Rejiggering IT Security Budgets For Better Perimeter and Systems Control
As is the case in any other business, IT security leaders must contend with finite resources and as a result they must depend on smart decisions about where to target their budget to ensure they leave as few gaps as possible. The only problem, one which security folk have dealt with for years, is that they tend to be seduced by the latest innovation over the fundamental management tools necessary to implement enough control over network and system infrastructure to properly manage their risks.
“When it comes to security budget, security organizations are very much like my children: they want to buy whatever they’ve seen last and is shiny and new and promises unbelievable results,” says Alan Shimel, managing partner of The CISO Group. “A serious dose of pragmatism and maybe just a little maturity would go a long way.”
Shimel says he’s written about it and stomped his feet until blue in the face, mostly to no avail. It’s a trend that Eric Cowperthwaite, former CISO of Providence Health and Services and now vice president of advanced security and strategy for CORE Security, has seen unfold time and again.
[Your organization’s been breached. Now what? See Establishing The New Normal After A Breach.]
“All too often the spending is on things that will provide for compliance with laws and regulations or that are glitzy and sexy and in the trade news a lot,” he says, explaining that an organization may make big investments in next generation firewalls or a huge single sign on system while failing to attend to simple tasks like patch management or configuration management on their systems. “We see organizations being exploited by social engineering and the compromise of systems that were not patched, even though the vulnerability was known for weeks, even months.”
On the network side, network change management and firewall rules management falls squarely within this “blue-collar, meat-and-potatoes” kind of security management market, Shimel says, “it’s just not as sexy to the guy who is looking for the security flux capacitor.”
These kind of management tools that offer more network controls and enable policy orchestration are foundational, but may be a budgetary afterthought. And the more they’re back-burnered, potentially the harder it will be politically to add them in after the fact. As Shimel explains, if an organization spends several million over the course of two to three years to pick up next generation firewalls and update traditional firewalls, coming in after that is over and asking for another half a million dollars for firewall management to keep the rules properly configured on those systems may anger the CFO or CIO.
But as IT organizations look into more iterative devops processes that require changing the network more frequently than ever and as they start to dive into projects such as software-defined networking to increase the dynamic nature of the network, they may well be forced to bake in security and change management into the budget cycle much earlier in the process, says Jody Brazil, president and CTO of firewall management firm FireMon.
“All of these great things get spun up at the click of a button within minutes of saying go and then either the access doesn’t exist, the access control systems aren’t in place,” says Brazil, “or the reverse–access is automatically allowed but now you don’t have scanning set up to run against this new system or the IPS isn’t configured in tune for the fact this is a new application,”
Brazil believes that as organizations are dragged into this more “operational world” of networking, security management is getting thrust front and center. He believes there could be a tide shifting, as he’s seen clients begin to worry more about those security management needs first before sparing change for those shiny new toys. For example, he mentions a customer in the federal space that is engaging his company before putting in a new slate of network security tools and next generation firewalls, so the agency can lay the groundwork for day-to-day controls first.
“Security management is becoming part of that budget conversation,” he says. “Whereas we often used to get brought in after the fact, they’re starting with management and saying ‘Let’s get this figured out first, then well worry about expanding the rest of the infrastructure.'”
Have a comment on this story? Please click “Add Your Comment” below. If you’d like to contact Dark Reading’s editors directly, send us a message.
Article source: http://www.darkreading.com/perimeter/rejiggering-it-security-budgets-for-bett/240162636
 We get an awful lot of spam in our spamtraps.
We get an awful lot of spam in our spamtraps.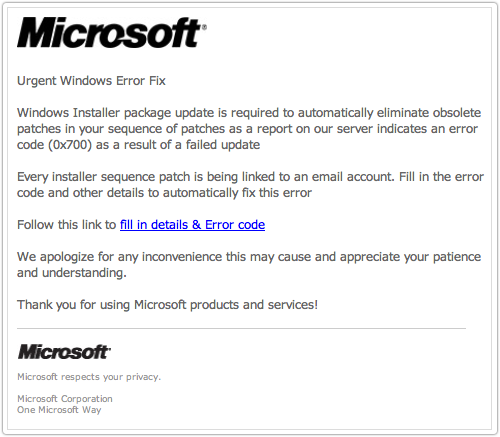
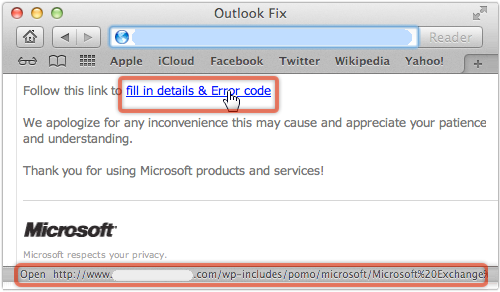
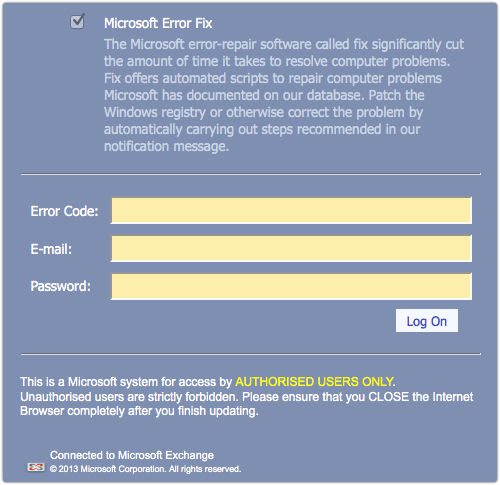
 In December 2012, Facebook announced a slew of privacy changes, one of which –
In December 2012, Facebook announced a slew of privacy changes, one of which – 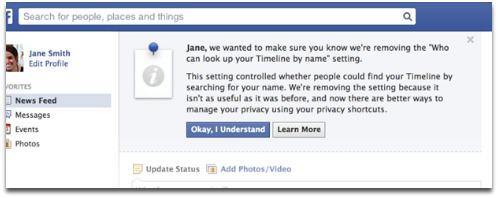

 In the course of one afternoon at last week’s Virus Bulletin conference in Berlin, two major cross-industry
In the course of one afternoon at last week’s Virus Bulletin conference in Berlin, two major cross-industry