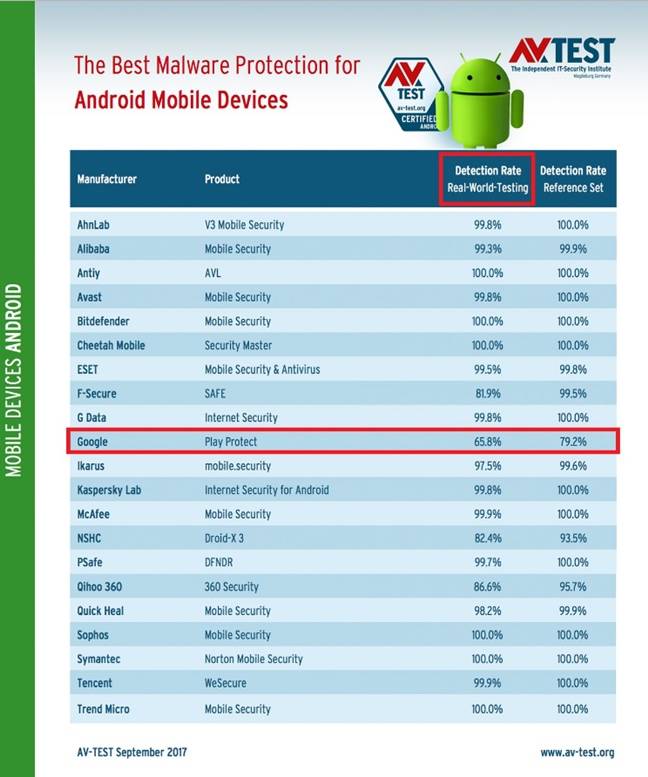
The origins of the rapid-fire ransomware attack campaign affecting mainly Russian targets remain a bit of a mystery.
The Bad Rabbit ransomware attack first spotted on Tuesday that spread in a matter of hours and hit machines mostly in Russia now appears to be over.
But as investigators dig deeper into the code and the anatomy of the attacks, they still aren’t sure just how malware-laden watering-hole attacks spreading the ransomware were set up, nor whether the subsequent worm-spreading infections were more about making money or mayhem.
Several research teams have concluded that Bad Rabbit shares some common code with previous ransomware variants Petya and NotPetya, but they can’t be sure it’s the same group or groups behind the attacks.
“A lot of clues point it [in] the direction of the gang behind NotPetya, but further investigation is required to assess,” says Marc-Ettiene Leveille, a malware researcher with ESET.
But Russian security firm Group IB said in a blog post that the code overlap “suggest a link between Bad Rabbit and Black Energy campaigns.” Black Energy is the Trojan used by the Russian nation-state Sandworm attack group thought to be behind the cyberattacks on Ukraine’s electrical utility, which is also believed to have waged NotPetya.
New research from RiskIQ appears to support a link to the nation-state attackers based on its tracking of the injection servers and dozens more infected websites.
They spotted four injection servers, one dating back to September of 2016, operating on the infected websites. “The operators of this campaign have been able to use this position to target unique visitors based on IP space they associate with their targets. The thing we do not understand at this point is why they decided to burn this information position to mass distribute the BadRabbit ransomware rather than save it for another type of malware,” they wrote. “The goal of the attack using ExPetya back in June was simple: cause as much disruption in the Ukraine and those associated with Ukraine as possible which also seems the case in the BadRabbit attack.”
Meanwhile, what sets Bad Rabbit apart from the Petya and NotPetya ransomware attacks, however, is that it took a different path in its campaign, and didn’t multiply in the same manner. “It wasn’t a wiper and it’s not designed to be purely destructive,” says Nick Biasini, a threat researcher with Cisco’s Talos team, which has studied the attacks.
While the previous two ransomware campaigns relied more on exploits and supply-chain attacks to distribute their malware surreptitiously, Bad Rabbit employed old-school password-stealing and didn’t exploit any vulnerabilities on victim machines.

