Sean Spicer’s WHOIS data is revealing his personal details
When Sean Spicer became White House press secretary, he acquired a very large bullseye on his back for cybercrooks to take aim at.
Understandably, Spicer’s personal website, SeanSpicer.com, has been made private since he got his new gig. You need to ask for an invitation to get in, according to a message from WordPress.
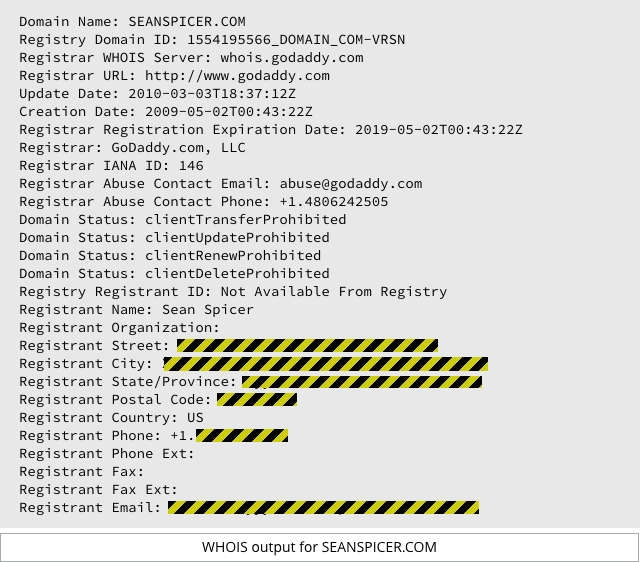
But while you can’t see the content of his website, you can still [2017-02-09T13:12Z] see Spicer’s phone number, email address and home address, through the registration record for his seanspicer.com domain name:
That’s because whoever made Spicer’s site private neglected to make his WHOIS data private as well. All his personal details are out there, like so many pieces of laundry flapping on the public laundry line of the internet.
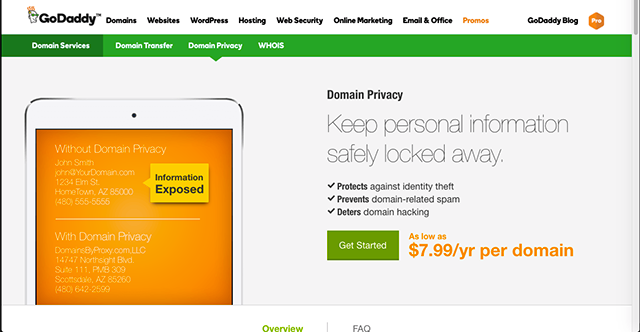
Spicer’s personal site is hosted with GoDaddy. You can keep personal information “safely locked away” when you register your domain with GoDaddy (and other domain hosts, of course), for $7.99 per year.
That helps to protect you against identity theft, GoDaddy assures customers in its advertising, as well as against domain-related spam.
GoDaddy could have chosen to make this ad longer. If you don’t make your domain registration private, and you’re not registering with a business address, you’re leaving your personal information out there for all sorts of creeps to see and abuse. Think SWATters who make crank calls to emergency hotlines with phony bomb threats or bogus reports of shooters at a given address.
In short, you’re leaving yourself open to armed police banging on your front door, guns pointing at you, your family, or any other residents of your home, like has happened to many public or semi-public figures who’ve caught a SWATter’s eye: the gamer who was SWATted while he live-streamed on Twitch.TV, for example, or the well-known security journalist Brian Krebs, or GamerGate critic Grace Lynn.
Another GamerGate target was Brianna Wu, who was driven from her home after someone posted her address online and threatened to rape, kill and mutilate her.
As those cases show, there can be extreme repercussions from leaving your personal details available online.
As an individual gains in celebrity, be it through gaming, journalism or conducting prickly press conferences as the White House’s chief media liaison, locking down privacy becomes ever more crucial.
That doesn’t make it any less important for us non-celebs, of course.
Is your domain private? If not, why not? If you want to stop reading this and go make it private right this very minute, have no fear: we’ll wait for you to get back and tell us your thoughts about it in the comments section below.
Follow @NakedSecurity
Follow @LisaVaas
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/ESCtdocYxwo/