Happy 10th b-day, Patch Tuesday: TWO critical IE 0-day bugs, did you say?
Email delivery: 4 steps to get more email to the inbox
Microsoft delivered no fewer than eight bulletins to mark the tenth anniversary of Patch Tuesday, including a fix covering two zero-day vulnerabilities in Internet Explorer.
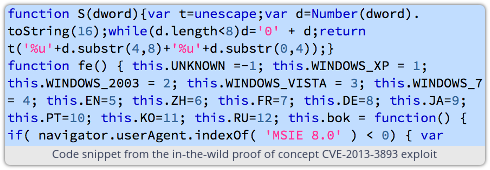
A critical patch for all supported versions of IE covers a well-anticipated fix for the CVE-2013-3893 vulnerability, which has been associated with cyber espionage-style attacks against targets in Japan, Taiwan and elsewhere in Asia since late August.
Microsoft also released a bonus extra fix for another in-the-wild browser bug. The same MS13-080 bulletin also covers the CVE-2013-3897 vulnerability that has become the target of attacks over the last two weeks or so. FireEye was the first to discover a malware campaign (dubbed Operation DeputyDog) linked to the CVE-2013-3893 security bug, while Trustwave SpiderLabs is claiming the credit for fingering the CVE-2013-3897 flaw.
“MS13-080 also addresses CVE-2013-3897 in an interesting case that illustrates the concurrent discoveries of vulnerabilities,” explains Wolfgang Kandek, CTO of cloud security firm Qualys, in a blog post.
“The vulnerability underlying CVE-2013-3897 was found internally at Microsoft and would have been fixed in MS13-080 as part of the normal security engineering and hardening that the product undergoes constantly. However, in the last two weeks, attacks against the same vulnerability became public – again, limited and targeted in scope – but since the fix was in the code already, it enabled Microsoft to address the vulnerability, CVE ID CVE-2013-3897, in record time.”
Microsoft explains that the MS13-080 bulletin “fixes multiple security issues, including two critical vulnerabilities that haven’t been actively exploited in limited targeted attacks.”
All versions of IE, from 6 to 11, need patching with updates that tackle 10 vulnerabilities in total.
The MS13-080 bulletin is by far the most important of the October batch but Redmond is also releasing three other critical fixes and four “important” security bulletins. The batch, which marks the tenth anniversary of Patch Tuesday, collectively grapples with 26 vulnerabilities.
The critical MS13-081 update addresses seven vulnerabilities in the Windows kernel, including problems in font handling, and can be triggered remotely through malicious web pages and maliciously formatted Office documents. Bugs in Microsoft’s .NET Framework and finally a vulnerability in Windows Common Control Library (64 bit only) occupy the remaining two berths on the critical list.
The upshot is that everything from Windows XP up to and including Windows 8 and Windows RT will need patching to defend against security bugs that are more problematic for desktop systems.
Noteworthy “important” vulnerabilities MS13-085 and MS13-086, both cover remote code execution-type vulnerabilities in Microsoft Excel and Microsoft Word, respectively. Security watchers are more worried about the potential for mischief from these bugs than Microsoft itself.
The two other “important” updates cover lesser security bugs in Microsoft Silverlight 5 and Redmond’s Sharepoint portal server software.
Microsoft’s advisory and an easier to understand graphical overview from the SANS Institute’s Internet Storm Centre provide more information.
Adobe – fresh from warning about a compromise on its website that might have exposed the IDs, password hashes, and encrypted credit card information of nearly three million customers – separately delivered a patch for its Acrobat and Reader software. Adobe also patched its RoboHelp software. ®
Email delivery: Hate phishing emails? You’ll love DMARC
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2013/10/09/patch_tuesday_double_ie_trouble/

 All communications coming from visitors and athletes at the 2014 Winter Olympics in Russia will be monitored by newly strengthened telephone and internet spying technologies.
All communications coming from visitors and athletes at the 2014 Winter Olympics in Russia will be monitored by newly strengthened telephone and internet spying technologies. The work has included laws that require all telephone and ISP providers to install SORM boxes in their technology.
The work has included laws that require all telephone and ISP providers to install SORM boxes in their technology.  The US National Security Agency (NSA) really, really hates
The US National Security Agency (NSA) really, really hates  Microsoft’s Tenth Anniversary Patch Tuesday
Microsoft’s Tenth Anniversary Patch Tuesday