WannaCry: could something similar happen to Android?
In the week since WannaCry hijacked hundreds of thousands of computers in 150 countries, we’ve been asked if Android devices are vulnerable. The answer is no, for a simple reason: WannaCry targets Windows.
But don’t be lulled into comfort by that. SophosLabs researcher Rowland Yu said Android is a huge ransomware target. WannaCry’s payload was merely one stripe of countless ransomware varieties. Yu explained:
A big difference between Windows and Android is that the foundation of Android is Linux kernel. Moreover, Android has removed unnecessary and potentially insecure parts of the kernel.
WannaCry exploited a Windows vulnerability Microsoft had released a patch for in March. That flaw was in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. The SMB function isn’t built into Android.
Furthermore, he said, WannaCry uses an NSA EternalBlue exploit and DoublePulsar backdoor to silently install and execute the payload. But installing apps in Android generally depends on users to install them or click on them. This also reduces the speed and chance of massive infection in wild.
SophosLabs has determined that WannaCry probably didn’t start the way a typical ransomware attack does – as a phishing email carrying a malicious attachment or link that the user is tricked into opening. It also appears the first infections were in south-east Asia. (Sophos CTO Joe Levy gave a webinar outlining the technical details of the attack, which you can access on the Sophos webinar page.)
Researchers assumed early on that the outbreak began with an email link or attachment, but SophosLabs VP Simon Reed identified it as a worm from start to finish.
In other words, this outbreak was a throwback to the early 2000s. Only this time, instead of mere noise and network downtime, a much more damaging payload of ransomware ground many organizations to a halt.
Android has its own problems
Though Android escaped this outbreak, Yu warned against complacency:
This week, Google announced the Android operating system has more than 2bn monthly active devices. Also, the growing adoption of Android has been found in the enterprise environment, in which Android devices are allowed for increased access to corporate information. Without a doubt, Android has become one of the main targets for criminal hackers. This is why SophosLabs has discovered the significant increase of Android ransomware in the last 12 months.
The SophosLabs 2017 malware forecast goes into detail about the ransomware threats against Android. SophosLabs analysis systems processed more than 8.5m suspicious Android applications in 2016. More than half of them were either malware or potentially unwanted applications (PUA), including poorly behaved adware.
And, in recent weeks, SophosLabs has uncovered a variety of questionable apps in Google Play.
A big question for Android users is if Android devices could suffer a WannaCry-sized attack. Before we answer the question, SophosLabs offers this statistic of Android ransomware during the last couple of years:
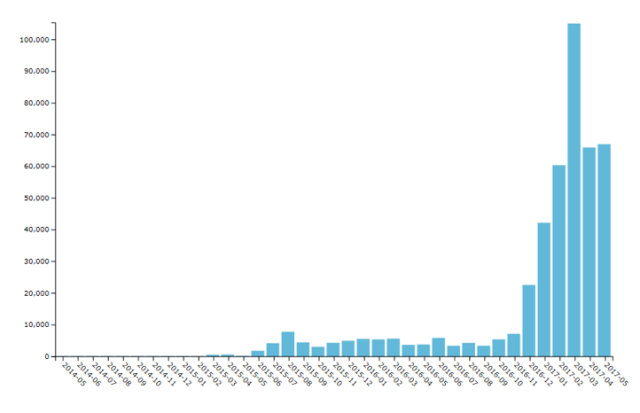
The trend of Android ransomware
Since the first Android ransomware was discovered in the middle of 2014, SophosLab has recorded the significant increase in the last three years. Just in the last 12 months, its research shows a spike of between 700% and 1,000% in Android ransomware.
In general, there are two types:
- Lock Screen ransomware
- Crypto ransomware
The former can lock the victims’ screen but not encrypt files. It might also change the lockscreen PIN to stop accessing devices. Moreover, some ransomware contains extra malicious behaviors apart from the locking screen, such as:
- Command and control
- Send SMS
- Steal sensitive information
- Disable anti-virus software
- Install or uninstall apps
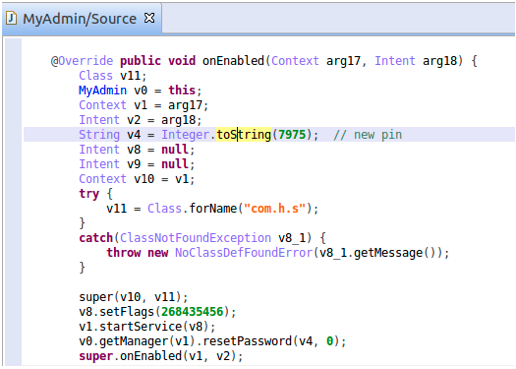
Here is a simple example of lock screen ransomware:
The locked screen above shows users can contact the attacker via WeChat or QQ in order to unlock the screen. Luckily, this ransomware only uses a hard-coded PIN, which can be found in the source code below:
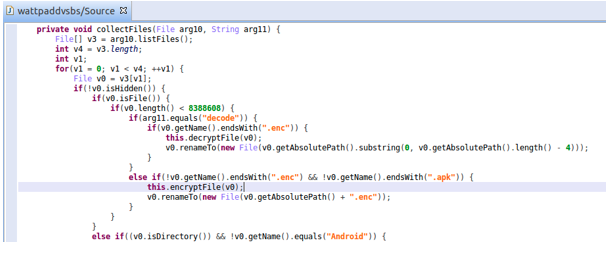
The second type of ransomware can encrypt users’ data while locking devices. Here we show an example:
This is the encryption code in the crypto ransomware:
It all needs to be taken seriously, Yu said. But in the big picture, these examples don’t have the ingredients that made WannaCry such a monster.
Defensive measures
As we’ve mentioned before, our advice to non-Sophos customers is not to download apps from Google Play without doing your homework on where they come from first.
The continued onslaught of malicious Android apps demonstrates the need to use an Android anti-virus such as our free Sophos Mobile Security for Android.
By blocking the install of malicious and unwanted apps, even if they come from Google Play, you can spare yourself lots of trouble.
LEARN MORE
As always, the best defence against ransomware of any sort is not to get infected in the first place, so we’ve published a guide entitled How to stay protected against ransomware that we think you’ll find useful:
You might also enjoy our Techknow podcast Dealing with Ransomware:
Follow @NakedSecurity
Follow @BillBrenner70
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/3_Lny6A8E38/