Latest numbers indicate Android is now the most targeted mobile device
Thanks to Rowland Yu of SophosLabs for providing the research for this article.
A recent SophosLabs statistical analysis comparing the ratio of malware to potentially unwanted applications (PUA) across Windows, Mac and Android illustrates a trend we’ve been seeing for some time: attackers are rapidly focusing their malware creation and exploit techniques on Android devices.
The analysis also shows the bad guys increasingly using PUAs to slip past security sensors and penetrate Android and Mac devices.
When we pull back the lens on the bigger picture, Windows continues to be the most-targeted of all operating systems, SophosLabs researcher Rowland Yu said. But the growing ferocity against Android is clear.
Follow the money
In an email exchange, Yu reiterated a point we’ve made in the past: the more open the system, the more susceptible it is to malware:
On the other hand, if the system has its own app store such as Mac and Android – or undergoes a system or human review – then malware writers will use PUA instead of malware.
The current thinking in the lab is that malware writers see PUA as a way to more easily bypass security systems and achieve the same end goal they have with other malware – making money.
By the numbers
A look at the raw volume of samples analyzed by SophosLabs in 2016 painted the following picture:
- Of everything targeting Windows, 6% were PUAs while 95% was straight-up malware.
- Of everything targeting Android, 75% is pure malware and 25% were PUAs.
- Of everything targeting Macs, 6% was pure malware and 94% were PUAs.
While malware is designed to do harm, PUAs fall more into the nuisance category: annoying apps that run ads and pop-ups until you finally uninstall them.
Android malware examined
In the SophosLabs 2017 malware forecast released in February, the researchers explored the specific malware designed for Android devices.
SophosLabs analysis systems processed more than 8.5m suspicious Android applications in 2016. More than half of them were either malware or potentially unwanted applications (PUA), including poorly behaved adware.
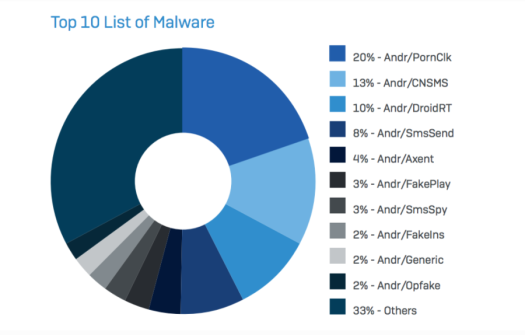
When the lab reviewed the top 10 malware families targeting Android, Andr/PornClk is the biggest, accounting for more than 20% of the cases reviewed in 2016. Andr/CNSMS, an SMS sender with Chinese origins, was the second largest (13% of cases), followed by Andr/ DroidRT, an Android rootkit (10%), and Andr/SmsSend (8%). The top 10 are broken down in this pie chart:
Defensive measures
Though Android security risks remain pervasive, there’s plenty users can do to minimize their exposure, especially when it comes to the apps they choose.
- Stick to Google Play. It isn’t perfect, but Google does put plenty of effort into preventing malware arriving in the first place, or purging it from the Play Store if it shows up. In contrast, many alternative markets are little more than a free-for-all where app creators can upload anything they want, and frequently do.
- Consider using an Android anti-virus. By blocking the install of malicious and unwanted apps, even if they come from Google Play, you can spare yourself lots of trouble.
- Avoid apps with a low reputation. If no one knows anything about a new app yet, don’t install it on a work phone, because your IT department won’t thank you if something goes wrong.
- Patch early, patch often. When buying a new phone model, check the vendor’s attitude to updates and the speed that patches arrive. Why not put “faster, more effective patching” on your list of desirable features, alongside or ahead of hardware advances such as “cooler camera” and “funkier screen”?
If you use a Mac, our recommendations typically include using a real-time anti-virus, even (or perhaps especially) if you have managed unharmed for years without one, and promptly downloading security updates as Apple releases them.
Similar advice applies to malware and PUAs targeting Windows. Apply patches immediately and be careful of attachments and links delivered via Outlook.
Follow @NakedSecurity
Follow @BillBrenner70
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/1qfXlyX9YxM/