Syrian Electronic Army returns with Thanksgiving press hack
 Yesterday, the Syrian Electronic Army (SEA) compromised a US customer identity management platform, Gigya, which is used by many high profile news websites.
Yesterday, the Syrian Electronic Army (SEA) compromised a US customer identity management platform, Gigya, which is used by many high profile news websites.
In a blog post, Gigya CEO Patrick Salyer explained how the hacker group accomplished its mission via DNS redirects:
At approximately 6:45 AM EST we identified sporadic failures with access to our service. An initial inquiry has revealed that there was a breach at our domain registrar that resulted in the WHOIS record of gigya.com being modified to point to a different DNS server.
That DNS server had been configured to point Gigya’s CDN domain (cdn.gigya.com) to a server controlled by the hackers, where they served a file called “socialize.js” with an alert claiming that the site had been hacked by the Syrian Electronic Army.
This meant that some, but not all, visitors to sites including CBC, CNBC, Forbes, OK magazine, The Chicago Tribune, The Daily Telegraph, The Independent and The New York Times were met with a message saying “You’ve been hacked by the Syrian Electronic Army (SEA).”
Other visitors were directed to an image of the group’s crest set against a black background.
The defacement seems to have been pretty short lived – a Naked Security reader reported a site that had shown him SEA material, and although we checked into it almost immediately, we found only the content we expected.
The SEA confirmed the attack via a tweet, which displays what appears to be a screenshot of the control panel for the Gigya.com domain at GoDaddy:
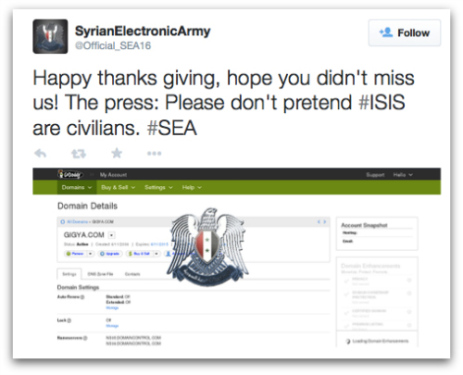
Happy thanks giving, hope you didn’t miss us! The press: Please don’t pretend #ISIS are civilians. #SEA
Salyer confirmed no user, administrator or operational data was compromised at Gigya and said the company has now put further security measures into place to ensure it is protected from another such attack in the future.
He also confirmed that DNS records had been restored but did note that the change may take some time to propagate across the whole of the internet.
The Telegraph tweeted to confirm the attack:
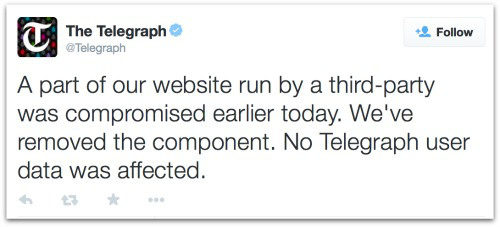
A part of our website run by a third-party was compromised earlier today. We’ve removed the component. No Telegraph user data was affected
The Independent also confirmed that “no user data is or was in jeopardy”.
The SEA has been relatively quiet lately but has previously been responsible for taking over a number of high profile Twitter accounts and websites.
Previous victims include The New York Times, Twitter, Skype, Forbes, the Israeli Defence Force and Viber.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Bl6dWxNwuvs/