Research While messaging apps, social media, fake websites and phone calls can all be used to carry out phishing attacks, in the business world, fake emails are the most common and dangerous method.
The wave of mass-mailing phishing attempts appears to be subsiding but that doesn’t mean business and IT managers can allow themselves to be lulled into a sense of security. Attackers are focusing their efforts on well-focused “spear-phishing” campaigns using cleverly crafted messages that bypass traditional email security measures. It is estimated that perpetrators have so far tricked unsuspecting businesses out of $5bn.
This Temperature Check of 330 IT professionals reveals that attackers are regularly impersonating senior managers and targeting specific business departments. So, what’s to be done?
Let’s start by sizing up the problem and looking at how organisations are responding to this threat.
Impersonators, imposters, and thieves sneak past email security checkpoints
Love it or loathe it, there’s no escaping email. Your organisation may be using enterprise social networks and chat-based platforms to reduce the volume of emails, and some companies are even starting to shift their customer communications to apps and chatbots, but none of these has the same reach and range as email. If you have customers, partners, investors or suppliers, you still need to use it.
Email protocols, standards and architectures have evolved over the decades to address privacy and security issues. An ecosystem of ancillary products and services has also grown up to address specific problems and business requirements.
If you work in IT and run email servers on-premises you’ll be aware of the many products and services that wrap around the corporate email system to provide in-bound and out-bound hygiene and security. And if you’ve outsourced your corporate email, as many organisations have, then your service provider is likely to use an even bigger mix of products and technologies to protect your inbox.
We will provide an insight into how widely these technologies are used a little later in this Inside Track, but first we need to assess the threat that phishing poses to your business.
The survey data (Figure 1) indicates the scale of the phishing problem, with about 40 per cent of respondents reporting an incidence of at least daily phishing attacks. Although larger companies are more at risk firms of all sizes can be targeted, and there’s only slight variation across industries. The survey results also show that well-protected and well-prepared organisations receive phishing reports from end users, so every business and institution is a potential target.
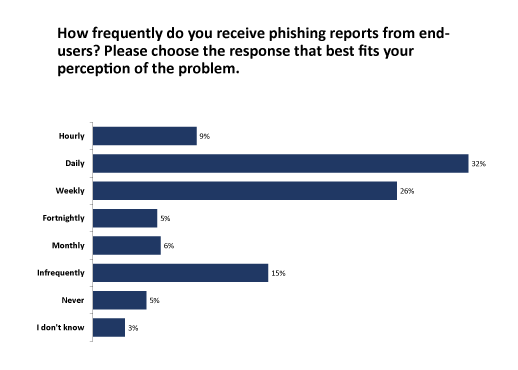
Figure 1 – Click to enlarge
Every phishing attack reported by an end user is evidence of at least two things. First, it proves that a well-crafted phishing attack can sneak past almost any security checkpoint or email filter. Secondly, it shows that some users are savvy enough to spot an attack and know how and where to report it.
What this chart doesn’t show us, however, is the number of phishing emails that go unnoticed or unread, or hit their target. While scattergun attacks are declining according to security industry reports, spear-phishing targeting specific businesses and individuals is on the increase. So, who is being targeted?
Follow the money
The FBI started tracking business email compromise (BEC) attacks in 2013. Is 2016 Internet Crime Report (published June 2017 (PDF)) stated that organised crime groups had targeted large and small companies and organisations in every US state and more than 100 countries around the world, with losses now in the billions of dollars. In the UK, the 2016 Cyber Security Breaches Survey found that 32 per cent of breaches or attacks involved impersonation of someone in the organisation.
BEC can take a variety of forms, with fraudsters most commonly tricking employees who have access to company finances into making fund transfers to bank accounts controlled by the criminals. But spear-phishing attacks also target those who manage business processes and IT (Figure 2). This opens organisations up to a range of vulnerabilities, including ransomware attacks and good old-fashioned extortion.
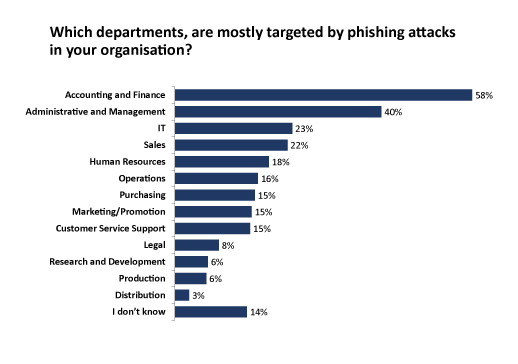
Figure 2 – Click to enlarge
BEC perpetrators are not amateur mischief makers but sophisticated groups with access to significant resources. The FBI reports that lawyers, linguists, hackers, and social engineers are often used to craft a spear-phishing attack, so it’s not surprising that companies can easily be fooled.
