OS X Mavericks
 Apple’s OS X 10.9, better known as Mavericks, is officially out.
Apple’s OS X 10.9, better known as Mavericks, is officially out.
The burning question for OS X fans everywhere, of course, is, “Should I or shouldn’t I?”
The positive spin is that the $29 fee Apple has charged for previous OS X “dot releases” has vanished.
Just like the uplift from Windows 8 to Windows 8.1, shifting from Mountain Lion (OS X 10.8) to Mavericks is free.
The negative spin is that since this is a dot release, there might just be more to go wrong than in a point release – just like happened in the uplift from Windows 8 RT to Windows 8.1 RT, which caused trouble for some early adopters.
→ In my vocabulary, a major release would be OS X to OS XI, a dot release something like 10.8.5 to 10.9, and a point release 10.8.4 to 10.8.5.
Will Mavericks go wrong if you install it right away?
Industry veteran and former Naked Security colleague Graham Cluley, for example, is dead keen on staying away – so much so that he’s even retweeted himself (I didn’t know you were allowed to do that) to tell us so.
Graham still seems to think it needs beta testing.
Digital lifestyle site Lifehacker also warns you to stay clear, saying without giving data that Mavericks “suffers from a speed decrease” (you or I would probably just have written that it was slower), and calling it “imperfect.”
Mind you, the site also says, with doubly ironic orotundity, that “you should have no trouble work under the new OS without trouble.”
I’d love to tell you that Graham is just being a scaredy-cat and Lifehacker merely stirring, but I can’t – and not for want of trying.
It’s just that at 5.29GB, over a mobile network, I’m still waiting for the Mavericks installer to download itself.
There is one thing that neither Graham nor Lifehacker took into account, however, and that’s the fact that Mavericks (the first OS X release not named after a type of cat) is a security upgrade, too.
OS X 10.9 as a security update
In fact, the list of security fixes is, to me, the most interesting part of 10.9.
If you’re looking for Remote Code Execution vulnerabilities, or RCEs, you won’t be disappointed – you’ll find several.
There’s a fix for dealing with “a format string vulnerability [that] existed in Screen Sharing Server’s handling of the VNC username.” (CVE-2013-5188.)
There’s a patch for curl, the web download utility, apparently sorting out multiple vulnerabilities including some that could lead to RCE. (CVE-2013-0249 and CVE-2013-1944.)
And there’s even a fix for an RCE hole in the kernel itself, caused by incorrect bounds checking, which implies that there was an exploitable buffer overflow. (CVE-2013-3954.)
But there are other important operational fixes, notably for security features that gave a false sense of security, because even when turned on, they didn’t always work.
Here are some examples:
- The OS X application firewall had a bug so that applications to which you thought you’d blocked network traffic might nevertheless receive it.
- Apple’s application sandbox could be bypassed by software that it was supposed to have locked down.
- Safari’s Reset function didn’t always clear your session cookies, which could leave you logged in to sites you wouldn’t expect.
- The display’s lock screen didn’t always stop window contents from appearing on top of it.
- The lock screen sometimes didn’t activate after the interval you had chosen.
- You could sometimes return from hibernation mode without needing a password.
- Random numbers weren’t always random. (Or, to quote Apple’s own delightful oxymoron, “under unusual circumstances, some random numbers may be predictable.”)
- The Mail app would sometimes detect that secure password exchange was possible when configuring a connection, but then fail to use it.
- The “Require an administrator password to access system preferences with lock icons” setting wasn’t always honoured.
Mavericks also includes a brand new release of Safari, version 7, that includes a raft of security fixes published to pre-Mavericks users as Safari 6.1.
In short, it sounds to me as though Mavericks is probably an update you do want to get, though I can’t put my hand on my heart yet and say, “She’ll be right.”
I’m still waiting for that 5.29GB to turn up.
While that’s happening, I’m sorting out my backups – always a good idea anyway – and installing the 50MB Safari 6.1 update on my Mountain Lion system.
And, I hasten to add, I’m getting ready to make a copy of the Install OS X Mavericks.app package out of the /Applications folder as soon as the download finishes, so I never need to download it again
If you’re an Apple fan, where do you sit on Mavericks?
Keen on new features, and willing to wait for 10.9.1?
Or keen on security and ready to update right away?
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/cuz_XleY5MM/

 Information security has become such a booming business that it seems there is a conference somewhere in the world every single week.
Information security has become such a booming business that it seems there is a conference somewhere in the world every single week.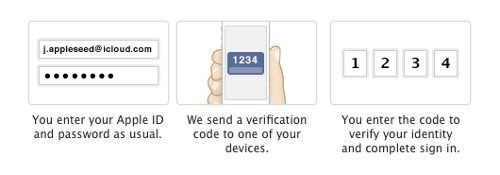
 Katalov demonstrated that by simply acquiring the Apple ID and password of another user, whether they have enabled two-factor authentication or not, he can download their iPhone/iPad/iPod backups and documents from iCloud and see their pictures, music, emails, contacts, documents, presentations, spreadsheets or anything else without the victim being alerted.
Katalov demonstrated that by simply acquiring the Apple ID and password of another user, whether they have enabled two-factor authentication or not, he can download their iPhone/iPad/iPod backups and documents from iCloud and see their pictures, music, emails, contacts, documents, presentations, spreadsheets or anything else without the victim being alerted. Unlike other similar systems of the past, this one didn’t depend on bulky laptops or large antennae, says the speaker, Daniel Cuthbert, COO of SensePost.
Unlike other similar systems of the past, this one didn’t depend on bulky laptops or large antennae, says the speaker, Daniel Cuthbert, COO of SensePost.
 Soon after iOS 7 came out, a
Soon after iOS 7 came out, a  My last post about
My last post about  With all the software installed, it was time to think about
With all the software installed, it was time to think about  Since we’re talking networks, I should mention that our home wireless network is also set up with security in mind.
Since we’re talking networks, I should mention that our home wireless network is also set up with security in mind.  Ever since I first passed my driving test I realised how expensive motoring could be. Just buying a car and filling the tank with petrol took my entire childhood savings. Thankfully the yearly road tax and insurance costs weren’t too high.
Ever since I first passed my driving test I realised how expensive motoring could be. Just buying a car and filling the tank with petrol took my entire childhood savings. Thankfully the yearly road tax and insurance costs weren’t too high. Apple’s OS X 10.9, better known as Mavericks, is officially out.
Apple’s OS X 10.9, better known as Mavericks, is officially out.