Thanks to Dorka Palotay and Fraser Howard of SophosLabs for their behind-the-scenes work on this article.
A few readers have asked us about a ransomware variant with the intriguing name of Mole.
Interest seems to have been sparked by a recent security advisory from CareCERT, the cybersecurity initiative set up for the UK’s National Health Service (NHS), currently the world’s fifth largest employer.
(You know you want to ask, so we’ll answer. Depending on whom you consult and how you count, the list goes something like this: US Department of Defense, PRC People’s Liberation Army, Walmart, McDonalds, NHS.)
With cyberattacks on hospitals getting huge publicity in recent years, it’s not surprising that the UK’s healthcare CERT wants to keep its constituents on their toes when it comes to fending off ransomware attacks.
Ransomware is probably the most in-your-face sort of malware ever devised: when it triggers, it immediately scrambles all your data files, sends the decryption key to the crooks, and offers to sell the key back to you.
Unless the crooks are lazy or have made a programming mistake, they end up with the only copy of the decryption key…
…so if you don’t have a recent backup, you may have little choice but to try to do a deal with the crooks to buy back the decryption key. (Sometimes, the crooks mess that part up, so even if you do pay the extortion money, you might end up with nothing anyway.)
How Mole starts off
Typically, ransomware attacks start with an email that tries to threaten, cajole or simply just sweet-talk you into running a malicious file that’s supplied by the crooks, shipped in from outside your network.
Just the sort of email or web link, in fact, that you really ought to treat with sufficient distrust to delete it without opening or clicking on it.
Nevertheless, the crooks often hit their target by using with emails that are mundane and unexceptionable enough that opening them up feels harmless – like this one associated with the Mole ransomware:
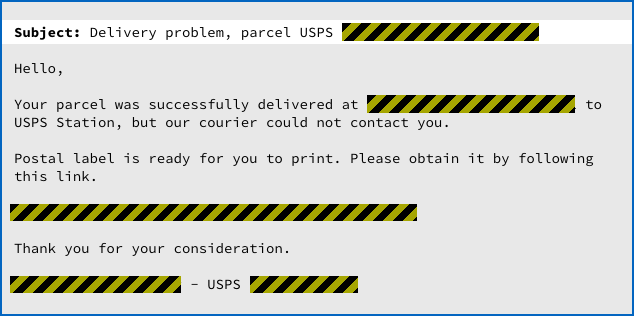
SophosLabs has also seen the Mole ransomware packaged inside a ZIP file, presumably so that the crooks can send out an attachment rather than (or even as well as) a weblink.
Some of us are more inclined to open attachments than to click unsolicited links, perhaps because we’ve ended up in trouble before from a booby-trapped website.
Others of us are diligent about deleting unsolicited attachments but more open to clicking through to websites, perhaps because we regularly exchange links with people we don’t know very well.
Launching the malware
If you click through to the link in the malicious email, you’ll typically be downloading the malware directly, under the guise of installing a special viewer program needed as a plugin for your browser to let you view the document from the courier company.
If you open the malware in its attachment form , you’ll load the ransomware indirectly by launching a script inside the ZIP, again claiming to be a special viewer program.
In the sample we examined, the script file was called Flash-2017.js, as though it were an updated Flash viewer app.
Once you’ve invited the ransomware program into your computer, the trouble starts.
The program files you need to launch Windows, to get online and to send email are left untouched, which is how the crooks make sure you’ll still be able to use your computers to contact them for “help” after the damage is done.
But your data files go from looking something like this…
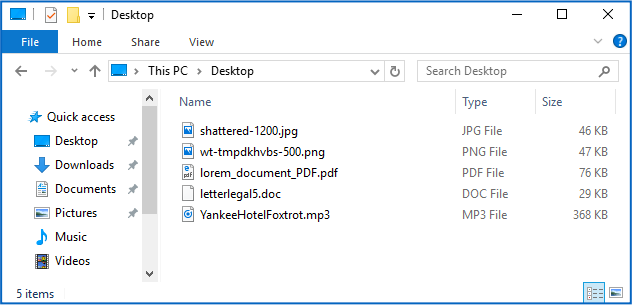
…to this:
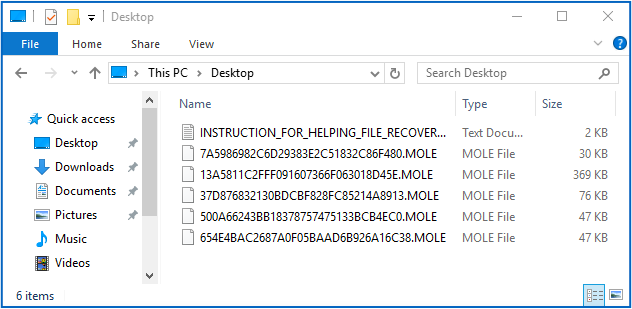
Even your filenames are scrambled, with every extension changed to .MOLE, and the names replaced with random numbers in hexadecimal.
