Snowden outs NSA’s “Follow The Money” international banking spies
 According to a new report, referencing leaks from Edward Snowden, the National Security Agency (NSA) has been widely monitoring international banking and credit card transactions. The agency allegedly targeted customers of Visa Inc. as well as the Society for Worldwide Interbank Financial Telecommunication (SWIFT).
According to a new report, referencing leaks from Edward Snowden, the National Security Agency (NSA) has been widely monitoring international banking and credit card transactions. The agency allegedly targeted customers of Visa Inc. as well as the Society for Worldwide Interbank Financial Telecommunication (SWIFT).
According to Germany’s Der Spiegel newspaper, information leaked by former NSA contractor Snowden shows that surveillance of financial transactions was carried out by a branch of the security agency known as “Follow The Money” (FTM).
The details of all the monitored transactions were then transferred to an NSA database called “Tracfin.” Snowden claims that in 2011 that database held 180 million records of which 84% were related to credit card transactions.
Der Spiegel alleges that the NSA targeted transactions in Europe, the Middle East and Africa to:
collect, parse and ingest transactional data for priority credit card associations, focusing on priority geographic regions.
In response to that allegation the newspaper quotes a Visa spokesperson who, “ruled out the possibility that data could be taken from company-run networks,” whilst Mashable has a quote from Visa security and privacy representative Rosetta Jones:
With respect to the claims in the Der Spiegel article, we are not aware of any unauthorized access into our network. Visa takes data security seriously and, in response to any attempted intrusion, we would pursue all available remedies to the fullest extent of the law. Further, it’s Visa’s policy to only provide transaction information in response to a subpoena or other valid legal process.
The NSA also spied on SWIFT, a network used by more than 10,000 banking institutions in over 200 countries. The system, used by the banks for sending transaction data in a secure manner, was spied upon on many levels according to the Der Spiegel report. One such way in which the NSA was accessing the information was described as reading “SWIFT printer traffic from numerous banks.”
“A deep invasion of privacy”
According to the documents there seemed to be at least some concern over the collection of such financial data.
The UK’s intelligence agency, GCHQ, queried the legal issues surrounding “financial data” and its own involvement in the program saying that, “The collection, storage and sharing of politically sensitive data is a deep invasion of privacy”, and involved “bulk data” full of “rich personal information,” much of which “is not about our targets.”
 Whilst this news may be further confirmation that the NSA is involved in widespread spying, it is probably not a huge revelation to many.
Whilst this news may be further confirmation that the NSA is involved in widespread spying, it is probably not a huge revelation to many.
In fact the real surprise may be that the Tracfin database ‘only’ stored 180 million records, considering that SWIFT itself processes over 15 million transactions every day.
The whole point of having an intelligence agency is to monitor the actions of potential enemies and the money trail is often a very good starting point for any investigation. It appears that this financial monitoring was almost exclusively targeting non-US citizens anyway so few, if any, domestic laws would have been broken.
Furthermore, the US Treasury already has an agreement with SWIFT which affords it consensual access to international transaction records, as confirmed by former Homeland Security chief Juan Zarate and SWIFT’s own CEO Leornard Schrank just a couple of months ago. This agreement is further backed up by a European treaty which came into effect on August 1, 2010.
