Attackers continue to use Office exploits to proliferate malware, and SophosLabs has traced the activity to three popular exploit builders.
We described the first two – Microsoft Word Intruder and Ancalog Builder – in earlier papers. A new paper released today examines the third one: AKBuilder.
AKBuilder generates malicious Word documents, all in Rich Text, according to the paper’s author, SophosLabs principal researcher Gábor Szappanos. Once purchased, malicious actors use it to package malware samples into booby-trapped documents they can then spam out.
Like its two cousins, AKBuilder uses exploits to deliberately corrupt files that automatically trigger bugs in Office and underlying bugs in Windows itself.
AKBuilder is advertised in YouTube videos and sold in underground forums. The kit usually costs around $550 (payable in electronic currencies like Bitcoin and Perfect Money). Here’s an example (click to enlarge):
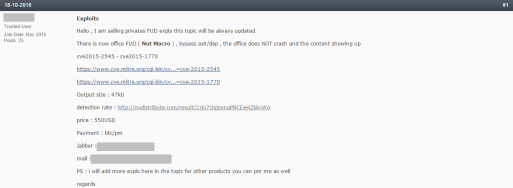
AKBuilder anatomy
Szappanos wrote about two variations of the kit, which are differentiated by the Office vulnerabilities they target. The earlier version, AK-1, uses two exploits in the same document: CVE-2012-0158 and CVE-2014-1761. The newer version, AK-2, uses a single exploit: CVE-2015-1641.
Both versions are released as a Python script. Everything is hardcoded and there is no configurable option apart from the file names, Szappanos wrote.
The script takes three parameters. The first parameter is the name of the payload file, the second is the name of the decoy document, and the final is the name of the generated exploit document.
All of the known builders have the same rough structure. The hardcoded exploit block with first- and second-stage shellcodes are stored as a huge data block in the script (click to enlarge):
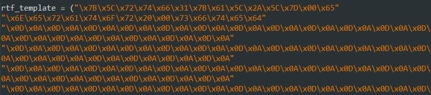
The encrypted payload and decoy files are appended after the template content. This is a very rigid structure, an update to make any modification. The beginnings of the generated files up to the embedded payload are identical.
This can only serve as the “release build” of the builder. The script contains the entire document as a single block of data. This block is often modified by the author to avoid detection by antivirus engines. The modifications, though they could be done manually, are more likely done by an internal tool owned (and not released) by the author. This internal tool generates the highly obfuscated exploit document, which is then packaged in the Python script.
The kit is used by various cybercrime groups, distributing dozens of different malware families. The most active (or least careful) of these criminals are Nigerian BEC groups.
AK-1- and AK-2-generated documents are detected by Sophos as Troj/20141761-F , Troj/DocDrop-FK or Troj/DocDrop-JK.
Lifecycle
AK-1 was most active between the middle of 2015 and 2016. The emergence of its successor AK-2 seemed to spell the end of the kit’s lifespan. By the summer of 2016, it seemed extinct.
But we recently started to observe a resurrection of AK-1 samples. Szappanos said it’s too early to speculate, but thinks it can be associated with the disappearance of the Ancalog builder.
There was a significant market gap that needed the older Office exploits provided by AK-1, and when there is a need, there is a solution.
AK-2
Szappanos wrote about the characteristics of this kit back in a research paper published on Naked Security last year.
Like its predecessor, we are not aware of other public reports related to this exploit kit, thus, we have no official name for it.
The source code of the builder is based on the AK-1 builder Python script and it shows the same characteristics.
Distributed malware
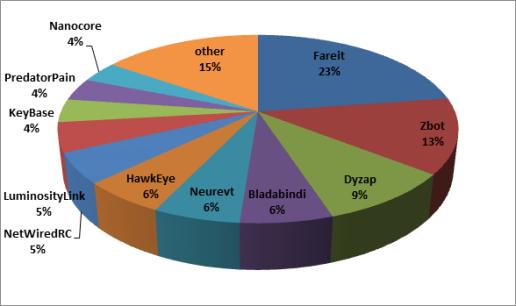
SophosLabs identified about 760 malicious documents generated by AK-1, which were used to distribute more than 50 different malware families.
In its heyday, the most popular Trojans (Zbot, Chisburg, Fareit, Neurevt) were favored, but with the appearance of AK-2 these variants have slowed down somewhat. It appears a few diehard groups are still using the older version of the kit, but they are mostly deploying the PredatorPain keylogger (which is the most frequent benefiter of the kit) and the NetWiredRC backdoor.
The following chart shows the malware families distributed by AK-1 and AK-2:
Attribution
In case of AKBuilder, it is hard to tell how many individuals or groups are working on it. Because it is a simple Python script, it is very easy to steal the builder and start a new “development branch”. It is quite possible that the work was started by a single individual, and then others jumped in and stole the code, releasing their own versions.
It is clear though that the known builder versions come from the same origin and could be considered as belonging to the same development branch even though there are multiple email accounts connected to it.
Some of the distributors (including the most persistent one) are seemingly from the Arabic regions. There is no proof that there is any connection between them, though.
But apart from them, there are a handful of other, seemingly unrelated developers/distributors who sell versions of this kit. We suspect that most of them work independently, purchasing one version of the kit, then modifying and distributing it on their own. Some of them distribute only this kit, others seem to be involved in selling a wide range of malicious software builders.
This is possible because the release version of the kit is written in Python which makes it easy to understand and modify.
SophosLabs believes there are about half a dozen individuals who are involved in developing and distributing AKBuilder, but the exact connections between them is less clear.
Conclusion and defensive measures
Cyber-criminals find Office documents useful for delivering malicious programs to their targets. They’ve been using this method steadily over the past two years, and there is no sign that they intend to give up.
The availability of black-market tools makes it possible for a wide range of criminals to generate the exploited documents. After the disappearance of the Ancalog builder, AKBuilder took over as the most popular choice of these tools.
The rigid hard-coded structure of AKBuilder means that for any change in the generated samples, a new version must be released. That information helps the defenders: even if the first few samples go undetected, a quick signature update can protect the users for days or even weeks.
The dependence of criminals on the commercial offerings has a disadvantage for them: the builder doesn’t use zero-day exploits or even exploits that could be considered as new.
AKBuilder shows a moderate progressiveness: new exploits like CVE-2014-1761 and CVE-2015-1641 are supported relatively fast after their first availability. But the kit is far from using zero-day exploits, in both cases the first use of the exploit was months after the vulnerability was disclosed and the patch made available.
In the final analysis, it shouldn’t be difficult to protect against these kinds of activities: just applying recent patches for Microsoft Office should disarm the attack.
Article source: http://feedproxy.google.com/~r/nakedsecurity/~3/z3Iu4FjuOhU/



