Outsider Attacks Give Nightmares To CIOs, CEOs, CISOs
 What’s This?
What’s This?
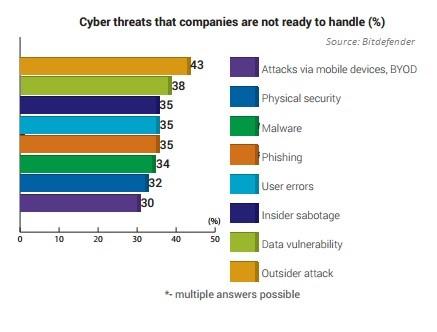
Outsider attacks, data vulnerability and insider sabotage are the main threats companies aren’t ready to handle, according to a Bitdefender survey of 250 IT decision makers at US companies with more than 1,000 PCs.
CIOs know that cybercriminals can spend large amounts of time inside organizations without being detected; Advanced Persistent Threats (APTs) are often defined as threats designed to evade detection.
Accessing any type of data, whether stored in the private or public cloud, needs to be done via multiple authentication mechanisms, Bitdefender’s security specialists recommend. This should involve more than just usernames and passwords. For access to critical data, two-factor or biometric data offers additional control and authorization of qualified and accepted personnel. This is especially significant in organizations where access to critical and sensitive data is restricted, and only then under strict security protocols and advanced authentication mechanisms.
Insider sabotage is the third threat IT decision makers can’t yet handle
“To limit the risks of insider sabotage and user errors, companies must establish strong policies and protocols, and restrict the ways employees use equipment and infrastructure or privileges inside the company network,” recommends Bogdan Botezatu, Bitdefender’s senior e-threat specialist. “The IT department must create policies for proper usage of the equipment, and ensure they are implemented.”
In the past two years, companies witnessed a rise in security incidents and breaches, with a significant increase in documented APT type of attacks targeting top corporations or government entities (such as APT-28). This type of attack intends to exfiltrate sensitive data over a long period, or silently cripple industrial processes. In this context, concerns for security are rising to the top, with decisions taken at board level in most companies.
IT decision makers, CISOs and CEOs are all concerned about security, not only because of the cost of a breach (unavailable resources and/or money lost), but also because their company’s reputation is at risk when customer data is lost or exposed to criminals. The more media coverage a security breach receives, the greater the complexity of the malware causing it. On top of this, migrating corporate information from traditional data centers to a cloud infrastructure has significantly increased companies’ attackable surface, bringing new threats and more worries regarding the safety of the data.
The demand for hybrid cloud, a mix of public cloud services and privately owned data centers, is estimated to be growing at a compound rate of 27% a year, outpacing overall IT market growth, according to researcher Markets and Markets. The company said it expects the hybrid cloud market to reach $85 billion in 2019, up from $25 billion in 2014. (Read the full white paper here.)
This survey was conducted in October 2016 by iSense Solutions for Bitdefender on 250 IT security purchase professionals (CIOs/CEOs/ CISOs – 26 percent, IT managers/directors – 56 percent, IT system administrators – 10 percent, IT support specialists – 5 percent, and others), from enterprises with 1,000+ PCs based in the United States of America.
Razvan, a security specialist at Bitdefender, is passionate about supporting SMEs in building communities and exchanging knowledge on entrepreneurship. A former business journalist, he enjoys taking innovative approaches to hot topics and believes that the massive amount of … View Full Bio
Article source: http://www.darkreading.com/partner-perspectives/outsider-attacks-give-nightmares-to-cios-ceos-cisos/a/d-id/1328019?_mc=RSS_DR_EDT