‘Bad Rabbit’ Ransomware Attacks Rock Russia, Ukraine
A wave of ransomware infections is hitting hundreds of government, media, transportation, and other targets in Eastern Europe today mainly in Russia and Ukraine, but also in Bulgaria, Germany, and Turkey.
Among the most high-profile targets thus far are major news outlets such as Russia’s Interfax Agency, and Ukraine’s Kiev Metro, its Odessa International Airport, and ministries of infrastructure and finance.
US-CERT said today that is has received “multiple reports” of Bad Rabbit infections from “many countries,” and says victims should not pay the ransom because it doesn’t guarantee the attackers will release the hijacked, locked-down data.
Ukraine was on alert for the attacks, as its Security Service and CERT earlier this month had warned of a possible large cyberattack akin to NotPetya to occur in conjuction with its Defender of Ukraine Day holiday.
Details about the attacks are trickling in as researchers drill down on the malware and its attack vectors, but researchers at ESET say the malware used in the Kiev Metro attack is Diskcoder.D, a new variant of the infamous Petya. The most recent version of Diskcoder was used in a ransomware campaign that spread around the world in June.
Researchers at Kaspersky Lab say the dispci.exe file found in the malware seems to originate from the code base of open-source encryption tool DiskCryptor, a legitimate tool for encrypting disk and system partitions. “It acts as the disk encryption module which also installs the modified bootloader and prevents the normal boot-up process of the infected machine,” Kaspersky researchers Orkhan Mamedov, Fedor Sinitsyn, and Anton Ivanov wrote in a blog post today.
They also noticed the attackers appear to be fans of “Game of Thrones,” based on code strings that include names of characters from the popular book and HBO series.
Although Bad Rabbit is a relatively widespread ransomware campaign, don’t expect it to be another WannaCry. Robert Lipovsky, senior malware researcher with security vendor ESET, which has been studying the attacks, says the ransomware campaign won’t likely spread like WannaCry did.
“Considering the infection capabilities we discovered in the samples, spreading outside Ukraine is theoretically possible but much less likely than in the June NotPetya case, due to the lack of EternalBlue spreading mechanism,” he says, referring to the SMB-worm style attack used in WannaCry to spread like wildfire around the globe.
Instead, Bad Rabbit employs hardcoded stolen credentials via SMB, first by remotely stealing passwords from infected machines via the Mimikatz password-extraction tool, and using a username/password list that’s hardcoded in the binary code.
There’s also a phony Adobe Flash Player connection: a dropper of Diskcoder.D that poses as a Flash Player installer. ESET spotted that on major news websites in Russia and Ukraine, Lipovsky notes. “While this may very well be an infection vector, it is doubtful that this was the main infection vector … and quite possibly a smokescreen.”
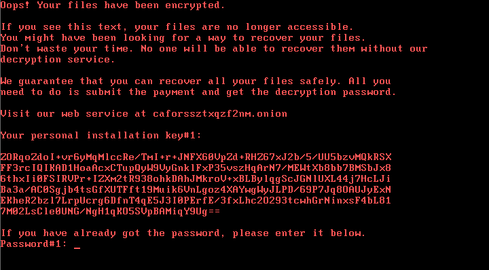
Bad Rabbit ransom message
Source: ESET
Researchers at Kaspersky say their telemetry shows a drive-by attack is the initial attack vector, and it’s a targeted attack campaign. “Our observations suggest that this been a targeted attack against corporate networks, using methods similar to those used during the ExPetr attack,” they say, referring to the June attacks.
“The ransomware dropper was distributed with the help of drive-by attacks. While the target is visiting a legitimate website, a malware dropper is being downloaded from the threat actor’s infrastructure,” according to Kaspersky. “No exploits were used, so the victim would have to manually execute the malware dropper, which pretends to be an Adobe Flash installer.”
Adam Meyers, vice president of intelligence at CrowdStrike, says Bad Rabbit appears to have been served up via the argumentiru.com website, a Russian and Eastern European news and celebrity gossip site. “CrowdStrike Intelligence can confirm that this website was hosting a malicious JavaScript inject as part of a Strategic Web Compromise (SWC) attack on 24 October 2017,” Meyers said in statement.
CrowdStrike also found more proof of a link to the NotPetya attackers: Bad Rabbit and NotPetya DLLs “share 67% of the same codebase, which makes it likely that the same threat actor is behind both attacks,” Meyers said in a tweet late today.
Related Content:
- 10 Social Engineering Attacks Your End Users Need to Know About
- Here Comes Locky, A Brand New Ransomware Threat
- Ransomware Authors Break New Ground With Petya
- NotPetya: How to Prep and Respond if You’re Hit

Join Dark Reading LIVE for two days of practical cyber defense discussions. Learn from the industry’s most knowledgeable IT security experts. Check out the INsecurity agenda here.
Kelly Jackson Higgins is Executive Editor at DarkReading.com. She is an award-winning veteran technology and business journalist with more than two decades of experience in reporting and editing for various publications, including Network Computing, Secure Enterprise … View Full Bio