Please don’t spread the Facebook "giraffe picture" hoax!
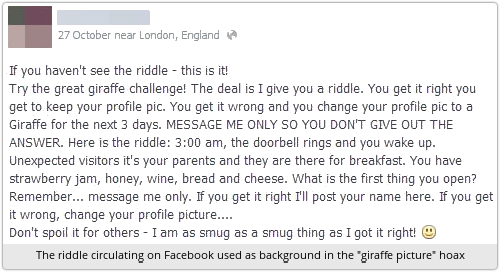
 A bizarre warning is circulating on Facebook urging you not to change your profile picture to a giraffe.
A bizarre warning is circulating on Facebook urging you not to change your profile picture to a giraffe.
When I heard about this, my first reaction was, “Of all the things I could choose to represent myself, what’s the chance that today I’d suddenly want it to be a giraffe?”
My next thought was, “But if I were to decide on a giraffe – and they are majestic animals, let’s face it – why would that be a problem?”
The whole thing is a load of rot, of course, and just the latest in a long line of internet hoaxes.
The advice in the hoax
The bogus reasoning in the hoax is somewhat contorted, but it seems to go something like this:
- There’s a Facebook game in which players who fail to answer a riddle correctly are urged to set their picture to a giraffe as a harmlessly light-hearted signal they got it wrong.
- Crooks have tried to take advantage of this by poisoning Google’s image searches with booby-trapped giraffe images.
- These booby-trapped JPEG files install malware with a range of dangerous side-effects, including stealing your username and password.
- So don’t change your profile picture to a giraffe.
There’s enough here to be mildly believable: readers may have heard of the riddle that asks you to change your profile picture if you get it wrong; search engine results can be manipulated by cybercriminals; and software bugs have been found in the past that allowed booby-trapped JPEG files to deliver malware.
Why it isn’t true
It’s all a pack of made up rubbish – and here’s how you can tell.
Way back in 2004, a lot of media coverage was given to a JPEG vulnerability in the heart of Windows.
This security hole could, in fact, have allowed booby-trapped images on web pages to inject malware onto your computer, in the same way that booby-trapped DOC and PDF files are often used for that purpose these days.
Patches from Microsoft headed off that vulnerability at the pass with security update MS04-028, but the concern at the time was understandable, since the JPEG format was, and still is, one of the most commonly-used image types on the internet.
Indeed, if you dig around online for nine-year-old stories aobut the MS04-028 vulnerability, you will find articles like this one:
A virus that exploits the recently discovered JPEG vulnerability has been discovered spreading over America Online’s instant-messaging program….
“It’s been done in the past, but with HTML code instead of the JPEG,” said Johannes Ullrich, chief technical officer for SANS’ Internet Storm Center, the organization’s online-security research unit. “It is a virus, but it didn’t spread very far. We’ve only had two reports of it.”
…The code also installs a back door that can give hackers remote control over the infected computer. Antivirus expert Mikko Hypponen of F-Secure warned on Wednesday that the JPEG exploit can also dodge antivirus technology.
Guess what?
According to the Hoax-Slayer website (which has itself been around since 2003), the current hoax tells much the same story, with some minor changes in detail, and some deliberate mis-identification of the “experts” being quoted (my emphasis):
A virus that exploits the recently discovered JPEG vulnerability has been discovered spreading over google’s giraffe pictures.
“It’s been done in the past, but with HTML code instead of the JPEG,” said James Thompson, chief technical officer for SANS’ Internet Storm Center, the organization’s online-security research unit. “It is a virus, but it didn’t spread very far. We’ve only had two reports of it.”
…The code also installs a back door that can give hackers remote control over the infected computer. Antivirus expert Fred Hypponen of F-Secure warned on Wednesday that the JPEG exploit can also damage your Iphone if you charge it with your computer.
Johannes Ulrich, quoted back in 2004, is still the Internet Storm Center CTO, not James Thompson.
And although F-Secure’s best-known antivirus expert is indeed – today as in 2004 – a certain Mr Hypponen, his first name is Mikko, not Fred.
Adding a modern twist
The introduction of the warning about charging your iPhone gives the old story a bit of a modern twist, and takes advantage of a recent expose about the potential risk to iPhones (now patched) posed by booby-trapped chargers.
The current hoax apparently also adds a bogus detail to say that:
By default, antivirus software only scans for .exe files. And even if users change the settings on antivirus software, the JPEG file name extensions can be manipulated to avoid detection.
That’s not true either.
An on-access (real time) virus scanner – the component that prevents virus infection by blocking files before they open – will generally identify files by their content, meaning that the extension is largely irrelevant.
And if you change the settings on your on-demand scanner, you can just set it to check all files, which makes misapplied extensions irrelevant.
As you can see, there are lots of signs that this “giraffe story” is entirely bogus.
→ If it were true, and a vulnerability were currently known that would let JPEGs inject malware onto your computer, then the crooks wouldn’t bother going to all the trouble of poisoning Google image searches and hoping you would change your Facebook profile. They’d just put the booby-trapped files onto innocent-looking web pages and infect you during normal browsing, wouldn’t they?
What to do?
Our advice:
- If you’re a news writer who covers computer security, check your facts before you endorse security warnings: false alarms just make us collectively less likely to react when there is a problem.
- If you’re a reader of security warnings, don’t spread this hoax, even if you think it’s amusing: false alarms just make us collectively less likely to react when there is a problem.
Image of giraffe warning sign courtesy of Shutterstock.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/H4SeNybovw8/