Guess what?
It’s October, and that means it’s Cybersecurity Awareness Month.
In the US, it’s a big enough deal to be officially known as National Cybersecurity Awareness Month (NCSAM), and it started back in 2004 as “a collaborative effort between government and industry to ensure every American has the resources they need to stay safer and more secure online”.
In short, it’s not about pushing products, or crowing that your way of doing it is better than everyone else’s, or pulling off publicity stunts to promote a particular technology over all others.
For Naked Security, at least, it’s about presenting easily-digested articles that are plainly written, educational and, as far as possible, fun.
After all, computer security doesn’t have to be boring, doesn’t have to be awash in jargon, and doesn’t have to end up as a set of proscriptions and prohibitions.
So here are 3 simple steps to online safety that aren’t just clicking a button.
Each of these steps requires a little bit of commitment and some ongoing extra effort on your part…
…but although you might find them a hassle at first, we think you will soon consider them second nature.
The theme for Week 1 of NCSAM is STOP. THINK. CONNECT: Simple steps to online safety.
All our steps will quite literally make you STOP and THINK before you CONNECT, thus increasing your advantage over the cybercrooks.
#CYBERAWARE STEP 1
TRY 2FA WHEREVER YOU CAN
As you probably know, 2FA is short for two-factor authentication, also known as two-step verification or 2SV.
Typically, 2FA works by asking you for your regular password, which is the same every time, and then asking you for a one-time code that is calculated by, or sent as a text message to, your phone.
2FA isn’t foolproof – the crooks could steal your phone, booby-trap the code generation app using malware, or swap out your SIM card and intercept the messages – but it does make things harder for the crooks.
In particular, they can no longer steal your password today and use it again and again for hours, days or weeks.
The downside, and we’ll be honest here, is that 2FA isn’t as convenient as just using a password, at least for what you might consider your “less important” accounts that you use a lot.
If you leave your phone at home, you probably won’t be able to login from your laptop at the coffee shop.
Also, logging in takes a bit longer, every time, and there are more things to go wrong that could keep you out of your account.
So, 2FA is indeed a simple step to online safety, but it isn’t a one-off action: it adds an extra step to every login, so you have to change your login procees – what time management and user interface experts like to call “workflow”.
But we think the effort is worth it, and we encourage you to try 2FA wherever you can.
If you really can’t get on with it, you can always turn it off, but give it a fair go first.
#CYBERAWARE STEP 2
TRY THE LONGEST MOBILE PHONE LOCKCODE YOU CAN MANAGE
Back in 2015, Apple upped the shortest permitted lockcode for iPhones from four digits to six.
That’s because adding two digits doesn’t increase the number of different codes by 50% (6 digits / 4 digits = 1.5 = 150%), but takes you from 10×10×10×10 codes (10,000) to 106 (1 million), a 100-fold boost in complexity.
We suggest upping your lockcode even further, say to 10 digits, even though it’s harder to memorise to start with, and takes longer to type in every time.
Although 10-digit codes take 2.5 times longer to type in than 4-digit codes – let’s say close to three seconds instead of about one second – they are, at least in theory, a cool one million times more secure. (The arithmetic here is 10/4 = 2.5, but 1010/104 = 1,000,000.)
That means that it’s easier to pick something unique and hard to guess, and harder for crooks – or for your oh-so-witty friends who are dying to send out off-colour tweets in your name – to shoulder-surf by watching you typing in your code out of the corner of their eye.
We think the effort is worth it, and we encourage you to increase the length of your lockcode as much as you can.
If you’re worried about forgetting your new, superlong code and being faced with resetting your phone and losing any data you haven’t yet backed up, consider writing down the new code and locking it away at home until you’re happy you’ve mastered the new finger pattern.
#CYBERAWARE STEP 3
TRY LOGGING OUT FROM APPS YOU’RE NOT USING
Have you ever retweeted something without realising it, or Liked something on Facebook without meaning to?
Have you realised your blunder only when your friends started pestering you to find out when you adopted your new and uncharacteristic political opinions, or when you fell in love with a certain Mr J. Bieber? (Those are rhetorical questions. You don’t need to answer.)
