Thanks to Graham Chantry and Tad Heppner of SophosLabs for their help with this article.
Many UK residents woke up yesterday to a rude internet shock: a scam email that greeted them with their real name and home address.
Collectively, we’re getting better and better at spotting emails that don’t come from where they say, for example because our real bank doesn’t call us Dear Customer, and because our real mortgage provider knows how to spell its own kompani nayme without making absurd misteaks.
But in this case, the email wasn’t trying to disguise that it came from a ne’er-do-well.
Indeed, the scamminess of the text made the email more worrisome, and thus perhaps paradoxically more likely to squeeze victims into action than a well-written email from an obviously unlikely source.
The text in the emails vary slightly from sample to sample, but examples seen by SophosLabs go something like this:

Or like this:

The salutation uses your first name (given name); the filename is your surname (family name); and the address is your home address, complete with postcode.
You know it’s a scam, not only from the terrible mistakes in spelling and grammar, but also from the fact that no official organisation would dare write what amounts to a veiled threat of this sort.
So it feels wrong and risky to open it to see how much is in there.
On the other hand, there must be some truth in the claims about a data leak, because the crooks know your name and address – and not just vaguely, but precisely, so who knows what else they know about you?
With so many data breaches in the news recently, it’s perfectly reasonably to wonder, “How serious is this?”
So it feels wrong and risky not to open it to see how much is in there.
What happens next?
If you do open the attachment, which is portentously called Yoursurname.dot, Word prompts you for a password, just as the scammers warned you to expect:
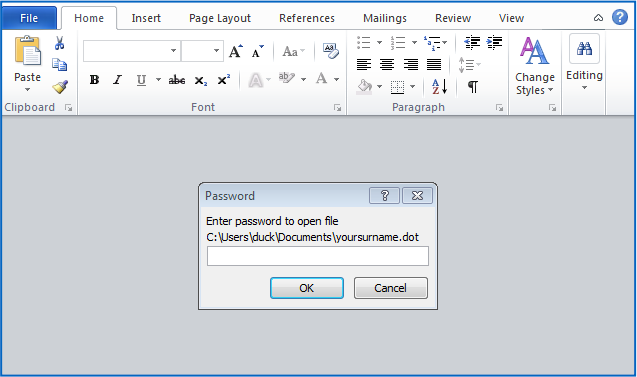
The password is randomly chosen for each recipient, and you really do need to use the one in your own email to open the file:

At this point, the crooks are aiming to persuade you to enable macros in the open document, which means you’ll be running program code stored in the file by the crooks themselves.
This is a feature of Word – you can write extensive and powerful Word extensions as macros, using Microsoft’s Visual Basic for Applications (VBA) programming language – but because macros that arrive from outside can be super-dangerous, they don’t run by default.
To get you to agree to run their malicious macro program, the crooks use what you might call a bait-and-switch trick.
The document presents an official-looking help page that tells you that you need to “Enable editing” to view its content.
Somehow, this sounds less suspicious that enabling macros, as though you’re just agreeing to view what’s inside the document, not trusting it to the point of letting it run untrusted program code inside Word.
If you click on [Enable Content], you’re agreeing to execute a malicious VBA program that tries two different web pages, hosted on hacked web servers, and downloads what looks like a GIF file.
GIF is short for Graphics Interchange Format, an old but still-common type of image file.
In fact, the GIF file has just 10 bytes of valid header data, followed by a 256-byte decryption key, followed by about 0.5MB of binary data scrambled by XORing it with the decryption key repeated over and over. (This is known as a Vigenère cipher, named after a cryptographer from the 1500s who didn’t actually invent it.)

The GIF header makes the file look innocent, even though it won’t display as an image, and the Vigenère scrambling means that the suspicious parts of the file aren’t obvious.
Malware unscrambled
Of course, the scrambling also means that the fake GIF file is harmless on its own, so the malicious macro includes a decryption loop that strips out the executable code, unscrambles it and writes it to %TEMP%, the special folder where Windows saves your temporary files.

The malware ends up with a randomly-chosen numeric name, such as 05643.EXE
When we tested out this attack in SophosLabs, the downloaded malware was Troj/Agent-AURH, a strain of bot or zombie malware that calls home to a so-called command-and-control (CC) network for further instructions.
Our zombified computer didn’t receive any instructions during our test, but it’s important to remember that in attacks of this sort:
- The crooks can vary the downloaded malware as they see fit, changing it according to your timezone, your location, your language settings or simply their own whim.
- The crooks can vary the instructions they send to some or all of the bots in their botnet, typically including updating or changing the bot itself, or downloading additional malware.
Should you be afraid?
It’s understandable to feel a touch of fear when you receive a scam email that knows your name and home address, because of the lurking question, “Why me?”
The good news, if you can call it that, is that through articles and advisories like this one, you’ll soon see that you aren’t alone, and that the crooks are targeting a much wider group than just you.
Sadly, however, it’s likely that the home addresses they’re using were stolen in one or more data breaches, and then sold on in the computer underground for criminal abuse of this sort.
At least in the UK, many companies that collect addresses put them through some kind of standardisation algorithm to produce address data in the format preferred by the Post Office, so it can be hard to figure out the likely source of the breach.
What to do?
- Don’t open unsolicited or unexpected attachments, especially not on the say-so of an unknown sender.
Even if the document claims to be an invoice you don’t owe, or threatens you in some way, don’t let fear or uncertainty get the better of you. After all, if you’re concerned about the trustworthiness of the sender, the worst thing you can do is to take their “advice” about computer security!
- Don’t turn off important security settings such as “macros have been disabled”, especially not on the say-so of an unknown sender.
The crooks have come up with many ways to trick you into clicking [Enable content], usually by making it sound as though it somehow increases security, for example by decrypting or unlocking confidential information. But Microsoft turned Word macros off by default years ago to improve security, so turning macros back on will leave you less secure.
- If you’re unsure what to do, ask someone you actually know and trust, such as a friend or family member.
Never ask the sender of the email for advice. They will simply tell you what they want you to hear, not what you need to know. And if you’re a friend who gets asked for help, try using our short-and-sweet motto, and stick to your guns: “Don’t buy, don’t try, don’t reply.”
- If you think a targeted email of this sort really is a personal attack on you, for example by a stalker, rather than part of a wider cybercrime campaign, and you are genuinely concerned for your safety, contact law enforcement locally.
Be prepared to explain yourself clearly, which typically means keeping suspicious emails and messages.
Have you recently opened an email that you now have reason to distrust, or are you concerned that you may have let malware sneak in by taking risky advice that came from someone you don’t know? If so, you can download our free Sophos Virus Removal Tool to search for malware that may be lurking undetected. You don’t need to uninstall your existing anti-virus first – our Virus Removal Tool is designed to work alongside other security products.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/iDTu97AKSLQ/








