Why you should be cautious of emails from friends or colleagues
You’ve probably been warned about the risks of trusting emails from people you don’t know, and if you haven’t then our advice is to think twice before booking your dream holiday from an email claiming that you have won the lottery when you didn’t even buy a ticket!
But what about emails from your friends, colleagues, long-standing doctor or smart-suited solicitor?
When we receive a message from a familiar email account, then how many of us are likely to click on links or open attachments without paying as close attention as we would for an email from an unknown account?
As a NakedSecurity reader you are probably already aware of these risks. But what about your friend, your mother, your next door neighbour or someone you do business with?
Last week my solicitor had his email account hacked. Here’s what happened next.
The First Attack
For me it started with an email from my solicitor:
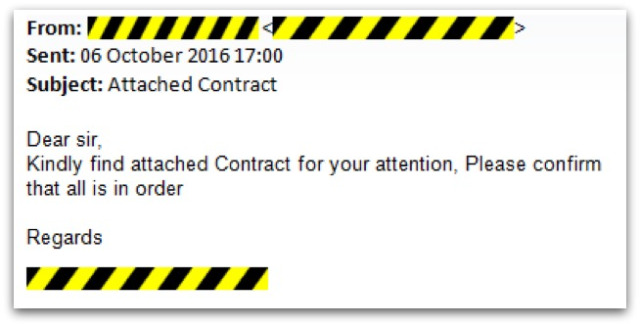
This came from his real (not spoofed) email address and included his normal email signature, with phone and address details. As I am in the middle of moving house and expecting paperwork from him, this email and attachment appeared completely normal at first.
As I moved my cursor to open the attachment I noticed a problem. The attachment was called Drafted Contract003.pdf.htm – a cunning use of the double extension .pdf.htm which was an attempt to trick me into thinking that this was a PDF document instead of the HTM (web page) file that it actually was.
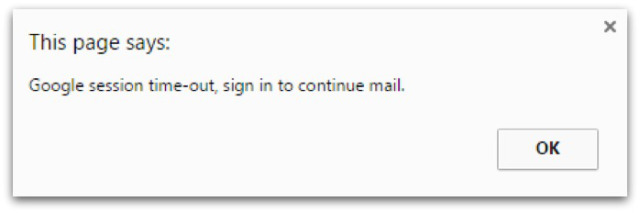
On opening the file, instead of a PDF viewer launching, my browser opened with a popup alert:
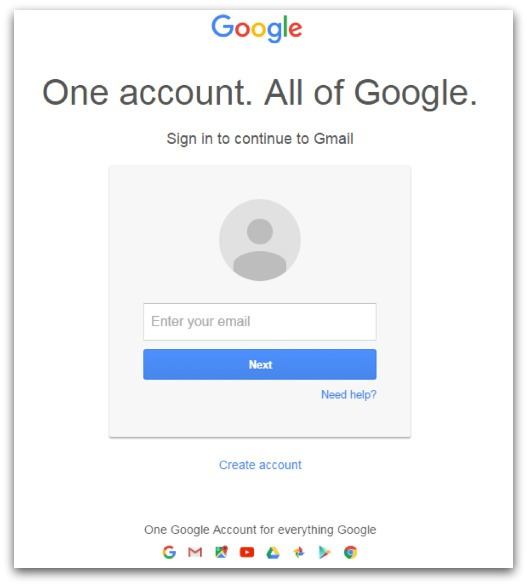
After closing this alert I was taken to a very realistic looking Google login page:
The next clue that this wasn’t real can be seen in the address bar:
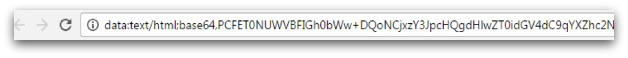
This address clearly isn’t Google, it isn’t even a website URL, but instead it is the code included in the HTM file. This code can be seen if you open the HTM in a text editor:
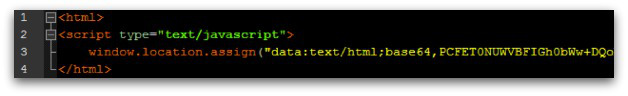
If you look at the source code of this page in a browser you can see that any user who enters their username and password will have those details submitted to the hacker and not Google.

