SEA hits CNN, may be linked to Microsoft law enforcement info heist
 Microsoft has admitted that spearphishers compromised email accounts at the company, potentially leaking documents “associated with law enforcement inquiries”.
Microsoft has admitted that spearphishers compromised email accounts at the company, potentially leaking documents “associated with law enforcement inquiries”.
Just the previous week we had heard how accounts operating Microsoft’s social media effort were hijacked by the Syrian Electronic Army, with official Microsoft Twitter feeds used to tweet out the SEA’s usual political gripes.
Just the day before Microsoft revealed the legal data loss, the SEA made another strike, this time targeting news outlet CNN.
Several Facebook accounts, Twitter feeds and blogs run by CNN were apparently compromised, and some were used to send out messages questioning the accuracy of CNN’s coverage of recent events in Syria.
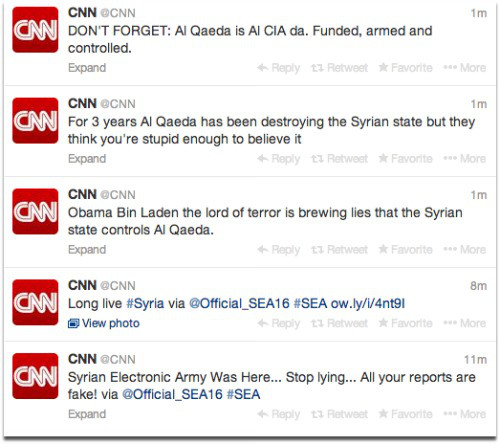
The rogue tweets were only visible for “minutes”, according to CNN itself, who also mentioned in passing that the SEA’s disruption of fellow news outlet the New York Times last August took twenty hours to rectify.
The rather vague wording of the MS blog post on the latest compromise led many to assume the leaked documents came from the same account hijacked for the SEA Twitter hijinks.
That would mean someone with access to social media accounts was also handling legal paperwork – a rather odd division of labour to say the least.
However later comment from Microsoft to SecurityWeek clarifies that the two are separate incidents, but appear to be related.
The documents that are thought to have been stolen sound like requests for information from police or other agencies – the sort of thing totted up in annual transparency reports.
This kind of data would be of considerable value to the right person, anyone subject to a request for covert information on their online behaviour being an obvious starting place. It’s not really clear quite what the SEA would want with such documents though, other than the chance to show off its talent for breaching accounts.
By all accounts, the bulk of the SEA’s successes has been down to social engineering and accurate spearphishing – tricking people into handing over passwords rather than any more technical hackery.
This makes it three compromises in a month for Microsoft, after the takeover of its Skype Twitter feed at the turn of the year, again by the SEA.
It seems remarkable that big firms with large marketing budgets are unable to train their staff to be more careful with public-facing accounts.
Two-factor authentication may be problematic for accounts shared between many people, possibly in many locations, but there are still plenty of things people can do to minimise their likelihood of passing on login details to the wrong sort.
The main weapon against human-focused attacks is awareness of the danger and familiarity with the main tricks and techniques social engineers use.
One would think that any company making use of social media would by now be aware of the potential embarrassment digital graffiti and political sloganeering can cause, and would pass that awareness on to whoever has access to account passwords in the strongest possible terms.
Another potential angle is policy. It shouldn’t be beyond the wit of corporate-grade password management software to auto-fill passwords only when accessing the right URL, on an approved browser or app and via a trusted connection, without giving the user any way of seeing the password itself.
This approach should cut out the human element entirely, and make access to company social media accounts part of access control procedures.
Still plenty of room for human error there too of course, and certainly not a guarantee of complete safety as there will surely be technical ways to bypass such a system, but it could at least force the likes of the SEA to work a little harder.
Follow @VirusBtn
Follow @NakedSecurity
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/1RvDVpMnbRQ/