China’s censorship cyber-missiles shoot down pics flying through WhatsApp, chat apps
China has expanded its censorship tools to strip out images from chat messages in transit through its networks.
The new powers were inadvertently demonstrated on the country’s most common messaging services – WeChat and Weibo – following the death of Nobel Peace Prize winner Liu Xiaobo last week. The superpower’s Great Firewall was also able to clumsily disrupt photos and texts sent via Facebook’s WhatsApp service.
Netizens in China reported the immediate deletion or blocking of references to Liu Xiaobo, who died at a hospital in Jinzhou in the north west part of the country from liver cancer. He had been held as a political prisoner for over eight years, and the Chinese government refused a request for him to seek medical attention overseas.
Concerned that his death could lead to political protest, Chinese censors went into overdrive, using keywords to try to remove any mention or discussion of Xiaobo from WeChat, Weibo, and other Chinese services. A review of that censorship by the University of Toronto’s The Citizen Lab revealed a depth of sophistication and hitherto unknown censorship capabilities.
To be clear, we’re told that censors were able to peer into private conversations on Chinese services, and strip out any banned material as it moved from person to person. For foreign services, such as the encrypted WhatsApp, they were only able to block all large messages or simply firewall off whole systems in a ham-fisted way.
Regarding the Chinese chat portals, Citizen Lab reported this week that the Middle Kingdom’s expurgators had…
- The ability to discern and apply different blocking rules based on whether chats were one-to-one or to a group (groups chats were more heavily censored).
- The ability to understand context and apply differing degrees of censorship depending on how many and what types of blocked keywords were included in a message.
- The power to perform server-side blocking of messages, meaning that people didn’t even see messages intended for them.
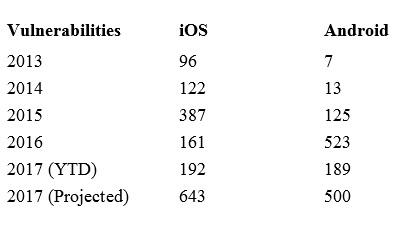
But the most surprising new capacity was the ability to remove images in transit. Chinese users have grown used to having their images removed, and have learned a variety of techniques, including rotating images, as a way of passing its legion of censors. But images sent on messaging apps have typically made their way through and been deleted later.
Obviously concerned that pictures of Liu Xiaobo in a hospital bed could become widely shared, or even iconic, the authorities demonstrated their ability to intervene mid-transit and many images of the activist never made it beyond individuals’ phones.
“We found 74 images blocked on WeChat Moments, 26 blocked on group chat and 19 blocked on one-to-one chat,” The Citizen Lab reported. “These are the first tests in which we have found evidence of image censorship on WeChat’s one-to-one chat.”
The difference in numbers is directly connected to how large the public reach of each service is. “The blocking of images on one-to-one chat shows an effort to restrict content across semi-public and private chat functions, demonstrating the sensitivity of Liu Xiaobo’s death,” the researchers noted.
One of the banned images
The outlawed snaps include everything from pictures of Liu Xiaobo in hospital, to simplified cartoon-like images of him using his glasses as a frame of reference, to screengrabs showing censorship, to people commemorating him. In short, anything that appears to strike a chord and started being shared widely was immediately blocked, demonstrating both the depth and the resources applied to censoring citizens’ communications.
It is notable, however, that the Chinese government was only able to shoot down specific images on the chat apps based in China – strongly suggesting that the government has access to the company’s backend systems. When it came to Facebook’s end-to-end encrypted WhatsApp messaging service, the government reacted by simply blocking the sending of any and all images and video – presumably by stopping all attachments from being delivered rather than cracking and inspecting conversations. Some users reported that WhatsApp wasn’t working at all for them, but many reported that text messaging was working fine while all images were being dropped.
WhatsApp uses the strongly encrypted Signal protocol. Attachments, such as pics and videos, are scrambled and transferred via a blob store [PDF] – and it could be this process that the Great Firewall of China disrupted to stop photos getting through, rather than decrypting the contents.
In terms of keywords, Liu Xiaobo’s name in both English and Simplified Chinese were blocked online, as was mention of his wife Liu Xia. A strongly blocked phrase remains “Charter 08” – which was the manifesto he wrote back in 2008 arguing for political reform, and which led to his arrest and imprisonment. Others included “Nobel Peace Prize,” “liver cancer,” any reference to his death or condition and the phrase “wash the guilt.”
In the past six months, China has expanded its already extensive censorship systems to cover not just politically sensitive topics, but also issues that the central government does not approve of, including homosexuality and drug use.
Earlier this month, the government also started cracking down on “unlicensed” VPN services that many citizens have used for years to circumvent the online controls. VPN providers will now be expected to block a government-supplied list of websites and services if they wish to operate in the country. ®
Article source: http://go.theregister.com/feed/www.theregister.co.uk/2017/07/18/china_censorship_includes_images_in_transit/
 Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the
Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the  Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the
Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the