A new report has found that 41% of Americans have personally experienced online harassment, 66% have seen it directed to others, and 62% consider it a major problem.
The Pew Research Center survey of 4,248 US adults shows that the number has crept up since the center last did a study of this type in 2014. Three years ago, 35% of all adults had experienced some form of online harassment.
Some of the trollery is just part of online life: something we can ignore or shrug off, such as name-calling or attempts to embarrass us.
But nearly one in five Americans – 18% – have been recipients of the truly nasty, be it threats of violence, sustained harassment, sexual harassment or stalking.
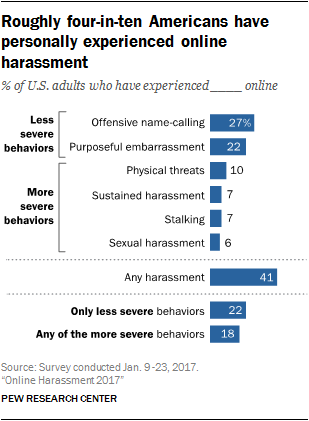
From the report:
At its most severe, it can compromise users’ privacy, force them to choose when and where to participate online, or even pose a threat to their physical safety.
When asked who should clean up the mess, be it with policing or policies, Americans mostly point to online companies and platforms. Only 15% of respondents didn’t think that online services should be held responsible for users’ behavior or content, compared with 79% who think they should.
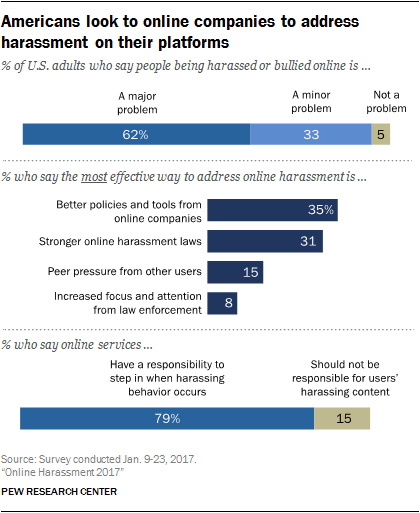
Then again, a majority of Americans – 60% – think we’re all on the hook when it comes to sticking up for each other in the face of harassment. Another 15% said that peer pressure is the single most effective way to address online harassment. Many think police should also be involved: 49% think law enforcement should play a major role in addressing online harassment, and 31% say stronger laws are the single-most effective way to address this issue.
But as Twitter and other social media platforms well know, it’s frustratingly difficult to balance the right to free speech with people’s rights to feel safe and welcome online.
Men are somewhat more likely to be harassed online – 44% of men and 37% of women say they’ve been harassed. Men are also modestly more prone to being called offensive names (30% vs. 23%) or receiving physical threats (12% vs. 8%).
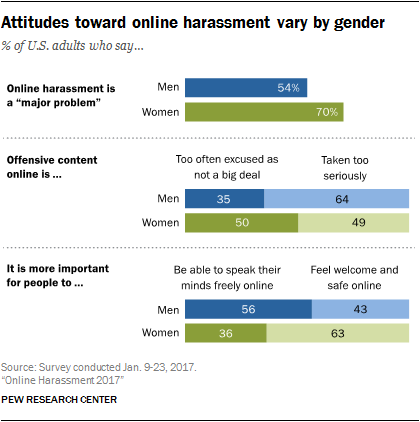
But women are far more likely to be abused on sexual terms. Some 21% of women ages 18 to 29 report being sexually harassed online: more than double the share among men in the same age group (9%). Meanwhile, 53% of young women – aged between 18 and 29 – report that someone has sent them explicit images they didn’t ask for. Women are also more shaken by their online abuse: 35% of women who have experienced any type of online harassment describe their most recent incident as either extremely or very upsetting, which is about twice the share among men (16%).
Differences in opinion on which is more important – free expression or freedom from abuse – vary significantly by gender. Most women – 63% – say people should be able to feel welcome and safe in online spaces, compared to 43% of men. Men are also much more likely than women to say that people should be able to speak their minds freely online (56% of men vs. 36% of women).
The study quoted women on what gender-based harassment looks like:
Any woman who has an opinion online is bound to get men who through anonymity feel the need to threaten and assault them. I had a friend who got a stalker from posting a political Facebook post.
Usually men harassing or threatening females for posting any provocative pictures or an opinion different from his own.
Sexual harassment, extreme name-calling, taking sexual abuse I went through and broadcasting it in such a way that I was asking for what happened to me, more lies, that I am an immodest woman for breastfeeding my daughter…
Mostly on dating websites my friends have had experiences where once turned down, men threaten to beat and rape them, murder them, call them names, threaten to ruin their reputation, etc. I have never used a dating website because of what I have seen.
The most recent US election has spawned its own wave of vitriol. The report cited these people’s testimony:
People who expressed negative feelings or posted negative content toward Donald Trump were called derogatory or obscene names.
Liberals calling foul things to those who support Trump. Using profane language calling supporters ‘racists, bigots and f****** conservatives.’
