Between KRACK, ROCA, new threats to SSH keys, and the European Commission’s loosey-goosey stance on encryption backdoors, it’s been a difficult time for cryptography.
BY DAWN KAWAMOTO AND SARA PETERS — This week started off with a bang when the KRACK key reinstallation attack vulnerabilities upended the security of Wi-Fi and the ROCA factorization bug made all trusted platform module chips suddenly less trustworthy. That isn’t all the week had in store for the cryptography world, though.
Here’s a rundown on the latest news on KRACK, ROCA, and the news you might have missed about SSH and encryption backdoor regulation.
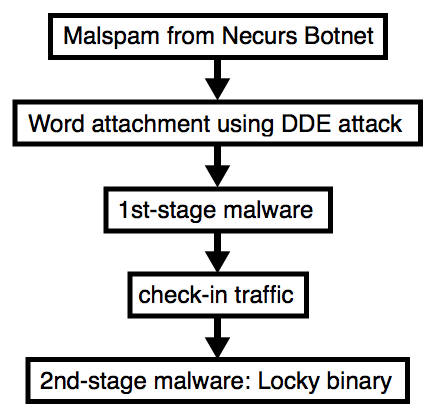
SSH Keys Being Scanned by Attackers and Ignored by Security
SSH (Secure Shell) got a little jolt this week, as well. Wordfence, a security service for WordPress, discovered a threat actor scanning up to 25,000 systems a day looking specifically for vulnerable private SSH keys. The attacker is specifically scanning for terms like “ssh,” “root,” and “id_rsa,” which might lead to a directory of private keys that was stored in the wrong place.
The rate of scanning for SSH keys from known-malicious IPs has continued at the same rate since Monday; roughly 25,000 systems per day, “which jumped up from just about zero,” according to Mark Maunder, CEO and founder of Wordfence.
In response, Wordfence is helping users determine if they have publicly exposed private SSH keys by adding this capability to their Gravity Scan service to users. Maunder says that users must prove site ownership before Gravity Scan will provide vulnerability details.
SSH is a ubiquitous but often overlooked cryptographic network protocol created largely as a secure alternative to telnet and rsh/rsec. It’s used for secure remote logins to remote computer systems and secure file transfer; it’s used not only for WordPress but across admin-to-machine and machine-to-machine communications in all manner of Linux- and Unix-based systems.
[Don’t miss “Preventing Lateral Movement in Your IT Environment” with John Terrill, CISO of OPAQ Networks, at Dark Reading’s upcoming INsecurity conference, Nov. 29-30 in the D.C. area.]
So far, Wordfence has not seen any active exploits as a result of this SSH key hunt. Maunder says that problems like this are often a result of users accidentally placing private keys in the wrong place because they don’t know it’s a risk. “It’s really an education problem,” says Maunder.
In a survey released Tuesday, conducted by Dimensional Research on behalf of Venafi, 90% of respondents conceded that they do not have a complete and accurate inventory of all their SSH keys, “so there is no way to determine if keys have been stolen, misused or should be trusted,” according to researchers.
The author of SSH, Tatu Ylonen, has himself lamented organizations’ woeful management of SSH keys and has suggested improvements to his protocol to eliminate problems like the proliferation of rogue keys. For now, though, respondents to Venafi’s study continue to commit the key management sins that SSH experts warn against. Forty percent of respondents do not rotate SSH keys at all, or only occasionally; 61% do not limit or monitor the number of administrators who manage SSH; 54% do not limit the locations from which SSH keys can be used (thereby making remote attacks easier); and 51% do not enforce “no port forwarding” rules (thereby effectively allowing users to bypass firewalls).
The Impact of KRACK
Key Reinstallation Attacks (KRACKs), which affect all modern Wi-Fi devices and access points, are hitting Cisco particularly hard. The networking giant released Thursday an updated security advisory on KRACK, noting 71 of its products had at least one or more of the 10 vulnerabilities tied to KRACK.
For Cisco’s customers using these products, there are currently no fixes available and only a workaround for one of the 10 vulnerabilities, the company notes.
“Cisco will release software updates that address these vulnerabilities. There is a workaround that addresses the vulnerability in CVE-2017-13082. There are no workarounds that address the other vulnerabilities described in this advisory,” the company stated.