Follow @Security_FAQs
Follow @NakedSecurity
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/iwBmcnnlN6o/
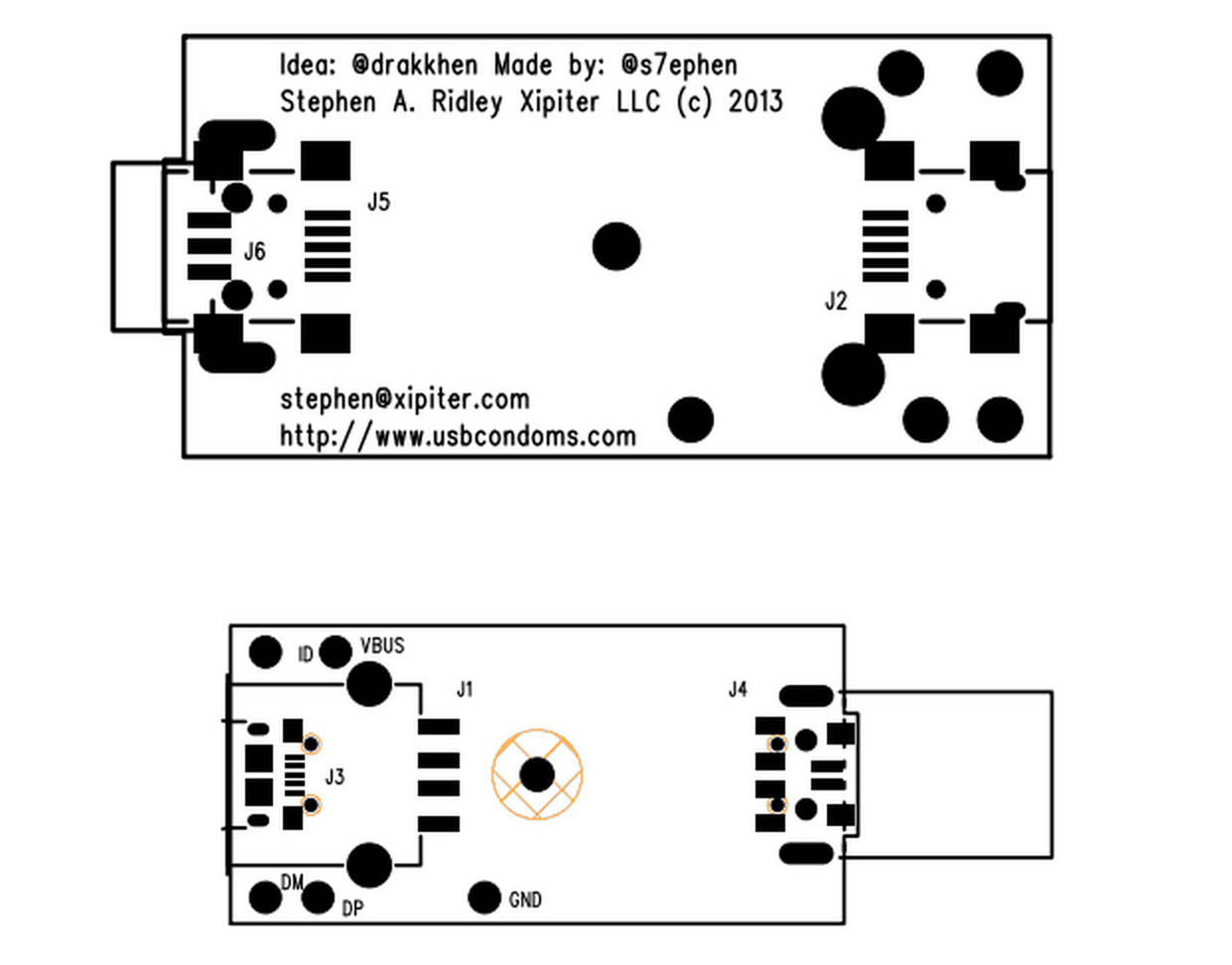
 You’ll soon be enjoying the adulation of the whole jailbreaking scene, a writeup on Naked Security, and the prospect of a job/lawsuit (or both!) with/against Apple.
You’ll soon be enjoying the adulation of the whole jailbreaking scene, a writeup on Naked Security, and the prospect of a job/lawsuit (or both!) with/against Apple.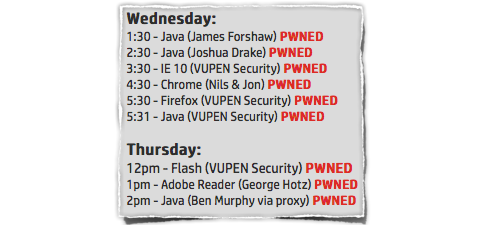
 For the first time in a little over four months, Microsoft published an emergency advisory and Fix it for users of its Internet Explorer web browser.
For the first time in a little over four months, Microsoft published an emergency advisory and Fix it for users of its Internet Explorer web browser. For more advanced users and corporate IT managers you can use Microsoft EMET to mitigate exploitation of this flaw as recommended in
For more advanced users and corporate IT managers you can use Microsoft EMET to mitigate exploitation of this flaw as recommended in  <!– >> headline
<!– >> headline