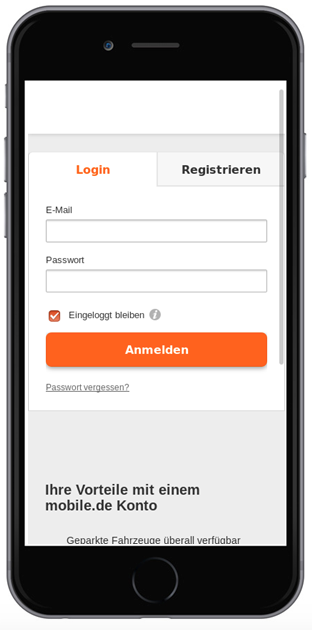
In the case of this campaign, users who clicked the link in the SMS message were taken to a fake log-in page that looked like this:
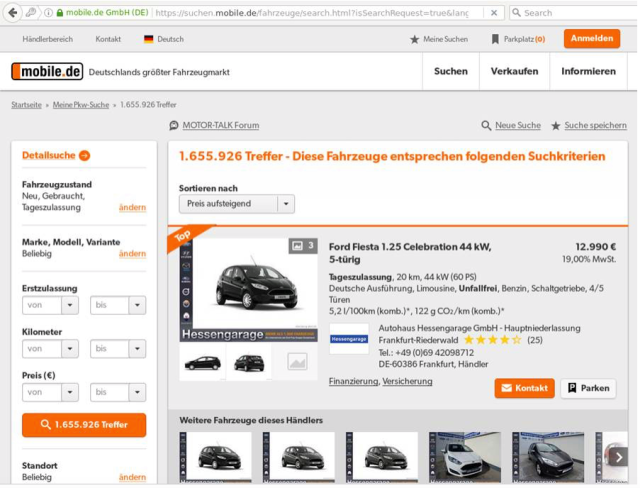
User who entered their credentials were moved along to the real site:
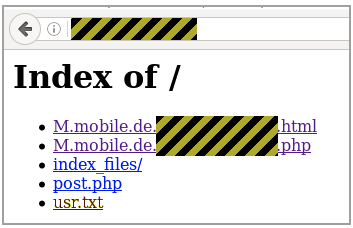
When SophosLabs researchers traced the activity back to the phishing site where stolen credentials were stored, they discovered that its root directory was open for all to see.
At one point the directory contained 210 accounts. That could have been the tip of the iceberg, because it was one of what was probably several sites used in the attack.
What to do?
The key to not ending up on one of these exposed sites if to avoid getting phished in the first place. The first step in defending one’s self is to be more aware that mobile malware is a growing danger and that everything we’ve learned about phishing protection must be applied to these smaller devices.
Sophos is now protecting customers from this campaign. But some additional advice is in order:
- Don’t be misled by domain names because they start with the text you expect – it’s the right-hand end of the URL that counts.
For example, Sophos owns sophos.com, which means we can use any and all subdomain names that end with that text string, such as partners.sophos.com, nakedsecurity.sophos.com, and so on. Many browsers deliberately highlight the text at the right-hand end, to remind you to look there first.
- If you’re asked for personal data like your address and credit card number on an unencrypted web page, don’t enter it.
Crooks can easily get certificates for HTTPS these days, so just the presence of a padlock in the address bar doesn’t confirm you are at the right site. But the absence of a padlock on a page that wants a credit card is always wrong, even if it’s the right site. (Why trust a company that clearly doesn’t take even the most basic precautions with your personal data?)
- Report scams and dodgy SMSs like this to your mobile operator.
Having real reports and genuine complaints “from the wild” makes it possible for the regulator to take action against scammers who might otherwise get away with it. Some scams are on the grey edge of legality, and it’s community consensus that helps the regulators redefine the boundaries of acceptable text messaging behavior.
Follow @NakedSecurity
Follow @BillBrenner70
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/60oqjnioq3U/