Each file and its original filename ends up encrypted with the RC4 algorithm, using a new, randomly-chosen key every time.
This means that even multiple copies of the same file are scrambled, each copy looks different from all the others, so you can’t even tell that the files used to be the same.
The decryption key for each files is itself encrypted using the RSA public-key algorithm, and then stored along with the encrypted file and filename.
Why use both RC4 and RSA?
The reason for using RSA to encrypt just the decryption key rather than the file is that RSA is a special sort of encryption system that’s too slow to scramble whole files but fast enough for small amounts of data such as cryptographic keys.
But why bother with the extra step of using RSA, given that the file is already encrypted with RC4?
The answer is that RSA is what’s called a public key or asymmetric algorithm.
You need one key (called the public key, which you don’t need to keep secret) to scramble the data, but a completely different key (the private key, kept secret as the name suggests) to unscramble it later.
In other words, the crooks can, and do, ship a copy of their public key buried inside the ransomware program itself; as long as they keep their private key secret, only they can unravel those RC4 decryption keys generated file by file.
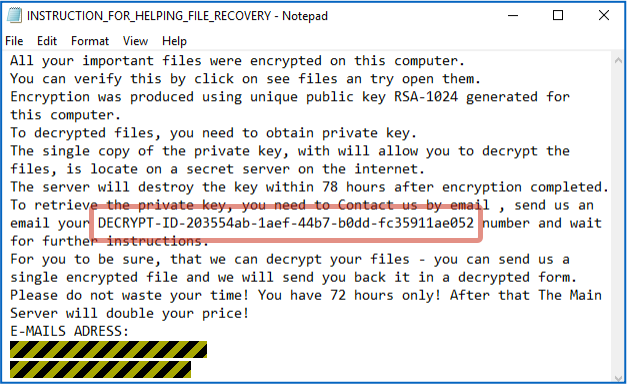
Simply put: the ransomware program can lock your files, but once it’s finished, it can’t unlock them, so you’re stuck with negotiating with the crooks, as explained in a text file that Mole opens automatically on your desktop:
Calling home
Like a lot of ransomware, Mole “calls home” as it runs to a server operated by the crooks, thus letting them know that they’ve clocked up yet another victim.
The network packet is sent out as an innocent-looking POST request via HTTP:
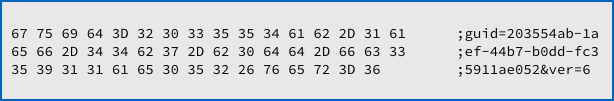
The guid field in the uploaded HTTP data is the same as the DECRYPT-ID in the INSTRUCTIONS file shown above, so that the crooks can tie any later correspondence with you to your call-home packet.
After the ransomware has finished scrambling your files, it calls home again:
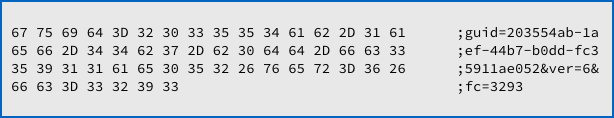
This time, the field labelled fc tells the crooks the file count – how many of your files they were able to scramble.
We assume that they’ll use this as a factor in negotiating the ransom price they want you to pay later on.
What to do?
Try these simple tips:
- When an unsolicited email asks you to open a file or click a link, don’t. (Sometimes, it really is that easy!)
- Be wary of unexpected web plugins. These days, most web pages, including those containing documents, videos and audio, are designed to load and display directly in your browser, specifically to reduce the need for plugins. If in doubt, ask someone you know and trust – never the sender of the unsolicited email!
- Keep a reliable current backup. That way you can recover from lost or scrambled files yourself, with no need to negotiate with crooks.
Remember: the only backup you will ever regret is the one you didn’t make.
Note. Sophos products detect and block this malware as Troj/Ransom-EKZ (the downloaded program) and JS/DwnLdr-SQU (the script part, if used).
LEARN MORE
As always, the best defence against ransomware of any sort is not to get infected in the first place, so we’ve published a guide entitled How to stay protected against ransomware that we think you’ll find useful:

You might also enjoy our Techknow podcast Dealing with Ransomware:
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/qWdG0i7vv7c/