How do the fraudsters do it exactly, and what can your organisation do to guard itself against an attack?
Masters of disguise
The fraudsters know there are plenty of “phish” in the sea and scam emails impersonating a senior manager or executive can help them land the big one. In a “whaling attack”, perpetrators are willing to go to considerable lengths to study an organisation’s processes and systems, collect email samples, and even monitor company events in search of an upcoming business trip that might present them with an opportunity.
A typical spear-phishing attack plays out like this: when the time is right a maliciously crafted email is sent to the victim. The fraudsters spoof a familiar trustworthy account, belonging for example to an executive, senior manager or supplier, and instruct the recipient, such as a finance officer or accounts clerk, to carry out some routine financial transaction.
More than half of the respondents in our survey confirm that senior managers in their organisations have been impersonated in spear-phishing attacks (Figure 3). Targeted employees usually believe they are sending money, or commercially sensitive information, to a familiar account, but the details are used to deposit the funds in the scammer’s account.
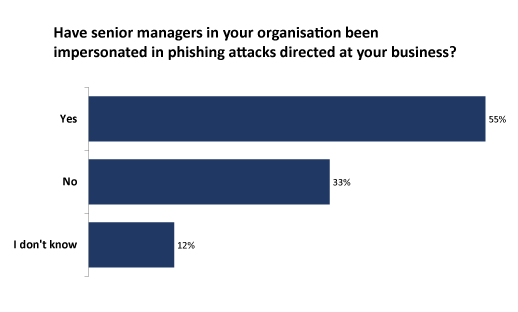
Figure 3 – Click to enlarge
Professional fraudsters know what they’re doing and use money laundering techniques to cover their tracks. It is usually too late to recover the money if the transaction goes through. If it’s commercially sensitive information that has been sent, the perpetrator might use it for immediate commercial gain or to trick another individual in the organisation or supply chain.
This all might sound like a plot line for a glamorous heist movie, but it’s fast becoming a very common and run-of-the-mill business story.
As phishers and whalers become more adept, what can your organisation do to protect itself?
Forewarned is forearmed
As with all things IT, technology on its own is not enough. Policies and processes are just as important, with regular testing and refinement to ensure a good business fit.
Even the most diligent of employees is fallible so you need to implement anti-phishing solutions alongside security products to protect your corporate email systems. End-point solutions add a layer of protection at the email client on desktop and laptop PCs.
More than 60 per cent of the respondents to our survey said they had already implemented anti-phishing protections or are “well advanced” when it comes to dealing with email-based phishing attacks, but this still leaves a sizeable proportion exposed (Figure 4).
And given the survey audience has an interest in security and data protection topics, these figures are likely to be somewhat optimistic for organisations in general.
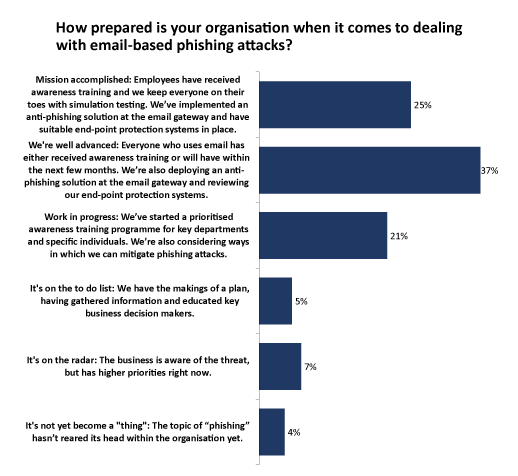
Figure 4 – Click to enlarge
Having IT security products and policies in place is only part of the solution. There’s no escaping the fact that humans are the weakest link when it comes to security, so is is crucial to consider staff training, especially for employees working in accounting and finance departments, as well as in administration, management and of course IT (remember what we saw in Figure 2).
A one-off training course can be little more than a box-ticking exercise, so consider how employees will be kept on their toes, with simulation testing being one obvious option.
If you’ve attended to all the above, well done, but it doesn’t end there. We’ve already agreed that since humans are fallible no security system can ever be perfect, so what happens when things do go wrong?
