There’s a Toronto woman named Roxanne who has an on-again, off-again hobby. For the past four years, she’s spent her time reaching out to those whose photos, some explicit, she’s found on a site dedicated to titillating men by, among other things, humiliating women by posting their stolen images and personal details.
As CTV News Canada tells it, Roxanne (who prefers not to use her full name, given concerns about her activities affecting her career in social work) learned that her own photos had cropped up on the image-sharing site Anon-IB.
People can post images anonymously on Anon-IB. In fact, its tagline boasts that it’s the “Best Anonymous Image Board”.
Yes, it’s sort of anonymous, but only in a lopsided way. As in, the people who post photos, many of them stolen or taken with hidden cameras, can do so anonymously. It’s certainly not anonymous for the women in the photos, though. They have no say when it comes to keeping their personal information off the site. Hell, nobody asked them if they wanted their photos posted in the first place.
Because the women in the photos are denied the luxury of anonymity, Roxanne is able to search for, contact, and warn them that their photos and personal information are on Anon-IB. To find the women in the photos, Roxanne uses information she gets from Anon-IB – their first names, the first letter of their last names, and the communities they’re believed to live in – to search for them on Facebook. In fact, the site lets users search for images by US state or by country. There are also pages dedicated to specific universities, and users often request highly specific nudes: “Hamilton hoes”, “Nanaimo Thread!”, “Markham wins”, or topless photos from a BC music festival called Shambhala or from a nudist beach in Vancouver that has a no-photos policy.
Roxanne has to admit, searching for them like this makes her feel like a bit of a creep. But at least she’s got their best interest at heart. Best to know how easily you can be found, she figures, before stalkers find you:
If I can track them down this easily, somebody with a worse motive can too.
The site caters to the typical hodgepodge of fetishes, but as you can see in its category list, it has no qualms about letting users post photos that they’ve captured via photo-stalking – be it through surveillance videos, downblousing, or upskirting:
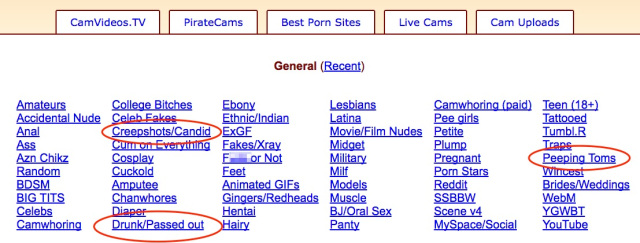
Plus, in spite of a ban on photos of the under-aged, there appear to be photos of children on the site, Roxanne notes.
Roxanne’s photos – in them, she was wearing underwear and a crop top – had been socially engineered out of her by somebody wielding a fake Facebook profile. The person had claimed to be a queer feminist, survivor of sexual violence and women’s studies student called Mary.
A few years after Roxanne shared her photos and grown suspicious of “Mary’s” increasing demands for more explicit images, the photos were posted to a sub-forum on Anon-IB titled “wins”. That’s slang for nude photos. She found out about it when a friend gave her a heads-up.
How is it that a site like this hasn’t been shuttered? As it is, the site prohibits the posting of images of minors and bans posting “personal details like addresses, telephone numbers, social networks links, or last names”. But as CTV News found, users pull a run-around by posting messages that contain the women’s first names, plus the first letters of their last names, plus what word their last names rhyme with. As in,
[First name], L., anyone? Surname rhymes with mammoth.
It isn’t as if law enforcement hasn’t managed to shut down other creep sites. Hunter Moore got more than two years in prison for his revenge porn activities. A henchman who stole photos to sell to Moore got two years himself.
But when Roxanne approached the police about her own photos, the officer “just looked bewildered,” she said. According to CTV News, York regional police said they’re aware of Roxanne’s case, that the force is still investigating, but that there have been no charges filed. Other Canadian police forces have investigated occasional complaints about the site, but likewise, no charges have been made by either the Royal Canadian Mounted Police (RCMP) in Antigonish, Nova Scotia, or by police in Peterborough, Ontario.
Of course, it’s pretty tough to complain about a site if you’re not even aware that your photos are posted on it. And it’s not uncommon for police to look baffled at the notion of prosecuting such a site. Revenge porn laws, where they exist at all, have only been added in recent years.
Canadians are protected under the Protecting Canadians from Online Crime Act, which makes it a crime to post or distribute an “intimate image” of another person without their consent. Whether the officer Roxanne was speaking to even knew about that law is an open question. At any rate, given that she was wearing her underwear, the photos wouldn’t be considered explicitly sexual, a lawyer told CTV News.
A Toronto-based lawyer, Jordan Donich of Donich Law, told VICE that these sites have been around for a long time. The current domain for Anon-IB was registered to a “private person” in 2015, though it was up for several years before that and went offline briefly in 2014. When it reported on the site last week, Vice noted the domain ended in “.ru.” As of Saturday, however, it ended in “.la,” the top-level domain for Laos.
The shell game of hosting such a site offshore, be it from Russia, Laos or elsewhere, makes it tough to investigate and prosecute the administrators, Donich said:
The people who organize these communities set up hubs in other jurisdictions, so Canadian law isn’t even applicable or enforceable a lot of times.
Roxanne had sent requests to take down the photos, but they were ignored. For whatever reason, after that lull in 2014, they weren’t reposted.
What can be done about sites victimizing women with stolen photos? For one thing, we can stop the photos from being taken or shared in the first place. These steps can help to protect your images:
- Don’t click on links in email and thus get your login credentials phished away.
- Use strong passwords.
- Lock down privacy settings on social media (here’s how to do it on Facebook, for example).
