Unsecured database exposed diabetics’ sensitive data
Diabetes: it’s a killer, both literally and figuratively.
The Type 2 market is predicted to almost double, from $31.2bn in 2015 to $58.7bn by 2025.
It’s great if you’re an investor, horrible if you’re a diabetic struggling to afford pricey drugs, devices and treatments. So it’s understandable why elderly diabetics, eager to sign up for programs that promise discounts on diabetic supplies, would hand over sensitive financial and health information to telemarketers – in other words, to complete strangers.
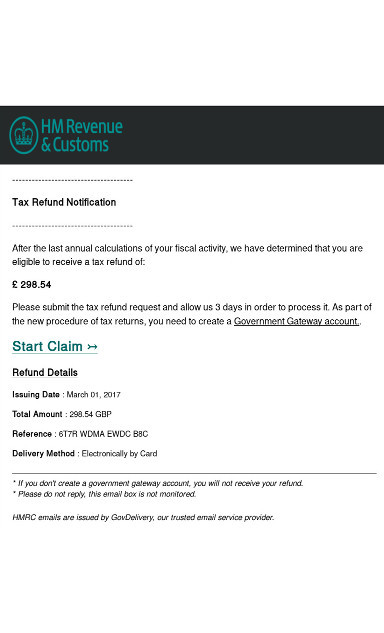
Unfortunately, because of that willingness, 918,000 seniors now have even more to worry about than diabetes. Their records have been discovered, freely available online, left exposed for months by a software developer who’d been working on a project for a telemarketer. He’d uploaded a backup of the telemarketer’s database to the internet and left it wide open.
The database was discovered by a Twitter user named Flash Gordon – @s7nsins – on what turned out to be an Amazon Web Services (AWS) instance at an IP address. Flash Gordon found it by using Shodan, a search engine for connected devices that crawls the internet, connecting to likely services, logging what comes back, and creating a searchable index of the results.
Shodan has powered the discovery of a laundry list of leaky databases. It’s been used to index internet-connected baby monitors, for one. Another target has been improperly configured MongoDB databases, like those at MacKeeper, Sanrio’s Hello Kitty, kid site uKnowKids and Hzone, a dating app for HIV-positive people, among others.
On March 25, Flash Gordon reached out to DataBreaches.net – a data security blog run by a health care professional – about the discovery of the telemarketer database. In turn, DataBreaches.net called on ZDNet’s Zack Whittaker and Troy Hunt, who runs Have I Been Pwned, to help investigate.
What they found: the records weren’t from a health insurer. Nor were they from any other entity covered by the Health Insurance Portability and Accountability Act of 1996 (HIPAA), according to DataBreaches.net’s writeup.
Rather, it was plain that they came from a telemarketer, given that the records contained scripts to follow when calling patients, along with notes about the individuals listed in the database.
They also contained both personal and health information: names, addresses, dates of birth, telephone numbers, email addresses, taxpayer IDs, health insurance carrier, policy numbers, and information about what types of health problems the individuals had in terms of needing diabetic supplies, back braces, or pain gel, according to DataBreaches.net.
Given the timeline, I’m guessing that the screenshot below, posted by Flash Gordon on March 25, shows some of the table rows in question. You’ll notice that the final rows refer to insulin and “AtHomeTesting”: presumably a reference to blood sugar testing.
Ok wow came across something 1.2gb file not sure on total rows yet. But just seeing the table creation fields you know its serious. pic.twitter.com/PUvRU1d664
— Flash Gordon (@s7nsins) March 25, 2017
The records also contained fields populated with sensitive information that would be a goldmine to spearphishers or other scammers: that a given individual was blind, for example, that they’d suffered a stroke, or that they had an aide or a child helping them out… and what those assistants’ names were.
Not everybody listed in the database had handed over their health insurance information. But most did, DataBreaches.net said:
It appeared that although a few people were reluctant or declined to give out their health insurance information, many people seemingly gave out their health insurance information to total strangers for the promise of diabetic supplies at lower prices, pain gels, or even free back braces.
The IP address was owned by a company called MediBoxSolutions.com. That website was owned by a developer named Daynier Brown. According to ZDNet’s Whittaker, Brown had intended the site to eventually provide database solutions for medical providers.
Brown told Whittaker in a phone call last week that he’d gotten a copy of the database when he was working for an outfit called HealthNow (not to be confused with HealthNow New York, Inc., which is an independent licensee of Blue Cross Blue Shield).
HealthNow is owned by Dino Romano, whom Whittaker identified as “a former Unistar executive and securities fraud recidivist“.
HealthNow went belly up in 2015 after failing to file an annual report with Florida authorities. It’s one of many companies that Romano opened and quickly closed, in seemingly disparate fields, including diabetes supplies, education advising, telemarketing, wellness management and more.
Brown told ZDNet that he found the backup drive on a failing hard drive on a development server he owned that was left over from the HealthNow project. He put the data on to his AWS instance, which in turn pointed to his MediboxSolutions.com site.
Brown told Whittaker that MediboxSolutions.com never did provide the database solutions he had intended it to because it was “too much work.”
He gave more details on that:
The data in question was an old system that I developed for healthnow.co in recent years. The files were temporarily placed on the server to get the old crm up and running as the box that I had it sitting on had drive issues and could not run the related platform properly. The system was found to be too unstable and I opted to start a different crm flavor on a MEAN stack. Frankly, I found myself without the time to venture further into it and put the project on hold.
“On hold?” Is that another way to say “stored in an unencrypted format online where anybody playing around with Shodan could have a look at it”?
As of Friday, when ZDNet published its writeup, Brown hadn’t yet told Whittaker why he’d left the database unencrypted … nor why he retained the database after he stopped working for HealthNow three years ago … nor how many distinct IP addresses had improperly accessed the data during the months it was on the AWS instance.
It’s since been deleted.
ZDNet and DataBreaches.net gave a copy of the database to Troy Hunt, over at Have I Been Pwned: a breach notification site that lets you look up your email address or user name to see if you’ve been swept up in a breach.
Hunt determined that the database contained 321,920 unique email addresses. When it comes to reaching out to inform all those involved in the breach, those hundreds of thousands of emails are a start, at least. At any rate, Hunt said that about 80% of the records were already in his database.
If you’re concerned that you might have been affected by the breach, you can look yourself up on Have I Been Pwned.
For future reference, the next time a telemarketer offers you a great deal on diabetes supplies and in return wants to know your doctor’s name, your social security number, personal details about your condition and more, bear in mind that you don’t know whether the caller is legit or a scammer (it’s happened before with diabetes-related fraud). Even if the caller is legit, those details could wind up in replicated databases that appear who knows where, like in this case.
It doesn’t have to be an intentional crime that all your personal and medical information got spilled on the internet. It could just be sheer sloppiness.
To an ID theft or a phisher, it doesn’t matter how or why your details have shown up. All that matters is that they did.
Follow @NakedSecurity
Follow @LisaVaas
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/iyp9ztoWKw8/