The cybersecurity playbook
There are hundreds of thousands of cyber-attacks on businesses like yours every day, attempting to steal your company’s information and its money or to disrupt operations. You might be well prepared but even the best defended company can never be totally safe.
So what happens if a spear-phishing or whaling attack hits its mark? Do you have a response plan?
Less than a quarter of those we surveyed said they had a specific playbook for dealing with sophisticated targeted email threats and exploits (see Figure 5). And while 38 per cent said they are “getting there”, the remainder have only a very general approach at best for dealing with this kind of incident.
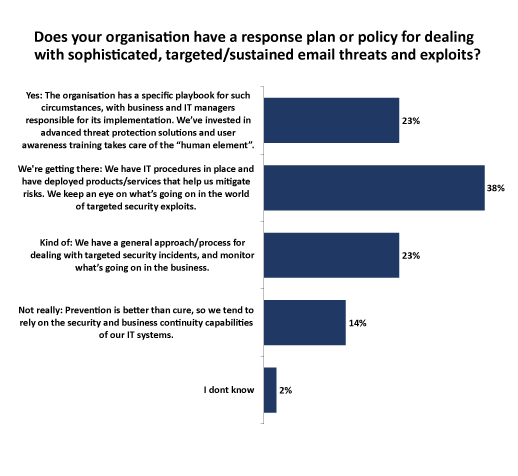
Figure 5 – Click to enlarge
If you don’t yet have a response plan, it might be a good idea to get executives to back the design, development and testing of one as part of their fiduciary responsibility. There are plenty of sources of good practice, as well as specialist consultants who can advise if your budgets can be made to stretch.
Think too about who you to turn to for support if your organisation falls victim to a financial phishing attack. Your audit firm or banking provider might be able to help here. If you suffer an IT service attack or disruption, think about what your recovery procedures will be and how you could keep your core business operations running.
Let’s now look at what organisations can do to mitigate the risks of phishing attacks.
Stay clear of the risks
The adoption rate of anti-virus and anti-spam solutions is nearly 100 per cent, but much smaller numbers say they have anti-phishing measures, spoofing detection, URL protection and data loss prevention in place (Figure 6).

Figure 6 – Click to enlarge
We can assume that our survey group of IT professionals has good insight into security and risk mitigation measures, so it’s somewhat disconcerting that anti-phishing, URL protection and spoofing protection are not more widely used. Some organisations may think they’re better protected than they are (especially in the SMB space, where email is generally outsourced), but budgets – or lack thereof – are also likely to be an issue.
Popular cloud-based communication and collaboration platforms, such as Microsoft Office 365 and Google’s G Suite, can help organisations shoulder the burden of corporate email, but both have been the focus of targeted phishing scams.
Third-party anti-phishing solutions are available from vendors, but this still leaves the most vulnerable element – the end-users – left to their own devices (quite literally in many cases). If you were to receive an out-of-hours email on your device from your boss marked “URGENT”, albeit to your personal email account, would you open it?
All-round protection
Training staff to spot phishing attacks, and testing them periodically, is likely to have a positive effect but it will never make for a totally safe working environment. Likewise, it’s impossible to mitigate every risk using technology, no matter how much money and expertise is thrown at it. A combined approach is required: one that is layered, multifaceted and adaptive.
We’re starting to see machine learning and artificial intelligence being employed to counter phishing attacks but it will take a while for these technologies to enter the mainstream. In the meantime, organisations can reduce risk security by following best practice.
- Commit to educating, training and testing employees. Good security habits take time to establish, so simulation and periodic testing should be part of your regime. IT security firms, industry bodies and government agencies can offer tips and best practice advice.
- Advise employees to be wary of emails appearing to originate from C-suite executives. If the message requests an immediate payment or funds transfer, or the sending of commercially sensitive information, make sure payment policies and procedures are followed.
- Consider the use of digital signatures for executives using email, and the use of two-factor authentication procedures such as a phone call or text message when immediacy is required. Staff need to know that if something smells a bit “phishy” they should pick up the phone and speak directly to the person requesting the transaction or information.
- Evaluate modern email protection services, such as anti-phishing, URL protection/detonation, spoofing protection and user activity profiles for unusual or out-of-policy activities.
- Produce a playbook that details what to do when a spear-phishing attack penetrates your organisation, and if you suspect that you’ve been targeted by a phishing email, report the incident immediately to the relevant authorities.
Sponsored:
The Joy and Pain of Buying IT – Have Your Say
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2017/10/26/phishing_temperature_check/