- Don’t friend people you haven’t met on Facebook, and don’t share photos with people you don’t know and trust. For that matter, be careful of those who you consider your “friends”. There are photos on Anon-IB posted by users who say they’ve been taken from Instagram feeds of “a friend”.
- Use multifactor authentication (MFA) whenever possible. MFA means you need a one-time login code, as well as your username and password, every time you log in. That’s one more thing the scumbags need to figure out every time they try to phish you.
So there’s that. That’s what’s we do all the time: we put the onus on women. We tell victims how to not be victims. It’s good advice, for any gender, to avoid having images stolen and accounts compromised. But it sure doesn’t help when photos are taken surreptitiously, without permission.
Like, say, when male Marines, Navy corpsman and British Royal Marines put up a private Facebook group – “Marines United” – to swap nude photos, some taken without their female colleagues’ knowledge.
Which brings us to putting onus where it belongs: on the creeps themselves.
Laws should help, but they often don’t. Beyond the difficulties in international investigations and prosecutions, in many places, laws haven’t even caught up with the age of mobile phones.
For example, it should be illegal for anybody to stick their camera-holding hand between women’s legs and take photos of their crotch/underwear/genitals without permission.
That’s commonly referred to as upskirting. It’s hard to imagine that such a harassing violation of privacy is legal anywhere, but it is. In the US, the legal situation is a patchwork of state laws: for example, upskirting was legal in Georgia until just a few months ago.
Upskirting is also perfectly legal in England. That will hopefully change soon: 25-year-old Gina Martin, a woman who was victimized last month at the BST Festival in London’s Hyde Park, has already garnered tens of thousands of signatures on a petition to make upskirting illegal.
I was targeted by a creep, who put his hand between my legs and took pictures of my crotch without me knowing. 📱😔 I gave the police the phone, the picture and the guy… and they closed my case. 🗄And told me that if I hadn’t been wearing knickers they might have been able to do more. 👗👚👙I started a petition to get him prosecuted and it now has 53,000 signatures. 👫👭👬Now, the fight has changed. I’m campaigning to get upskirting listed as a Sexual Offence and I need your help. 💭♥️ ✍🏽Sign the petition, share it with the women in your life and listen out, because soon i’m going to need your help to push our MP’s to make a change. 🤜🏼💥🤛🏽 Let’s do this, girls. 📣❤️ What you’re wearing should have nothing to do with how you’re treated. You are NOT the stylist of your own abuse. 😤🤛🏽 Link is in my bio. ☝🏻☝🏻☝🏻
A post shared by Gina Martin (@beaniegigi) on Aug 8, 2017 at 12:36pm PDT
And before anybody goes blaming women for not wearing knickers, or for wearing low-cut blouses, or any of that victim-blaming nonsense, bear in mind that these bozos will steal the most chaste of turtleneck/maxi-skirt photos and doctor them to appear as if the women are nude. It’s the people taking, creating and sharing the images who are to blame, not their victims.
That’s what happened to an underage girl who was tormented for months by an online sextortionist who stole iCloud backups of her perfectly innocent, fully clad dance videos, edited them to grab random shots – say, an elbow – and did a copy-paste job to make it look like they were nude videos.
(They got him. Or, rather, somebody arrested on suspicion of being behind the “Brian Kill” alias used by the sextortionist. The FBI used a booby-trapped video to do it.)
Similarly, an Anon-IB poster stole and doctored photos from one woman whom Roxanne managed to inform: “Katelyn”. Katelyn said her photos were taken from Facebook and from an online dating profile and edited to make her light-colored shirts appear see-through.
What lesson learned do we take away from that? “Don’t wear light-colored clothing?” Stay offline completely? Maintain a 10-mile no-camera/no mobile phones/no drones radius around our persons at all times?
Or do women have to mobilize, as have Roxanne and Gina Martin, to take it into their own hands when it comes to passing legislation and/or reaching out to inform the subjects whose images have been stolen?
Guys will be guys, they say. But police will be police, too. The best possible situation is when police know what’s legal and what’s not, make an effort to inform victims of obviously illegal photo-stealing, and make an effort to arrest the thieves.
In the past few years, the FBI infamously used a legally tainted tool to get to those who share illegal photos. I’m referring to the malware the FBI inflicted on 8,000 computers worldwide in the Playpen child abuse images investigation. The FBI was criticized for that.
The same technique – the FBI’s so-called Network Investigative Technique (NIT), also known as police malware – can be used in a more targeted fashion, as it was in the “Brian Kil” investigation.
The investigative tools are there. Granted, in order to go after photo thieves, the victims first need to know that they’ve been victimized: tough to do when the posting is done anonymously.
Similarly, it was a former Marine who initially discovered the revenge porn site Marines United, monitored it, and spent more than a month, near-daily, reporting offending images and groups. Another former Marine, Erin Kirk-Cuomo, runs a Facebook group Not in My Marine Corps as a support network for women affected by Marines United.
It’s not just down to ordinary people: technology such as facial recognition can be put to work. It’s facial recognition that’s being used in the sprawling Marines United revenge porn investigation, which had led to 21 felony cases as of May.
More than a dozen military members, mostly women, have asked the task force whether any of their intimate photos wound up on what are largely private sites without their consent. Facial recognition had helped match up four potential victims as of May, one of whom confirmed that a photo was of her, and another three that were still getting checked out at that time.
The laws are slowly, stutteringly coming on to the books. The technical tools are out there. Let’s hope they’re slowly putting an end to sites such as Anon-IB and others like it.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/coZzx8Q7zDM/