“What makes this particular strain unique is the inclusion of a hardcoded credentials list, which the malware uses to spread through [SMB local] network shares,” in addition to its use of the open-source Mimikatz tool to extract passwords, Leveille says.
The ransomware attack demanded a ransom of .05 Bitcoin, or $285 and infected victims either by a watering hole attack or phishing emails rigged with malicious attachments. Most security vendor research teams initially concurred the infections came via a handful of compromised websites, including news sites and a Bulgarian travel site and a Turkish cinema site, that unknowingly served up malicious and phony Adobe Flash installers. But late today, the plot thickened as the Security Service of Ukraine said in a post on its website that the infections came via phishing emails posing as Microsoft technical support.
Bad Rabbit spread quickly and for a short period of time in an apparent attempt to do the most damage. “It was designed to move around locally. It’s more about getting the most [possible] systems infected for monetary gain or otherwise,” Biasini says.
The ransomware campaign hit hundreds of government, media, transportation, and other targets in 15 nations, including Russia’s Interfax Agency and Fontanka, and Ukraine’s Kiev Metro, its Odessa International Airport, and various ministries of infrastructure and finance.
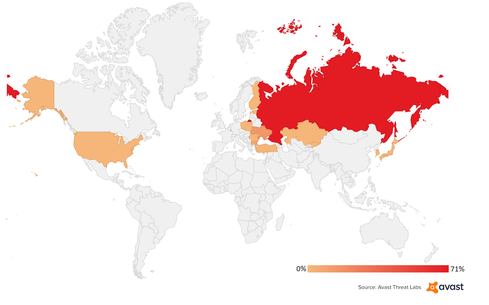
According to data from security firm Avast, Russia was most affected, representing 71% of detections by the AV firm, followed by Ukraine, 14%, and Bulgaria, 8%.
Although the US-CERT yesterday said it had received “multiple reports” of Bad Rabbit infections from “many countries,” ESET’s Leveille says his firm has not spotted any detections of the ransomware in the US.
Fake Flash
The victim gets infected by installing a phony Adobe Flash installer that’s pushed to his or her machine when visiting one of the infected websites. That’s when Bad Rabbit starts to make its lateral movement in the victim’s network, using a set of default weak password combinations as well as the open-source Mimikatz to steal other passwords used by the infected machine. NotPetya also used that method to spread inside a victim’s network, but unlike NotPetya and the massive WannaCry ransomware campaign in May, Bad Rabbit spreads via the SMB protocol sans exploits.
Still unknown is what exploits were used to hack and inject malicious code into the watering hole websites. Researchers say they also aren’t sure if victims got their data and files back if they paid the attackers’ ransom.
“The dangerous aspect is the fact that it was able to infect many institutions which constitute critical infrastructure – subway, airport, as well as government institutions – in such a short timeframe, which indicates a well-coordinated attack,” ESET’s Leveille says.
Adding to the mystery, he says it’s also possible those targets were compromised prior to the ransomware attacks this week.
RiskIQ researchers, meanwhile, say while Bad Rabbit ransomware is a new animal, the attack campaign dates back to at least 2016. “Even though the BadRabbit ransomware is brand new, we can track the distribution vector back to early 2016 showing that victims were compromised long before the ransomware struck and the news cycle began. In fact, the campaign could have been originally built for something other than BadRabbit,” the company wrote.
Related Content:

Join Dark Reading LIVE for two days of practical cyber defense discussions. Learn from the industry’s most knowledgeable IT security experts. Check out the INsecurity agenda here.
![]()
Kelly Jackson Higgins is Executive Editor at DarkReading.com. She is an award-winning veteran technology and business journalist with more than two decades of experience in reporting and editing for various publications, including Network Computing, Secure Enterprise … View Full Bio
Article source: https://www.darkreading.com/endpoint/bad-rabbit-dies-down-but-questions-remain/d/d-id/1330224?_mc=rss_x_drr_edt_aud_dr_x_x-rss-simple