At this point I contacted my solicitor and alerted him to the fact that his email account had been compromised and it was sending phishing emails. He thanked me and took my advice in changing his password and contacting his customers to advise them to be on the lookout for suspicious emails.
But that wasn’t the end of it – the next day I received another email.
The Second Attack
The new email had the same signature and appeared to come from my solicitor; however, this one actually came from a random Gmail address:
This time it had a real PDF file attached called Financial Statements001.pdf. On opening this file, a blurry picture appeared with a link at the top.

I haven’t altered this picture. It was blurred out by the crook so that most of the text is unreadable, leaving only the Barclays bank logo and an ‘Approved’ stamp legible. The idea is to trick you into thinking you have been approved for some kind of contract or loan and that if you click the link at the top you will be able to view the details.
In reality, clicking the link takes you to a web page hosted on the same domain as the previous phishing email, which again requires you to ‘log in’ on a fake Google page.
Looking at the whois ownership information for that domain, I saw that it had been registered one week earlier using presumably fake or stolen personal details of a woman called Fiona in Lagos, Nigeria.
At this point it was clear that the hacker had not only got into my solicitor’s email account but also stolen all the contact details in his address book. This allowed the attacker to continue targeting me and other customers using the same details but from different email addresses.
What happened?
I contacted my solicitor again to try and understand if he knew how his account had been hacked and what else had happened. It came as no surprise that he had recently received a similar email that had tricked him into entering Google login credentials. So he was phished, which led to the account compromise.
Now I wanted to understand the purpose behind the actions of the crook: was he just after usernames and passwords to sell on the Dark Web?
The answer became clear when I looked at the filters on his email account.
He had twenty new email filters named A, B, C… all the way through to T. Most of these had a similar theme: any email containing a keyword in the subject or message, such as Bank, Statement, or Sort Code would be moved into a Recently Deleted folder.
For hackers working against the clock, aware that the victim could change their password at any moment, this would make it very quick for them to get hold of the most valuable emails and save them for further investigation later.
The last few filters targeted emails that contained references to Contract003.pdf.htm. These would be automatically dumped into the Spam folder.
In other words, emails from me – and anyone else who tried to warn the solicitor that he had been hacked – would most likely have vanished into his Spam folder and never been seen, giving the hacker more time to keep the scam going.
It would be easy to say at this point that the moral of this story is, “Don’t trust anybody”, but I don’t want to be that dramatic.
Because it’s Cybersecurity Awareness Month, I’m going to leave you with more usable advice: STOP. THINK. CONNECT.
Even a couple of seconds of thought before opening attachments or clicking on links can save you from all sorts of unwanted attention from cybercriminals.
What to do?
To protect yourself from emails sent under false pretences by crooks:
- Look out for emails that come from different addresses to what you’d expect.
- Be careful of documents that ask you to enable macros or editing before you can see the contents.
- Tell Windows Explorer to show file extensions to protect you against misleading filenames.
- Watch out for double file extensions (e.g.
.pdf.htm) or extensions you aren’t familiar with (e.g..js,.wsf,.lnk). - Hover your mouse cursor over links to see if they go where they say they are going.
- If in doubt, call or speak in person to your friend or colleague and ask them if they sent the email. (Don’t use the number in the email you’re concerned about – look the number up in a different way!)
To protect yourself from having your email taken over by crooks to attack your friends and customers:
- Pick proper passwords. Even though strong passwords don’t help if you are phished (the crooks get the strong password anyway), they make it much harder for crooks to guess their way in.
- Use two-factor authentication whenever you can. That way, even if the crooks phish your password once, they can’t keep logging back into your email account.
- Consider using Sophos Home. Our free security software for Mac and Windows blocks malware and keeps you away from risky web links and phising sites.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/IVzSoIw8JvM/