I got into a political debate and the person did not agree with me. They threatened to find information about me and make it go viral. After I called them a troll they threatened to physically harm me.
I made a comment regarding the recent presidential election and was called many names and stereotypes regarding my race.
Non-Caucasians are also common targets. One in four of all black adults and 10% of Hispanics have experienced harassment online as a result of their race or ethnicity; just 3% of whites say it’s happened to them.
Their voices:
A talk about police killings of unarmed black people turned into a full-on verbal assault with racial slurs being hurled at the people who opposed the police killings.
My friend is a reporter for a major publication, and I have seen the racist threats made both in the comments section and DMs [direct messages] (she’s Jewish, so stuff about gas chambers and concentration camps). I’ve seen people be doxxed in public forums, violent threats in the comment sections and forums like Reddit, etc., etc.
I told a group discussion that I thought that the group should have more compassion for the immigrant children. A woman went off about my background and my father’s background, and she made references to finding me and ‘taking care’ of me, which I took as a threat.
Men have a tendency to shrug these things off. While half of women say offensive content online is too often excused as not being a big deal, 64% of men – and 73% of men aged between 18 and 29 – say that many people take offensive content online too seriously. Further, 70% of women – and 83% of women aged 18 to 29 – view online harassment as a major problem, while 54% of men and 55% of young men feel that way.
Political views, physical appearance, gender and race are among the top reasons people say they’re harassed online. The young are particularly vulnerable: 67% of young adults have been harassed, with 41% having experienced severe harassment.
What can we do?
As the report points out, the Communications Decency Act of 1996 holds that online hosts aren’t legally responsible for the content users post on their platforms. Americans still expect them to take care of the problem of online harrassment, though: 79% feel that online services have a responsibility to step in when harassing behavior occurs on their sites.
Twitter, for one, has been trying, over the course of years, to do just that. Back in February 2015, Twitter’s then-CEO Dick Costolo didn’t mince words: he said flat-out in internal memos that the company sucked at dealing with trolls and abuse, that it had sucked at it for years, and that it was about time that it changed.
Twitter’s most recent move, announced earlier this week: new tools to silence the trolls who barge into people’s notifications with seething replies or obnoxious user names. The options enable you to mute notifications from newly registered accounts, people you don’t follow, and people who don’t follow you. The advanced filters can be configured in the Notifications – Settings – Advanced Filters section of Twitter.
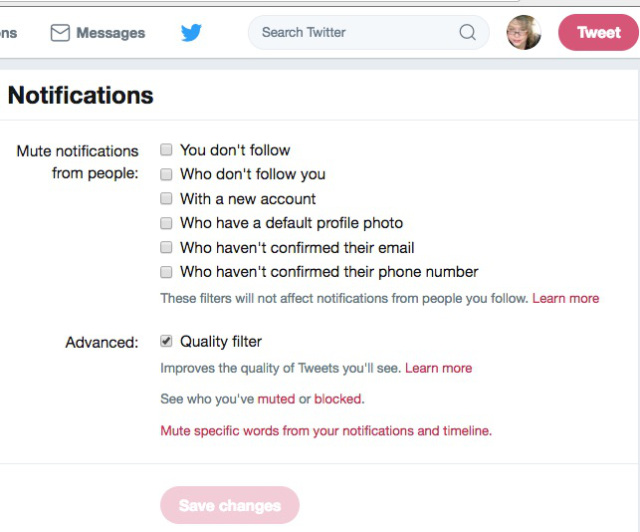
As one Twitter user noted, the advanced filters won’t erase trollery or abusive behavior, but they’ll at least turn down the volume.
Twitter isn’t the only one with a troll problem, and it’s far from the only online platform trying to flush out vitriol while simultaneously expressing fealty to the notion that users have a right to freely express themselves.
And as we reported in May, there are plenty of governments who’d be happy to step in and help the platforms figure it all out.
The European Union is on the brink of forcing Facebook, YouTube, Twitter and other social media companies to block videos with hate speech.
The European Council – which sets the EU’s political direction and priorities – in May approved a set of proposals that would require such companies to block videos that promote terrorism, incite hatred, or contain toxic, violent content.
Granted, hate speech is a specific type of content. Targeting individuals, in contrast, is a behavior, and harassing behavior might best be addressed by laws tailored to penalize the specific behaviors involved, be it the posting of nonconsensual/revenge porn, threats of rape or other physical harm, racist slurs, stalking or any of the other myriad illegal threats posed by online abusers.
Readers, your thoughts? Do you think we should all grow a thicker hide and just accept that the internet will never be a welcome, safe place for all?
Or do you expect, and demand, that platforms, police and individuals do more to stop online abuse? If so, what should they do that they’re not already doing?
Please share your suggestions in the comments section below.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/EbzmroZBypQ/




 Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the
Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the  Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the
Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the  Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the
Black Hat USA returns to the fabulous Mandalay Bay in Las Vegas, Nevada, July 22-27, 2017. Click for information on the