Google sent ~40K warnings to targets of state-backed attackers in 2019
In 2019, Google sent nearly 40,000 warnings to accounts that were targeted by state-sponsored phishing or malware attacks, it reported on Thursday.
That’s a nearly 25% drop from 2018: an improvement for which it claims at least some credit. Toni Gidwani, Google’s Threat Analysis Group (TAG) security engineering manager, said:
One reason for this decline is that our new protections are working – attackers’ efforts have been slowed down and they’re more deliberate in their attempts, meaning attempts are happening less frequently as attackers adapt.
Threat actors pretend to be journalists, news outlets
TAG has seen a rising number of attackers impersonating news outlets and journalists, including those from Iran and North Korea. For example, they’ll impersonate a journalist to spread fake news among other reporters.
Google’s also seen cases wherein attackers first try to chummy up with targets by sending several benign emails to build rapport. Then, they’ll send a malicious attachment in a follow-up email. Google says that government-backed attackers “regularly target foreign policy experts for their research, access to the organizations they work with, and connection to fellow researchers or policymakers for subsequent attacks.”
This has been going on for a while. We saw an example in 2017, when a fake hot babe with a patently fake LinkedIn profile (a 28-year-old MIT grad with 10 years of experience? Oh, puh-leez!) managed to dupe IT guys at a US government agency that specializes in offensive cybersecurity.
The (mostly) not surprising, heavily targeted sectors
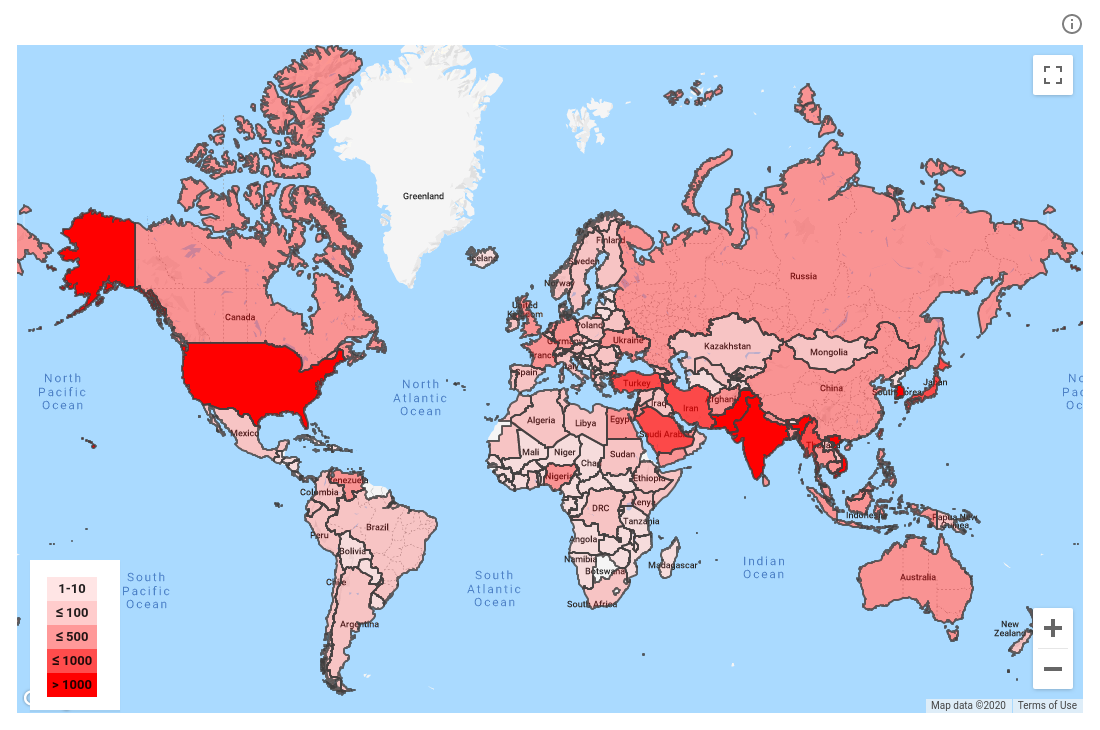
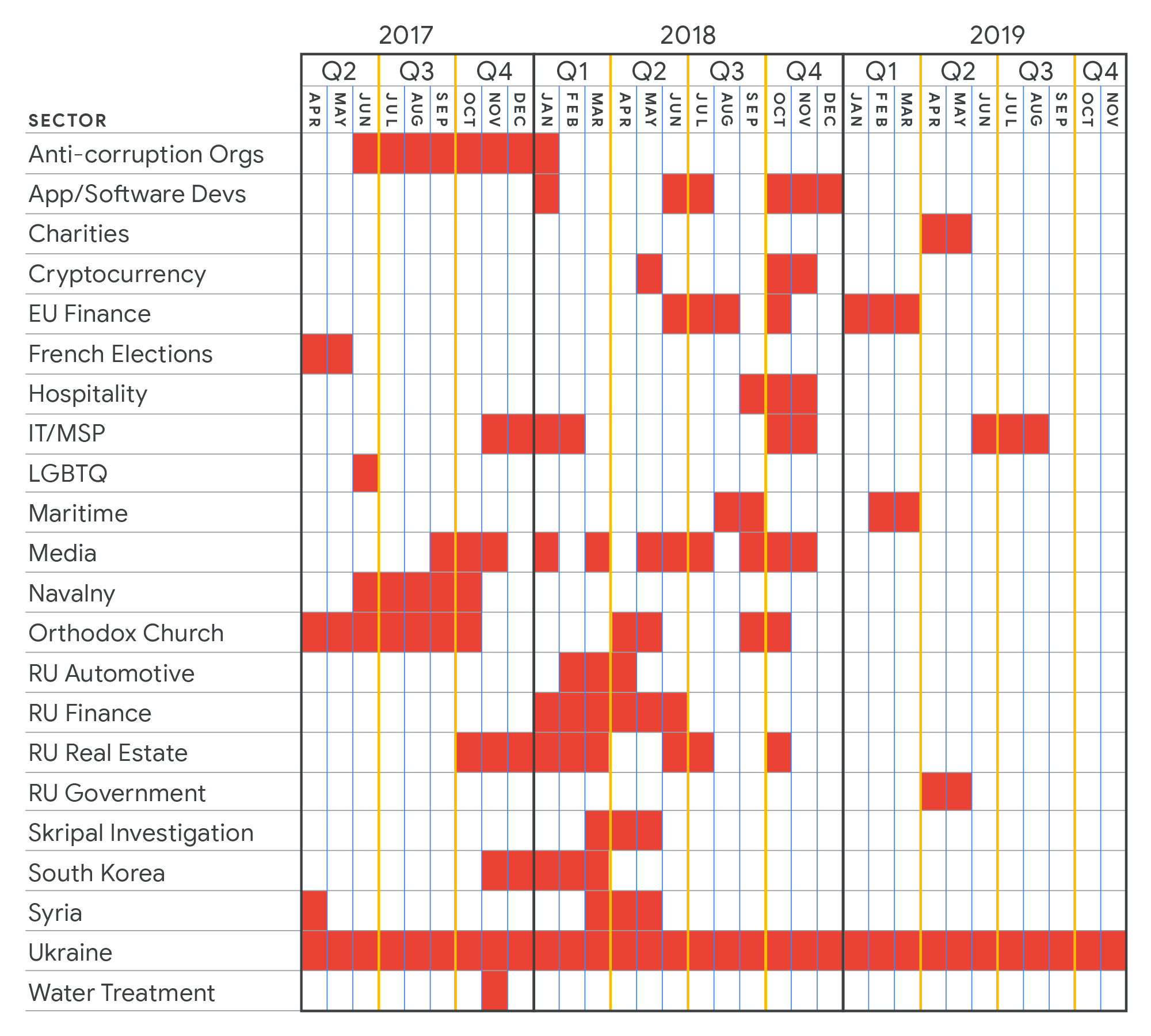
Google published this chart showing where one state-backed threat actor – the Russian group Sandworm – has focused its hacking over the past three years. Like other government-backed attackers, they’ve heavily targeted geopolitical rivals, government officials, journalists, dissidents and activists:
