Phishing via SMS – crooks target Australian mobile banking users
For better or for worse, most of us are familiar with bank-related phishing.
That’s where a crook tricks you into clicking a link that looks as though it belongs to your bank, and then presents you with one or more login screens that look like your bank.
The idea is that by making the experience seem familiar enough, and look realistic enough, you will simply “do what you usually do,” filling in the requested fields and clicking [Next].
We’ve written many times about this sort of trickery, along with lots of advice to help you avoid it.
💡 LEARN MORE – PHISH 1: iTunes ►
💡 LEARN MORE – PHISH 2: Online banking ►
💡 LEARN MORE – PHISH 3: Bitcoin ►
It’s easy to get sucked in if you aren’t paying attention, because it’s easy for the crooks to clone the look and feel of the bank’s real site by simply copying and lightly modifying the bank’s own web pages.
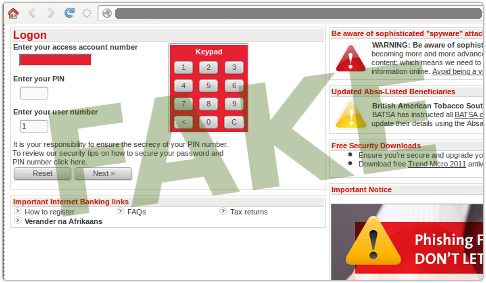
In the phishing attack you see here, for example, against South African bank ABSA, the crooks created a pixel-perfect clone of the login fields, and replicated the fraud prevention warnings of the real site:
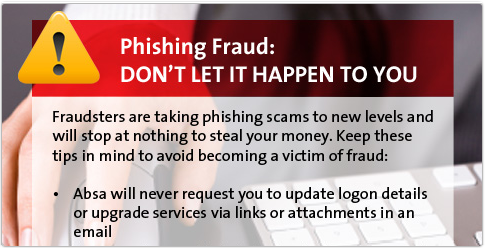
Even ABSA’s anti-phishing notice was cloned, and, in a neat irony, would take you to the bank’s real anti-phishing page if you clicked on it:
The good news is that even though phishing is still lucrative for the crooks, we are getting a lot better at not falling for it, at least for old-school phishes that are delivered in emails and require you to click through into a browser window.
WHAT ABOUT MOBILES?
But what about mobile devices?
The Australian Communications and Media Authority (ACMA) has recently warned that cybercrooks are make what looks like a concerted effort to target Australian financial institutions via a rather different route.
Instead of getting an email that takes you to a site in your desktop browser, the phish starts with a simple SMS that links to a believable-looking server name, much like this (we have altered the links so they don’t appear suspicious):
Account notification: http://yourbank.example.com 1 new Secure Email http://mobile.bank.example Your online statement is ready http://m.bank.test/
You ought to be suspicious already, not only because most banks simply tell you that your statement is ready, and leve you to use a bookmark of your own to get there, but also because all the sites use HTTP, rather than its secure cousin, HTTPS.
But all the usual phishing signals you might look for in an email are missing, especially if you know how to look at the headers of an email, which give you hints as to where it really came from, rather than where it said it came from.
And in the cramped confines of an SMS, there’s little chance for the crooks to make spelling mistakes or grammatical blunders.
An message that said nothing more than “Account notification” would seem unusually abrupt and suspiciously unprofessional in an email, yet it reads perfectly naturally in an SMS.
If you were to click through to one of the many phishy domains the crooks have registered for these attacks (ACMA has an extensive list on its site), you’d put yourself in harm’s way.
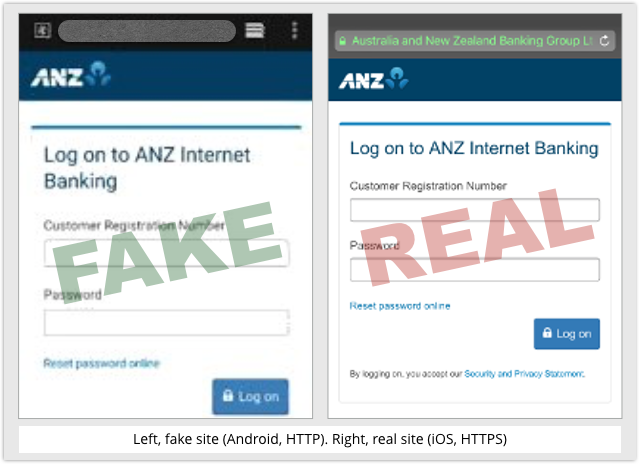
Here’s ACMA’s example screenshot for the fake login page for the ANZ bank, next to the real thing:
WHAT TO DO?
- Don’t throw caution out of the window when you switch from your desktop or laptop to your mobile device.
- Avoid clicking on links in SMSes, especially if they are unsolicited.
- Learn how to tell when a page is using HTTPS in your mobile browser of choice.
Your mobile device isn’t more secure simply because it’s not the same as, or newer than, or runs a different operating system to, your desktop or laptop.
Whether you are on your phone or your laptop, your tablet or your desktop, if you put your personal information or password into the wrong site, it will end up in the wrong people’s hands…
Follow @NakedSecurity
Follow @duckblog
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/C5UKUKgpwQ4/