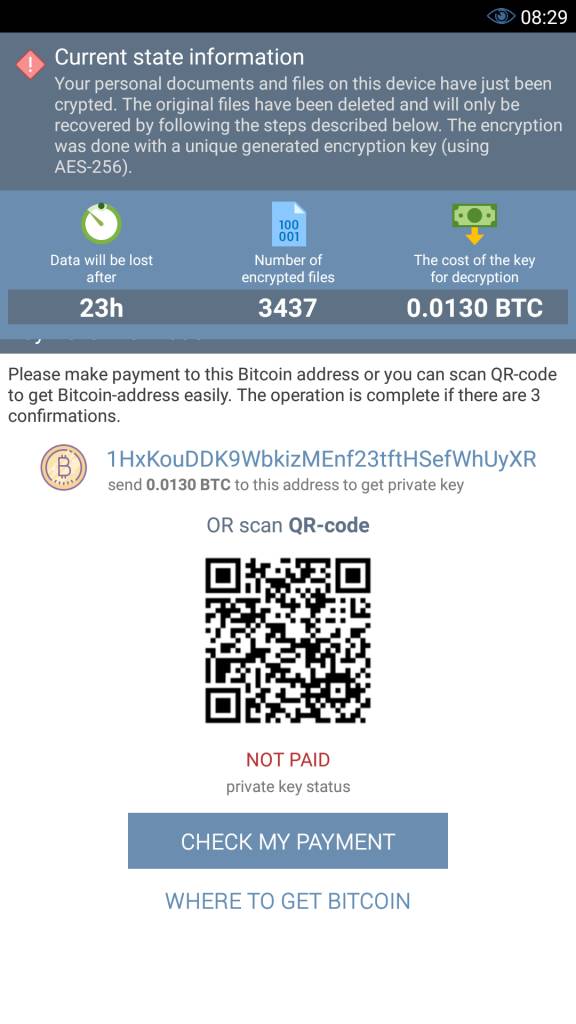
Hackers steal restricted information on F-35 fighter, JDAM, P-8 and C-130
Add the Australian Signals Directorate (ASD) to the already long list of organizations compromised by the security weaknesses of third-party contractors.
But in this case it wasn’t just credit card and other consumer data compromised. It was detailed information on some of the nation’s major military defence systems – aircraft, bombs and naval vessels.
The first mention of the breach came almost in passing and with few details, deep in the Australian Cyber Security Centre (ACSC) 2017 Threat Report. It said that almost a year ago, in November 2016, the ACSC:
…became aware that a malicious cyber adversary had successfully compromised the network of a small Australian company with contracting links to national security projects. ACSC analysis confirmed that the adversary had sustained access to the network for an extended period of time and had stolen a significant amount of data.
The report didn’t name the company, its size or what kind of national security work it did.
Turns out it should have been obvious that the company – a 50-person aerospace engineering firm with only one person handling all IT-related functions – was an obviously weak link in the security chain.
That and quite a bit more detail – although the company still remained unnamed – came earlier this week, from Mitchell Clarke, incident response manager at the ASD, in a presentation at the national conference of the Australian Information Security Association (AISA) in Sydney.
According to ZDNet correspondent Stilgherrian, who obtained an audio of the presentation, Clarke said the attacker(s), who had been inside the company’s network at least since the previous July, had “full and unfettered access” for several months, and exfiltrated about 30GB of data including, “restricted technical information on the F-35 Joint Strike Fighter, the P-8 Poseidon maritime patrol aircraft, the C-130 transport aircraft, the Joint Direct Attack Munition (JDAM) smart bomb kit, and a few Australian naval vessels.”
He said the attackers, who used a tool called China Chopper, could have been state sponsored or a criminal gang.
And they likely had little trouble gaining access.
Clarke, who named the advanced persistent threat (APT) actor “APT ALF” after a character in an Australian television soap opera Home and Away, said besides the single IT employee, who had only been on the job for nine months, the “mum and dad-type business” had major weaknesses:
There was no protective DMZ network, no regular patching regime, and a common Local Administrator account password on all servers. Hosts had many internet-facing services.
Access was initially gained by exploiting a 12-month-old vulnerability in the company’s IT Helpdesk Portal, which was mounting the company’s file server using the Domain Administrator account. Lateral movement using those same credentials eventually gave the attacker access to the domain controller and the remote desktop server, and to email and other sensitive information.
Beyond that, Clark said the firm’s Internet-facing services still had their default passwords of admin and guest. He called the months between when the hackers gained access and their intrusion was discovered, “Alf’s Mystery Happy Fun Time.”
The Age reported that a spokesperson for ACSC said while the data was “commercially sensitive,” it was not classified.
But Clarke said among the stolen documents was one that, “was like a Y-diagram of one of the Navy’s new ships and you could zoom in down the captain’s chair and see that it’s one metre away from the nav (navigation) chair and that sort of thing.”
Whatever the sensitivity of the data, it seems certain that the breached firm wasn’t following what the ASD calls the “Essential Eight Strategies to Mitigate Targeted Cyber Intrusions.”
The agency said while no strategy is guaranteed to prevent cyber intrusions, simply implementing the “Top 4” would block 85% of adversary techniques. They amount to what most security experts, and regular readers of Naked Security, will recognise as basic security hygiene:
- Use application allow lists so only run approved programs
- Patch applications like Flash, web browsers, Microsoft Office, Java and PDF viewers
- Patch operating systems
- Restrict admin privileges based on user duties
According to ASD, those strategies have been mandatory for all Australian government organizations since 2013.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/iuBneke9n_o/