If at first they don’t succeed, they’ll try, try again
These adversaries are nothing if not persistent. Google says that last year, one in five accounts that it warned about phishing or malware attacks was targeted multiple times. No luck penetrating your defenses? That’s OK, they’ll go after somebody you know, Gidwani says, or try to tempt you some other way:
If at first the attacker does not succeed, they’ll try again using a different lure, different account, or trying to compromise an associate of their target.
It’s not hard to find examples: for one, we saw a WhatsApp zero-day that allowed hackers to silently install government spyware onto victims’ phones and was exploited in the wild.
That zero-day was used to target Amnesty International. Subsequently, in May 2019, the human rights group sued the makers of Pegasus, alleging that its spyware was used to surveil Amnesty staff and other human rights defenders, thereby putting human rights at risk.
Google claims that its Advanced Protection Program (APP) — a free service for Google accounts that’s currently on limited release — safeguards personal Google Accounts from targeted attacks, going beyond two-factor authentication (2FA) by adding another security step. You will need…
- An Android 7.0+ device, which has a built-in security key;
- An iPhone with the free Google Smart Lock app (which you can get here); or
- Two security keys in order to enroll, the cost of which varies by model. Here’s Google’s guide to picking and purchasing a security key that will work with your device. Any key that supports the FIDO open standard will work.
As of Friday, there was a waiting list to join the service. In the meantime, Google suggests turning on 2FA and running its security checkup.
We say hear, hear! to the 2FA advice.
Learn more about 2FA
LISTEN NOW
Click-and-drag on the soundwaves below to skip to any point in the podcast. You can also listen directly on Soundcloud.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/rcIjuHYrwHM/
 Check out
Check out