ATM crooks up the ante by using infrared to steal your PIN
When we think of infrared technology, our minds go in many different directions at once as we march through the variety of uses for infrared. For those who follow the myriad television crime dramas, their minds no doubt go to the use of infrared photography at crime scenes. For those who are birdwatchers, infrared video can capture the hummingbird’s expenditure of energy. For most us, we think of the remote control which connects us from our couch-potato position to our television.
Well, there’s one more to add to this list – use of infrared video to transmit data captured at your bank’s ATM by criminals wishing to clone and use your bank cards.
The newfangled ATM skimmer was found in Norman, Oklahoma and according to the Norman police department, the device which they discovered in June 2017 was wafer-thin and undetectable by the victim. This skimmer had an antenna attached which served to broadcast the collected information to a tiny camera, which had visibility of the ATM’s keypad.
Security investigative reporter Brian Krebs dug a bit deeper into this skimmer and learned that these criminals had mastered, using infrared technology, to not only transmit the data captured by the skimmer, but also to transmit the accompanying keypad video.
The criminals showed a great deal of technological acumen and savvy in their use of infrared.
Infrared for data transfer is not new
Using infrared as a means to transmit data has been around for many years and is a highly efficient means to transmit at speeds many magnitudes faster than both Bluetooth and WiFi.
Furthermore, the use of an infrared transmitter greatly reduces the odds of having their transmissions inadvertently detected, when compared to WiFi or Bluetooth, which is present on every smartphone.
The criminals had only placed themselves at risk during time they put the device and video camera in place (Krebs has posted a photo of the two Oklahoma suspects), and when receiving the infrared signal (being in proximity to the ATM).
You’d have thought the criminals were Cold War history buffs, as their use of the concept of collect, store and forward data was previously perfected by the Russians. The KGB doctored several electric typewriters within the US embassy in Moscow in the 1980s which stored the key strokes and then used signal bursts to send the data to listening posts nearby. The implants were, like the ATM skimmers, deeply embedded in the hardware of the typewriter.
Available information doesn’t tell us if these ATM skimmer devices used directed or diffused infrared, a point of interest from a defensive standpoint. If the criminals used directed infrared, then their data collection point was within line of sight of the infrared transmitter – in other words, they would have to see the ATM, and thus could be seen from the ATM.
If their infrared signal used diffused infrared, then their collection point need only be in signal proximity, as the signal is more forgiving to line-of-sight disruption and therefore, a bit harder to observe.
The ever-reducing costs of readily available component parts make these devices essentially throw-away devices. Run the device for as long as the internal battery provides energy, and then move on.
What can the financial institutions do?
- Review the video at their ATMs with regularity – in this instance, it appears that the criminals were visible on video at the ATM but do not conduct a transaction.
- Install touchless technology, like NFC (near field communications), which will enable users to use their EMV/NFC debit/credit cards, key fob or smartphone to access their accounts.
- Or as has recently been implemented in Macau, by the Macau Monetary Authority, “Know Your Customer” technology requires that each ATM use facial recognition technology.
What should we do?
The low-tech solution is to cover your keyboard hand with a newspaper or your other hand when entering your pin codes – which will certainly stop anyone sneakily filming you as you tap in your PIN.
Follow @NakedSecurity
Follow @burgessct
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/5SXz5wCYxM8/
 Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the
Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the 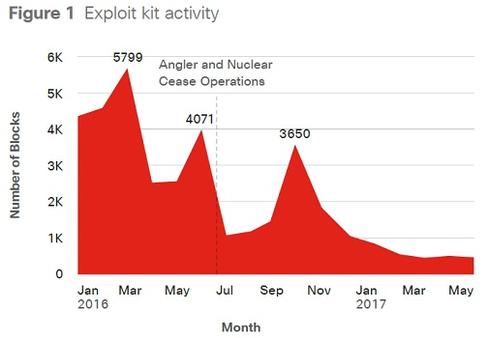 [Source: Cisco 2017 Midyear Cybersecurity Report]
[Source: Cisco 2017 Midyear Cybersecurity Report] Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the
Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the