Spam from an anti-virus company claiming to be a security patch? It’s Zbot/Zeus malware…
Julie Yeates of SophosLabs (thanks Julie!) alerted us earlier today to a spam campaign that seemed to originate from a whole raft of different security and anti-virus companies.
The messages have a variety of subject lines, such as:
Windows Defender: Important System Update - requires immediate action AVG Anti-Virus Free Edition: Important System Update - requires immediate action AVG Internet Security 2012: Important System Update - requires immediate action Kaspersky Anti-Virus: Important System Update - requires immediate action Microsoft Security Essentials: Important System Update - requires immediate action
The emails are all very similar, claiming to include an important security update to deal with “the new malware circulating over the net”.
The parts shown in pink above vary from email to email, but the bulk of the content stays the same:
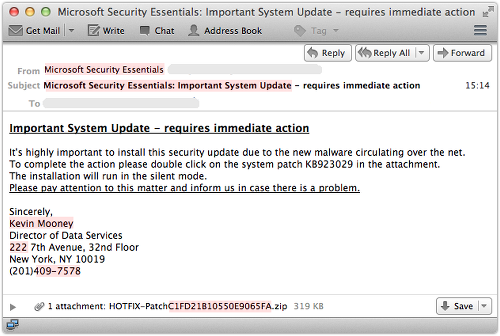
Important System Update – requires immediate action
It’s highly important to install this security update due to the new malware circulating over the net. To complete the action please double click on the system patch KB923029 in the attachment. The installation will run in the silent mode. Please pay attention to this matter and inform us in case there is a problem.
The email doesn’t explicitly mention the CryptoLocker ransomware that locks your files and tries to sell them back you.
But there is little doubt that many recipients, having heard of the ongoing saga of CryptoLocker, will be more inclined than usual to read on.
It’s all a pack of lies, of course.
There is no “system patch KB923029,” and even if there were, neither Microsoft nor any other reputable company would send out security updates as email attachments.
Also, if you are a native speaker of English, you should spot a number of niggling errors of usage and grammar in the text of the email.
→ The fact that an email is grammatically flawless, in English or any other language, is not an indicator of legitimacy. But language blunders in English, in an email purporting to come from the New York office of a legitimate software company, are a strong indicator of bogosity. If the crooks can’t even be both to trying rite and spel decent, you may as well use their linguistic sloppiness against them.
The ZIP file contains an EXE (a program file); that program file is one of the many variants of the Zbot malware, also known as Zeus, that we see on a regular basis.
You’re expected to open the ZIP and run the program inside, which has a name like this:
HOTFIX_patch_KB_00000...many digits...56925.exe
There’s nothing wrong with having an EXE inside a ZIP file.
But a ZIP that contains only an EXE, and that was delivered by email, is just as suspicious as a plain EXE that arrives as an attachment.
If you do run it, the EXE installs itself into:
C:Documents and Settings%USER%Application Data
with a random filename, and adds itself to the registry key:
HKEY_CURRENT_USERSoftwareMicrosoftWindows CurrentVersionRun
so that it gets launched every time you reboot or logon.
We shouldn’t need to remind you, but we’ll do so in case you want to remind someone else:
- Don’t open email attachments you weren’t expecting.
- Don’t believe emails that claim to be sending you a security patch – by email.
- Don’t ignore clues such as poor grammar or spelling in emails that claim to be official.
- Don’t neglect to keep your software patches up to date – but never by email.
Note. Sophos Anti-Virus on Windows detects this malware proactively (and very likely a high percentage of related variants still to appear) as HPMal/Zbot-C. Sophos on non-Windows platforms, including gateway products, detects the malware’s various components as Troj/Agent-AEWF and Troj/Agent-AEWG. Sophos web and email filters proactively quarantine attacks of this sort by identifying the ZIP file as suspicious.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/tlodfOiTSmY/