In addition to the 71 products that are vulnerable to KRACK, Cisco has another 22 products it is actively investigating to determine if they are also at risk, the company notes.
Earlier this week, researchers at a Belgium university discovered the KRACK vulnerabilities in the Wi-Fi Protected Access II (WPA2) protocol that is used to secure Wi-Fi networks. These vulnerabilities can be exploited to allow attackers to decrypt data and information, hijack traffic, and other nefarious activities as the data and information moves across Wi-Fi networks.
The WPA2 encryption protocol flaws also have industry titans Microsoft, Apple, and Google hustling to develop patches for their devices, as TechCrunch reports.
Microsoft has a patch out for its Windows 7, Windows 8, Windows 8.1, and Windows 10 devices, but Apple is working to roll out a fix to customers and currently has a beta version of macOS, iOS, tvOS, and watchOS available for download, notes TechCrunch.
And while exact figures on the number of users who are affected by these KRACK vulnerabilities are not available, it would not be hard to envision millions of users could potentially be affected given the omnipresence of WPA2 encryption protocols in Wi-Fi devices.
The Electronic Frontier Foundation (EFF) released a few calming observations. One is that any attack would need to have an active antenna within range of the targeted wireless network and would require the interception and delay of many packets traveling on the Wi-Fi networks. The EFF states it’s a complex task to trick a device and reset its encryption key as packets are actively being broadcast. Additionally, sensitive Wi-Fi traffic would not be affected by the WPA2 vulnerabilities if the site is encrypted with HTTPS.
European Commission Discusses Encryption
The European Commission this week revisited the topic of encryption backdoors. The EC seemed to subtly say no to backdoors when releasing the statement that it would support law enforcement when it encountered encryption “without weakening encryption at a more general level or affecting a large or indiscriminate number of people.” However, its set of proposals to enhance law enforcement’s ability to obtain the electronic evidence it desires include “to support Europol to further develop its decryption capability.” It also stated that “in early 2018, the Commission will present proposals to provide for a legal framework to facilitate access to electronic evidence.” (Emphasis not added.)
ROCA Rocks
Another crypto vulnerability revealed this week includes The Return of Coppersmith’s Attack (ROCA).
The ROCA flaw is found in the PC motherboard chipset inside Infineon Technology’s Trusted Platform Module, which is used to store encryption keys, passwords, and certificates, reports Kaspersky’s Threatpost.
When an RSA encryption key is generated, a remote attacker uses the value of a public key to compute the private key by crunching the numbers through practical factorization, according to researchers with the Centre for Research on Cryptography and Security at Masaryk University in the Czech Republic, Enigma Bridge in Cambridge, United Kingdom, and Ca’ Foscari University of Venice, Italy. These researchers discovered the vulnerability.
Once the private key has been compromised, attackers can impersonate the legitimate owner, decrypt sensitive messages, engage in signature forgery, and other attacks, according to a blog post by the researchers.
The researchers discovered the flaws when inspecting a large number of RSA keys that were generated and exported from the manufacturer of smartcards. The group notified Infineon Technologies of the vulnerability in February and also reached out to other affected parties, such as, Microsoft, Google, HP, Lenovo, and Fujitsu, which have since released updates.
“We found and analyzed vulnerable keys in various domains including electronic citizen documents, authentication tokens, trusted boot devices, software package signing, TLS/HTTPS keys and PGP,” the researchers stated. “The currently confirmed number of vulnerable keys found is about 760,000 but possibly up to two to three magnitudes more are vulnerable.”
Researchers noted Friday that “Gemalto IDPrime .NET smart cards have been generating weak RSA keys since 2008 or earlier.” You can check if keys are vulnerable here.
Related Content:

Join Dark Reading LIVE for two days of practical cyber defense discussions. Learn from the industry’s most knowledgeable IT security experts. Check out the INsecurity agenda here.
Dawn Kawamoto is an Associate Editor for Dark Reading, where she covers cybersecurity news and trends. She is an award-winning journalist who has written and edited technology, management, leadership, career, finance, and innovation stories for such publications as CNET’s … View Full Bio
Article source: https://www.darkreading.com/vulnerabilities---threats/the-week-in-crypto-bad-news-for-ssh-wpa2-rsa-and-privacy-/d/d-id/1330187?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple