CryptoLocker urgent alert
 We’ve seen a resurgence in interest in the CryptoLocker ransomware, not least because the UK’s National Cybercrime Unit (NCU) put out a warning about it yesterday.
We’ve seen a resurgence in interest in the CryptoLocker ransomware, not least because the UK’s National Cybercrime Unit (NCU) put out a warning about it yesterday.
The NCU burst onto the cybercrime fighting scene as part of the UK’s newly formed National Crime Agency (NCA), which became operational just a month ago, on 07 October 2013.
The NCA is part of the UK’s effort to tackle organised crime, including crimes launched by electronic means.
And CryptoLocker has been a strange baptism of fire for the agency dubbed by some “the British FBI.”
What CryptoLocker does
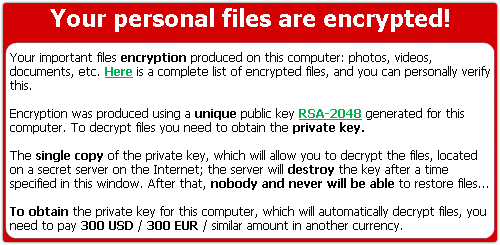
If you’ve been following the story, you’ll know that CryptoLocker is malware that deliberately scrambles your precious data files, such as documents and spreadsheets, and offers to sell you a decryption key to get them back.
The price the crooks are charging is currently hundreds of pounds.
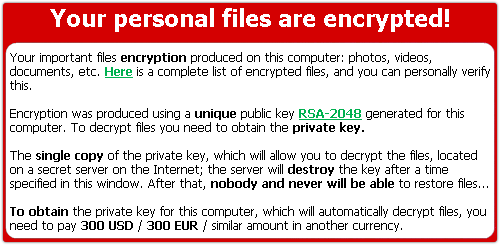
Of course, if you have a decent anti-virus, you’re unlikely to get infected in the first place, and if you have a decent backup you should be able to recover your data even if the worst happens.
But if you don’t, then you’re stuck.
As far as we can tell so far, the crooks who are operating the CryptoLocker crimeware haven’t left any holes or backdoors by which you can recover your data without paying up:
- The decryption key is different for each victim, so you can’t share your key with the next guy.
- The encryption used is strong enough that it can be considered impossible to crack.
- The crooks don’t let your key out of their sight until payment is received.
- No-one, to the best of our knowledge, has been able to get into the crooks’ own network to recover the keys.
Why the risk is high
Even though CryptoLocker is already well known, having made headlines for several weeks, and and tips on how to avoid it have been widely publicised, things may yet get worse.
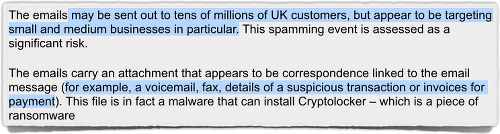
The NCA’s recent alert warns that emails containing infectious attachments “may be sent out to tens of millions of UK customers, but appear to be targeting small and medium businesses in particular.”
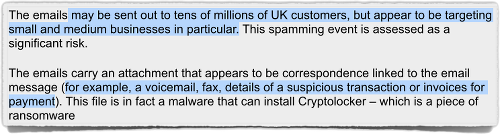
The attachments are often disguised, warns the NCA, as files that sound important enough to open, but not of a sort usually associated with viruses and malware, “for example, a voicemail, fax, details of a suspicious transaction or invoices for payment.”
Of course, crooks have known for years that attachments can be made to look like images, or audio files, or documents, by giving them names like VOICEMAIL.MP3.EXE or INVOICE_SCAN.JPG.EXE.
You see VOICEMAIL.MP3, which seems innocent enough, but Windows sees VOICEMAIL.MP3.EXE – in other words, an executable file, better known as a program.
So instead of firing up your media player, opening the attachment runs the malware.
How you can help
Even if we can’t find the crooks to stop the ransom process and get back all the keys created so far, we don’t have to be victims.
If you are the go-to IT expert for your friends and family, you can help:
- Warn your friends about the dangers of unsolicited email attachments.
- Check that they have a proper anti-virus and are keeping it up-to-date.
- Show them how to make backup copies of their precious files and to store the backups safely.
- Make sure they keep up-to-date with patches for their operating system and software.
- Get them to read up about CryptoLocker so they are in no doubt about the risk.
- Use CryptoLocker as evidence why prevention is better than cure.
GET INFORMATION AND ADVICE
If you are looking for useful material to use in advising your friends and family, Naked Security has the following excellent resources at hand:
• CryptoLocker prevention, cleanup and recovery.
• A video showing CryptoLocker in action.
• Five tips for protecting against ransomware
Remember: an ounce of prevention is worth a pound – in this case, hundreds of pounds – of cure.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/en5PUU5irUo/
 We’ve seen a resurgence in interest in the
We’ve seen a resurgence in interest in the