The problem is that social networks put a lot of effort into what they call frictionlessness, so that it’s as easy as possible – and sometimes much too easy, especially when you are somewhat lubricated yourself – to participate in online discussions at a moment’s notice.
Ironically, you may find – if you have made more than your fair share of online faux pas – that you can make your social networking life a lot easier, or at least a lot less prone to blunders, by making its operation a bit more difficult.
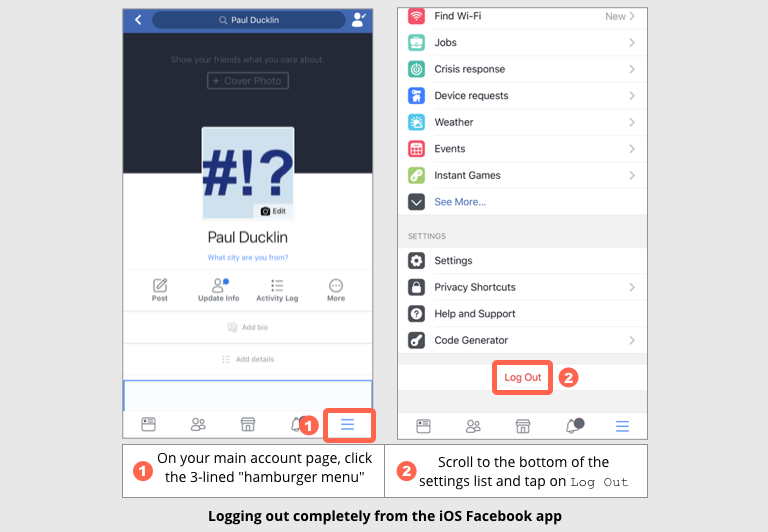
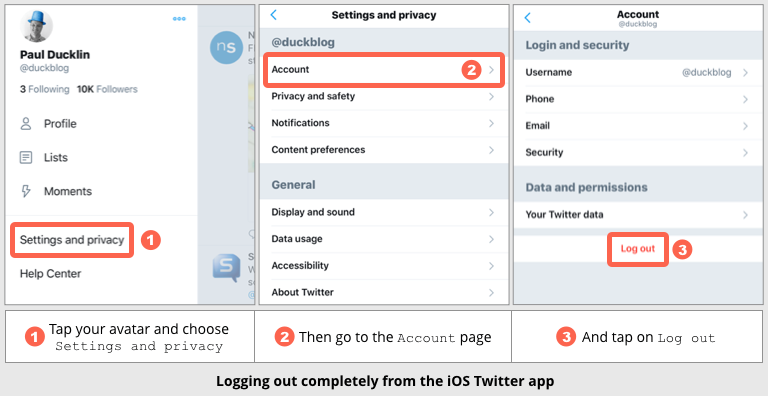
We suggest learning how to log out fully from services such as Twitter and Facebook, especially on your phone, where simply closing the app is not enough.
It means logging back in every time you start up the app or load the website again, which is mildly annoying at first.
But it means you’ll be much less likely to share something unintentionally, which will not only protect your friends from scams apparently “approved” by you, but also protect you from what could turn into career-limiting moves.
We think the effort is worth it, and we encourage you to learn to logout regularly.
Admittedly, for all that this is a simple step in theory, it’s irritating to get right in practice, because each social media app seems to have its own way of handling the logout function, and it isn’t always obvious where to find it.
Try looking for a “hamburger menu” (see below) on your main account page, or follow your nose to setup pages labelled Settings or Account.
To give you a hint of where to start and where in each app to go digging, here’s how to do it in the iOS versions of Facebook and Twitter:
There you have it.
As we said above, you might consider these steps a bit of a hassle at first, but that we think you will soon consider them second nature.
In fact, you might soon find yourself uncomfortable without them, like driving without a seatbelt or riding without a helmet.
Remember: STOP. THINK. And only then CONNECT.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/-hsAW_xR6IU/







